Enable password login
Note: This page applies to SFTP Gateway version 2.x. Visit Here for documentation on version 3.x.
Overview
By default, SFTP users are configured with SSH key authentication. This is more secure than passwords because the password is never sent over the wire.
End users might not be comfortable with SSH key authentication. So in these situations, you may need to configure an SFTP user with password authentication.
In previous versions of SFTP Gateway, configuring password authentication required complicated command line syntax. But in SFTP Gateway version 2.001.00, you can now set passwords in the web admin UI.
Use the web admin UI to set passwords
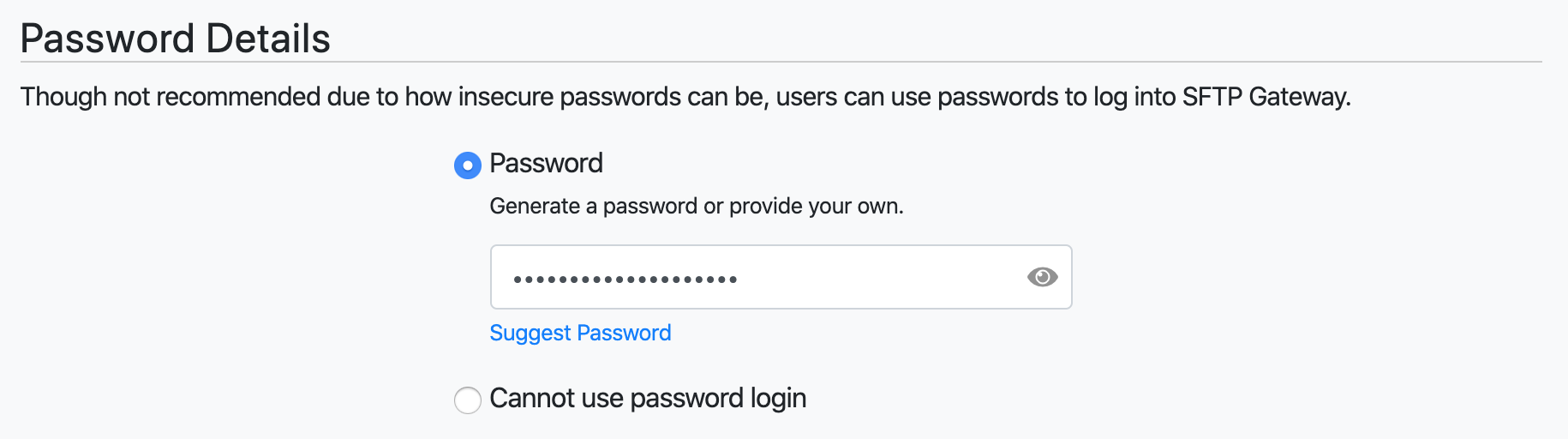
When creating or editing an SFTP user account, you should see a Password Details section.
By default, the radio button is set to Cannot user password login.
Select the Password radio button. This will reveal a form field where you can set the password.
 .
.
To apply your changes, scroll to the bottom and click Save.