SFTP Gateway 3.0 Beta Instructions
Overview
This page is to walk you through setting up the SFTP Gateway beta.
Before you begin, make sure you have completed the pre-requisites.
Pre-requisites
In order to participate in the beta, you need to email support@thorntech.com with the following information:
- Your AWS account ID
- Your preferred region for testing (e.g.
us-east-1)
We will share our beta AMI with your AWS account ID, and clone it into your region if necessary.
We will then email you the latest AMI ID, and remind you which region this AMI lives in.
Spin up the CloudFormation stack
In the AWS console, go to the CloudFormation service.
Click Create stack > With new resources (standard)
Under Specify template, choose Upload a template file
The file you want to upload is the CloudFormation template found at the bottom of this article. Create this file from scratch, and paste in the yaml code.
Fill in the following CloudFormation parameters:
- EC2 Type: Leave this as the default, which is
t3.medium. This is a cheap instance size for testing. - Disk Volume Size: Leave this as the default, which is 32 (GB). This is enough for testing.
- Key Pair: Choose a key pair that you have access to. Otherwise, create a new one, and return to this page.
- AMI ID: Paste in the AMI ID that we provide you.
- VPC: Choose the default VPC, which is
172.31.0.0/16 - Subnet ID: Choose one of the default subnets (e.g.
172.31.0.0/20) - Input CIDR: Enter your computer's IP address, followed by
/32.
Accept the defaults for the next few pages in the CloudFormation wizard.
On the last page, check the box for I acknowledge that AWS CloudFormation might create IAM resources. You are prompted with this warning, because our CloudFormation template creates an IAM role.
Click Create stack
Wait roughly 10 minutes. If all goes well, you should see a CREATE_COMPLETE status.
First launch experience for SFTP Gateway
The first time you launch SFTP Gateway, you need to configure the web admin account via the website.
In CloudFormation, click on the Outputs tab to get the EC2 instance's public IP.
Paste the IP address in a web browser.
You will see an SSL warning from the auto-generated self-signed certificate. Click Advanced and Proceed to get past the warning.
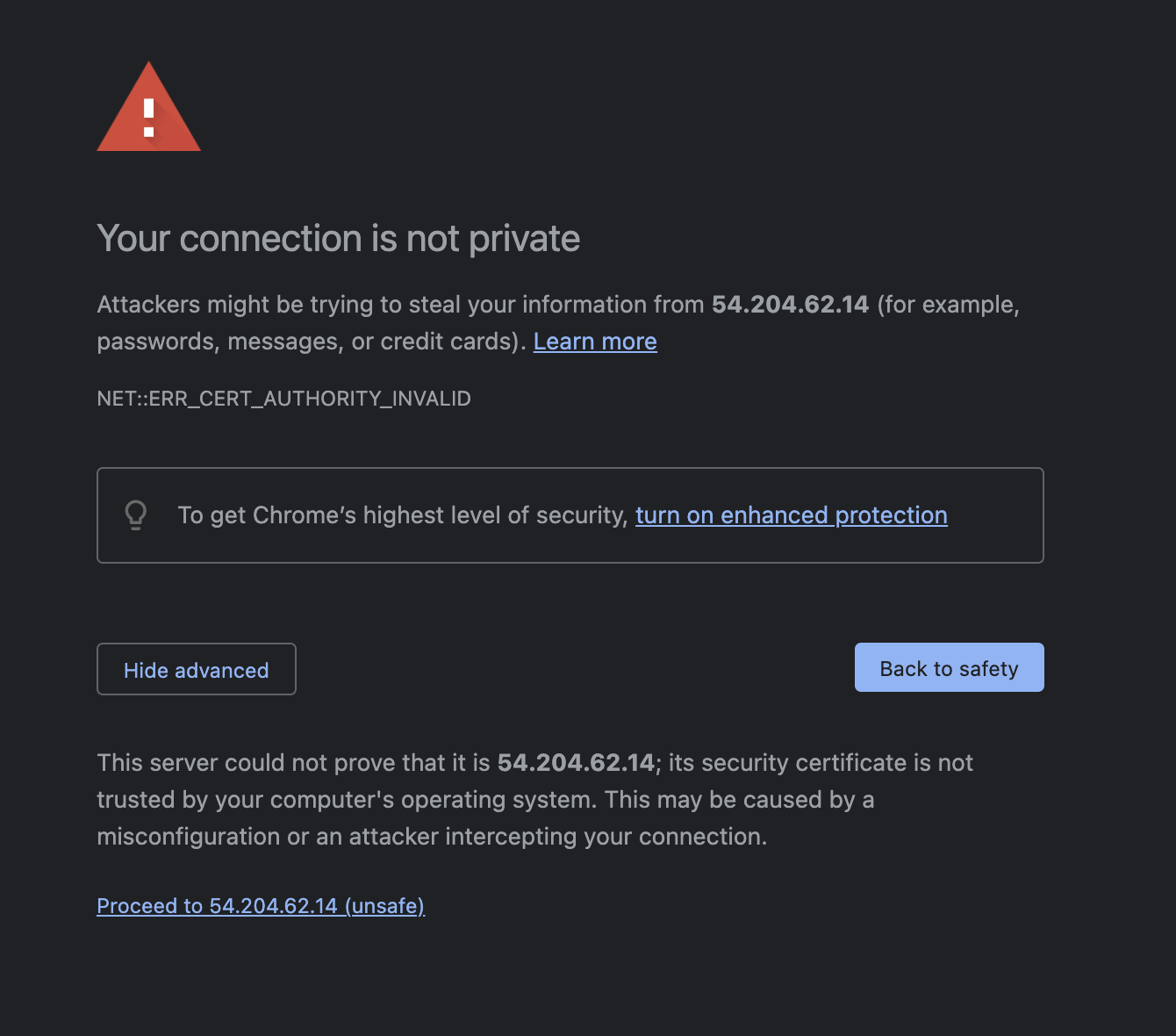
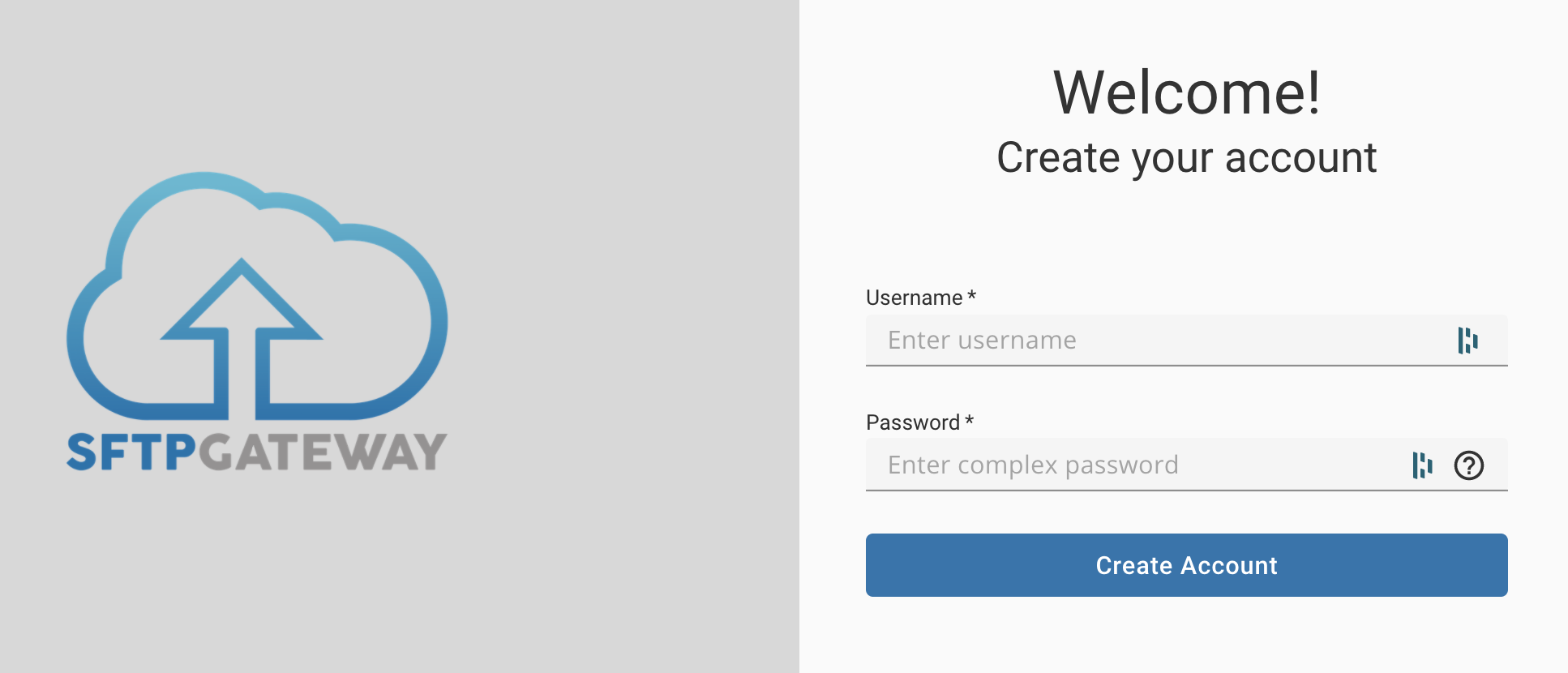
On the welcome screen, create an admin user. Enter a username and password, and then click Create Account.
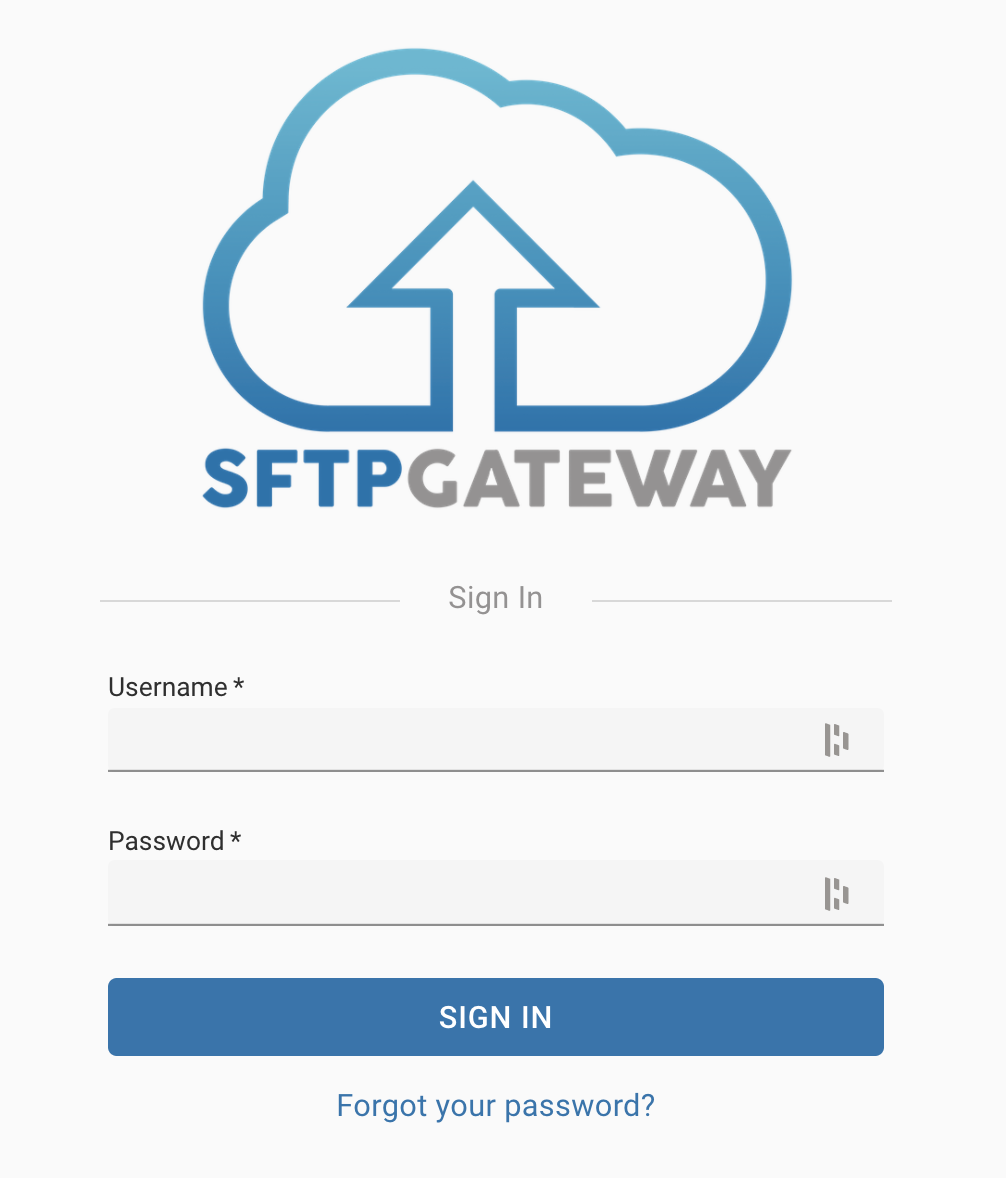
After creating the admin account, you can log into the web admin UI.
Create an SFTP user
In this section, you will create a new SFTP user.
Once you are logged in, you should see this screen:
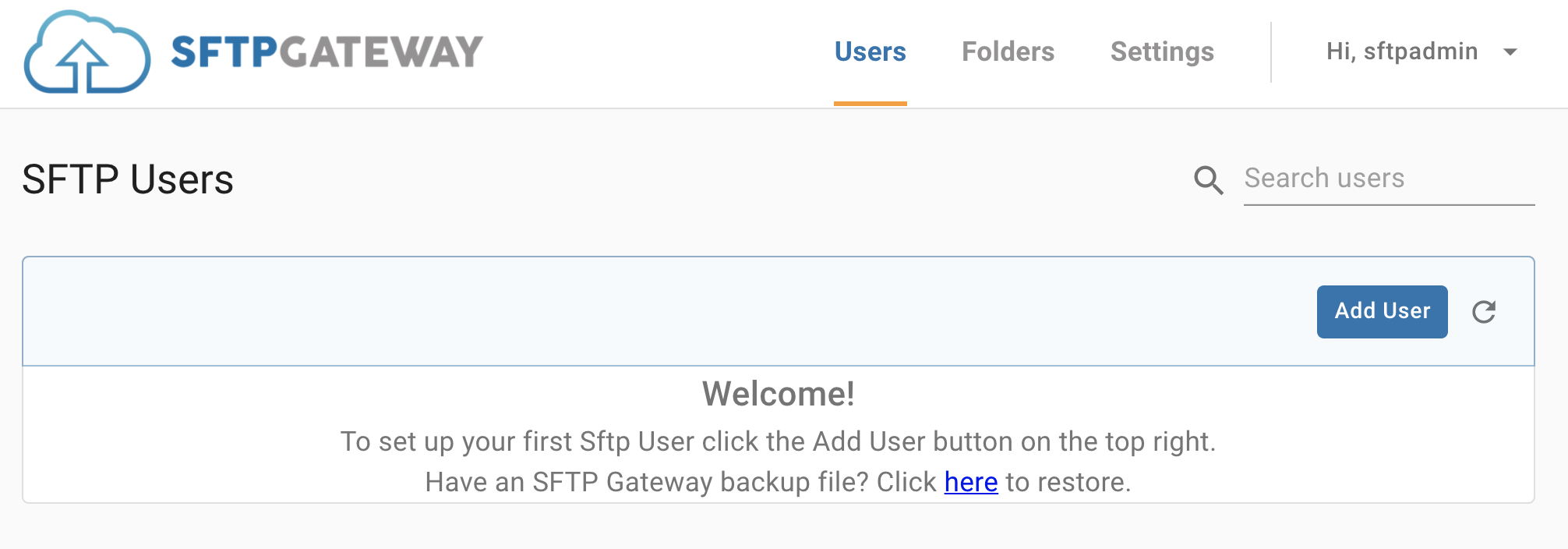
Click Add User
Enter a username (e.g. robtest)
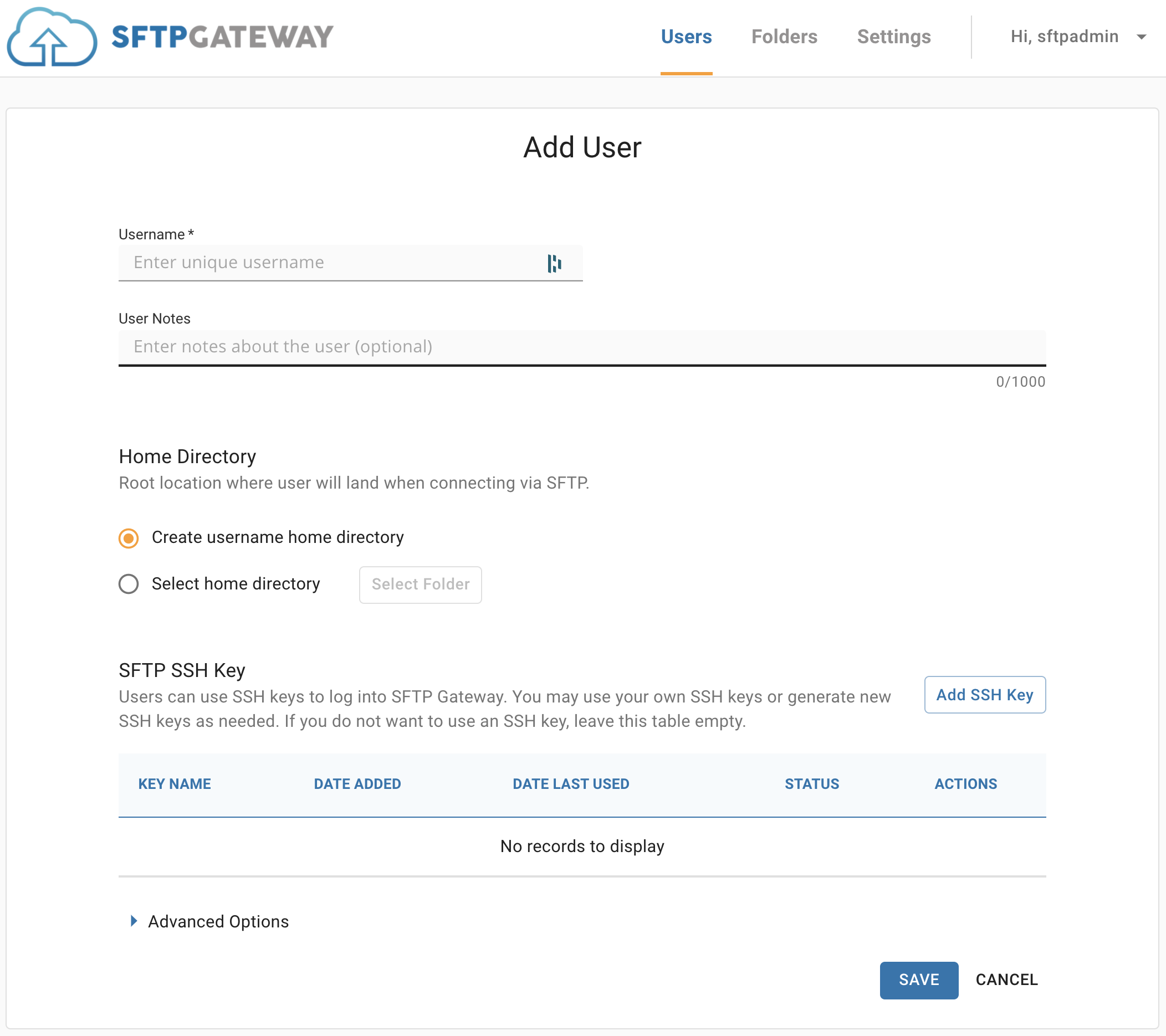
Scroll down and expand the Advanced Options.
Choose New Password, and set a password.
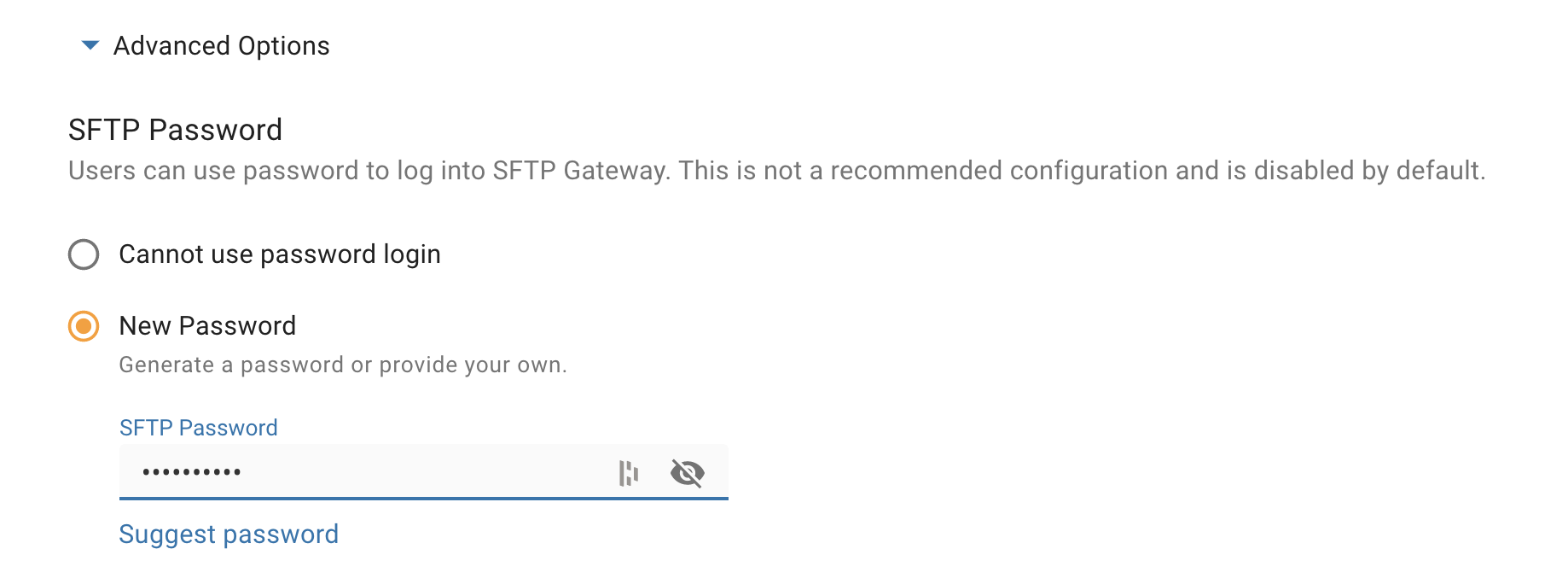
Scroll to the bottom, and click Save
Test the SFTP account
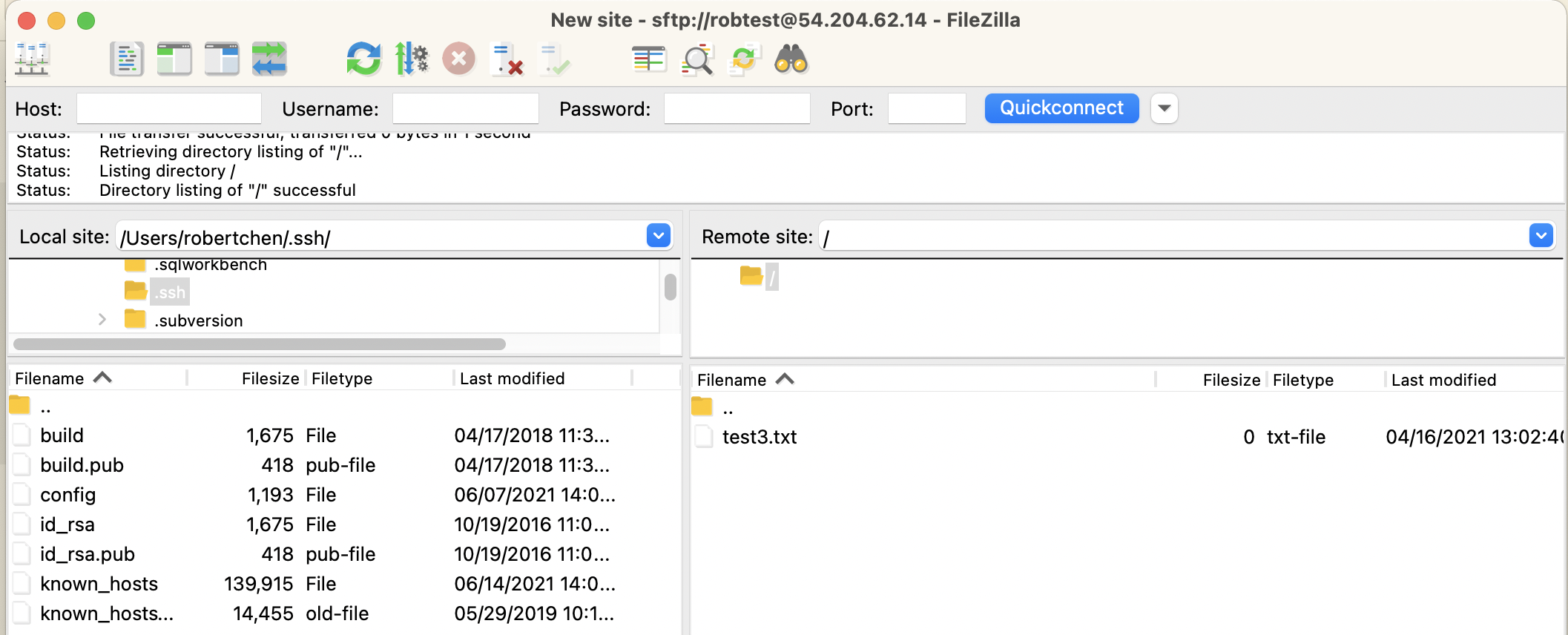
In this section, you will connect as the SFTP user via a client such as FileZilla.
You will need the following connection settings:
- Host: This is the public IP address of the EC2 instance
- Port:
22 - User: Use the SFTP username you just created
- Password: Use the password you just set
When prompted to trust the server host key, click OK.
Once connected, drop a test file in your SFTP directory.
Verify the file exists in S3
In this section, you will verify that the test file you uploaded exists in S3.
Open the AWS console, and open the S3 service.
On the list of S3 buckets, sort them reverse chronologically by creation date.
SFTP Gateway creates a new S3 bucket, based on the EC2 instance ID (e.g. sftpgw-i-0d6d5009eef240a64)
Click on the S3 bucket. You should see the following file:
users/robtest/test3.txt
The CloudFormation template
This is the CloudFormation template you will use to provision the SFTP Gateway stack.
Copy the contents into a new file on your computer.
AWSTemplateFormatVersion: 2010-09-09
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: Bucket
Parameters:
- BucketAccess
- Label:
default: Instance and storage options
Parameters:
- EC2Type
- DiskVolumeSize
- KeyPair
- AMIID
- Label:
default: Network
Parameters:
- VPC
- SubnetID
- Label:
default: Access and authentication
Parameters:
- InputCIDR
Parameters:
AMIID:
Type: String
Description: AMI ID
EC2Type:
Description: SFTP Gateway instance type. You can use a t3.medium for testing, but m5.large is recommended for Production.
Type: String
Default: t3.medium
AllowedValues:
- t2.micro
- t2.small
- t2.medium
- t2.large
- t2.xlarge
- t2.2xlarge
- t3.micro
- t3.small
- t3.medium
- t3.large
- t3.xlarge
- t3.2xlarge
- m3.medium
- m3.large
- m3.xlarge
- m3.2xlarge
- m4.large
- m4.xlarge
- m4.2xlarge
- m4.4xlarge
- m4.10xlarge
- m4.16xlarge
- m5.large
- m5.xlarge
- m5.2xlarge
- m5.4xlarge
- m5.12xlarge
- m5.24xlarge
- c3.large
- c3.xlarge
- c3.2xlarge
- c3.4xlarge
- c3.8xlarge
- c4.large
- c4.xlarge
- c4.2xlarge
- c4.4xlarge
- c4.8xlarge
- c5.large
- c5.xlarge
- c5.2xlarge
- c5.4xlarge
- c5.9xlarge
- c5.18xlarge
- f1.2xlarge
- f1.16xlarge
- g2.2xlarge
- g2.8xlarge
- g3.4xlarge
- g3.8xlarge
- g3.16xlarge
- p2.xlarge
- p2.8xlarge
- p2.16xlarge
- p3.2xlarge
- p3.8xlarge
- p3.16xlarge
- cr1.8xlarge
- r3.large
- r3.xlarge
- r3.2xlarge
- r3.4xlarge
- r3.8xlarge
- r4.large
- r4.xlarge
- r4.2xlarge
- r4.4xlarge
- r4.8xlarge
- r4.16xlarge
- r5.large
- r5.xlarge
- r5.2xlarge
- r5.4xlarge
- r5.12xlarge
- r5.24xlarge
- r5d.large
- r5d.xlarge
- r5d.2xlarge
- r5d.4xlarge
- r5d.12xlarge
- r5d.24xlarge
- z1d.large
- z1d.xlarge
- z1d.2xlarge
- z1d.3xlarge
- z1d.6xlarge
- z1d.12xlarge
- x1.16xlarge
- x1.32xlarge
- x1e.xlarge
- x1e.2xlarge
- x1e.4xlarge
- x1e.8xlarge
- x1e.16xlarge
- x1e.32xlarge
- i2.xlarge
- i2.2xlarge
- i2.4xlarge
- i2.8xlarge
- i3.large
- i3.xlarge
- i3.2xlarge
- i3.4xlarge
- i3.8xlarge
- i3.16xlarge
- h1.2xlarge
- h1.4xlarge
- h1.8xlarge
- h1.16xlarge
- hs1.8xlarge
- d2.xlarge
- d2.2xlarge
- d2.4xlarge
- d2.8xlarge
- a1.medium
- a1.large
- a1.xlarge
- a1.2xlarge
- a1.4xlarge
- c5n.large
- c5n.xlarge
- c5n.2xlarge
- c5n.4xlarge
- c5n.9xlarge
- c5n.18xlarge
VPC:
Description: SFTP Gateway will launch into this VPC
Type: AWS::EC2::VPC::Id
SubnetID:
Description: Make sure this subnet belongs to the VPC above.
Type: AWS::EC2::Subnet::Id
DiskVolumeSize:
Default: 32
Description: Disk volume size in GB. Must be at least 32.
ConstraintDescription: Must be a number greater or equal to 32
MinValue: 32
Type: Number
InputCIDR:
Description: Public IP address range for SSH and web access. Use a CIDR range to restrict access. To get your local machine's IP, see http://checkip.dyndns.org/. (Remember to append /32 for a single IP e.g. 12.34.56.78/32)
AllowedPattern: (\d{1,3})\.(\d{1,3})\.(\d{1,3})\.(\d{1,3})/(\d{1,2})
ConstraintDescription: Must be a valid IP CIDR range in the form of x.x.x.x/x.
Type: String
KeyPair:
Description: Make sure you have access to this EC2 key pair. Otherwise, create a new key pair before proceeding.
Type: AWS::EC2::KeyPair::KeyName
ConstraintDescription: Existing EC2 KeyPair.
Resources:
SFTPGatewayInstance:
DependsOn:
- RolePolicies
Type: AWS::EC2::Instance
Properties:
IamInstanceProfile: !Ref EC2InstanceProfile
ImageId: !Ref AMIID
KeyName: !Ref KeyPair
InstanceType: !Ref EC2Type
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: !Ref DiskVolumeSize
VolumeType: gp2
Encrypted: 'true'
NetworkInterfaces:
- AssociatePublicIpAddress: true
DeviceIndex: "0"
SubnetId: !Ref SubnetID
GroupSet:
- !Ref SFTPGatewaySG
Tags:
- Key: Name
Value: SFTPGateway
UserData:
Fn::Base64: !Sub |
#!/bin/bash
# Magic variable read by cloud-init sftpgatewaysetup script
cfn-init --stack ${AWS::StackName} --resource SFTPGatewayInstance --region ${AWS::Region}
cfn-signal -e 0 --stack ${AWS::StackName} --resource SFTPGatewayInstance --region ${AWS::Region}
IPAddress:
Properties:
Domain: vpc
InstanceId: !Ref SFTPGatewayInstance
Type: AWS::EC2::EIP
LogGroup:
Type: AWS::Logs::LogGroup
Properties:
LogGroupName: !Sub sftpgw-${AWS::StackName}
EC2InstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
Path: /
Roles:
- !Ref OpenSFTPGWRole
OpenSFTPGWRole:
Type: AWS::IAM::Role
Properties:
Path: /
ManagedPolicyArns:
- !Sub arn:${AWS::Partition}:iam::aws:policy/AmazonS3FullAccess
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service: ec2.amazonaws.com
Action: sts:AssumeRole
RolePolicies:
Type: AWS::IAM::Policy
Properties:
PolicyName: SFTPGatewayPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- logs:CreateLogStream
- logs:PutLogEvents
- logs:DescribeLogStreams
- logs:CreateLogGroup
Resource: '*'
- Effect: Allow
Action:
- ec2:DescribeAvailabilityZones
- ec2:DescribeInstances
- ec2:DescribeTags
- s3:ListAllMyBuckets
Resource: '*'
- Effect: Allow
Action:
- autoscaling:DescribeAutoScalingInstances
- autoscaling:DescribeAutoScalingGroups
- cloudformation:DescribeStacks
- cloudformation:ListStackResources
Resource: '*'
- Effect: Allow
Action:
- kms:ListAliases
- kms:ListKeys
Resource: '*'
Roles:
- !Ref OpenSFTPGWRole
SFTPGatewaySG:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: SFTPGateway Security Group
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: !Ref InputCIDR
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: !Ref InputCIDR
- IpProtocol: tcp
FromPort: 443
ToPort: 443
CidrIp: !Ref InputCIDR
- IpProtocol: tcp
FromPort: 2222
ToPort: 2222
CidrIp: !Ref InputCIDR
SecurityGroupEgress:
- IpProtocol: tcp
FromPort: 0
ToPort: 65535
CidrIp: 0.0.0.0/0
- IpProtocol: udp
FromPort: 0
ToPort: 65535
CidrIp: 0.0.0.0/0
Outputs:
Hostname:
Value: !Ref IPAddress
Description: Elastic IP address
CloudWatchLogs:
Value: !Ref LogGroup
Description: CloudWatch logs