Creating Unique Credentials
Purpose: Create AWS Access Key credentials for StorageLink Cloud Connections instead of using instance profile.
When to Use: Per-user S3 permissions, cross-account bucket access, or when instance profile isn't available
Steps:
- Create IAM user in AWS console
- Attach custom policy with S3 permissions for specific bucket(s)
- Generate Access Key and Secret Access Key under Security credentials
- Enter credentials in StorageLink Cloud Connection settings
Required IAM Permissions: s3:GetBucketLocation, s3:ListBucket, s3:GetObject, s3:PutObject, s3:DeleteObject
Product: StorageLink by Thorn Technologies — cloud storage gateway for secure file sharing
Overview
When configuring an AWS Cloud Connection, you have two options for the Cloud Connection Credentials. You can either use the instance profile credentials or use unique credentials. The recommended & easiest option would be to use the instance profile credentials.
However, in certain scenarios you will need to use unique credentials. This article walks you through the process of obtaining these unqiue credentials, which are the AWS Access Key ID & AWS Access Secret.
Create an IAM user
You will need to create an IAM user. Permissions to your S3 bucket will be associated with this IAM user from which we will later create the Access Key & Secret.
Navigate to IAM.
Next, navigate to the Users section.
Click Add users and then configure a User name.
Configure S3 permissions
In this section, you will add permissions that are tailored down to a single S3 bucket. This will allow our StorageLink service to read and write to your bucket. If you'd like to use multiple buckets feel free to include them in the policy.
Under Step 2, Set permissions select the permission option of Attach policies directly.
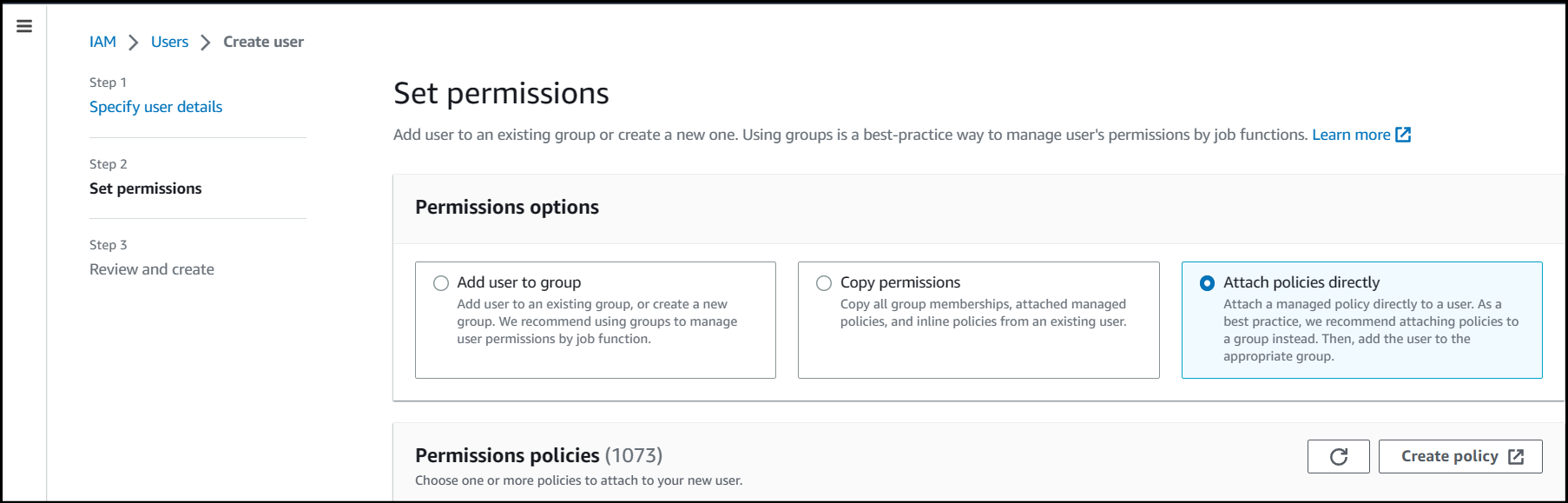
Then, click Create policy. Select the JSON tab.
Give this user the following IAM permissions, via an in-line policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket",
"s3:ListAllMyBuckets"
],
"Resource": [
"arn:aws:s3:::your-bucket-name"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::your-bucket-name/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}
Remember to replace your-bucket-name with the value of your actual bucket name.
Note: Make this change in two locations.
Once your policy has been created, navigate back to the Create IAM user tab.
Under Permission policies, click the refresh icon and you should see one new policy, which you just created. Using the search bar, find your newly created policy and select it.
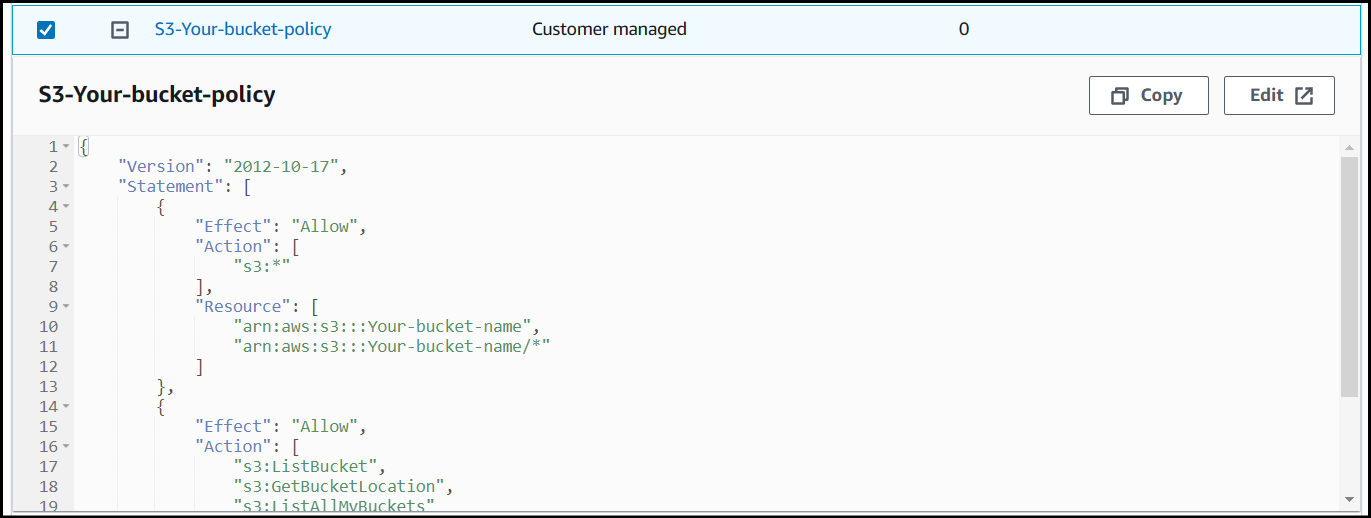
Once your policy has been selected, click Next.
Check that everything looks as it should under Review and create and click Create user.
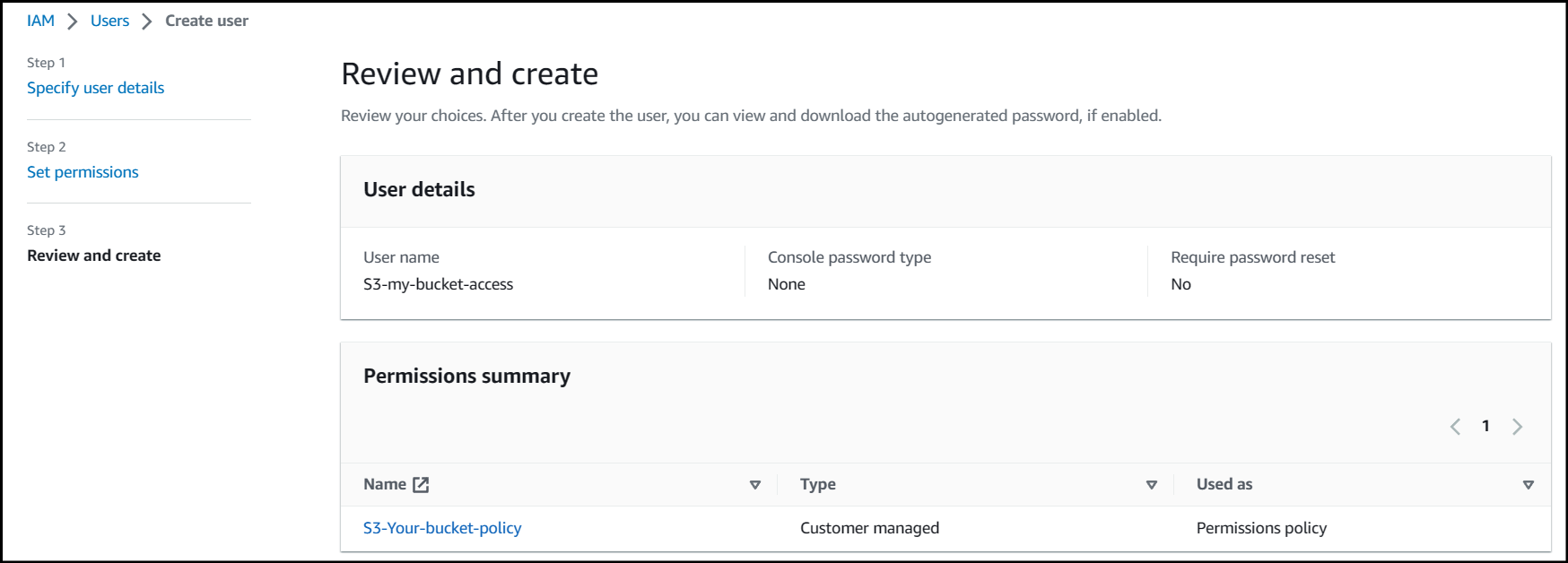
Now that your user has been created, click on it so you're under the Summary page.
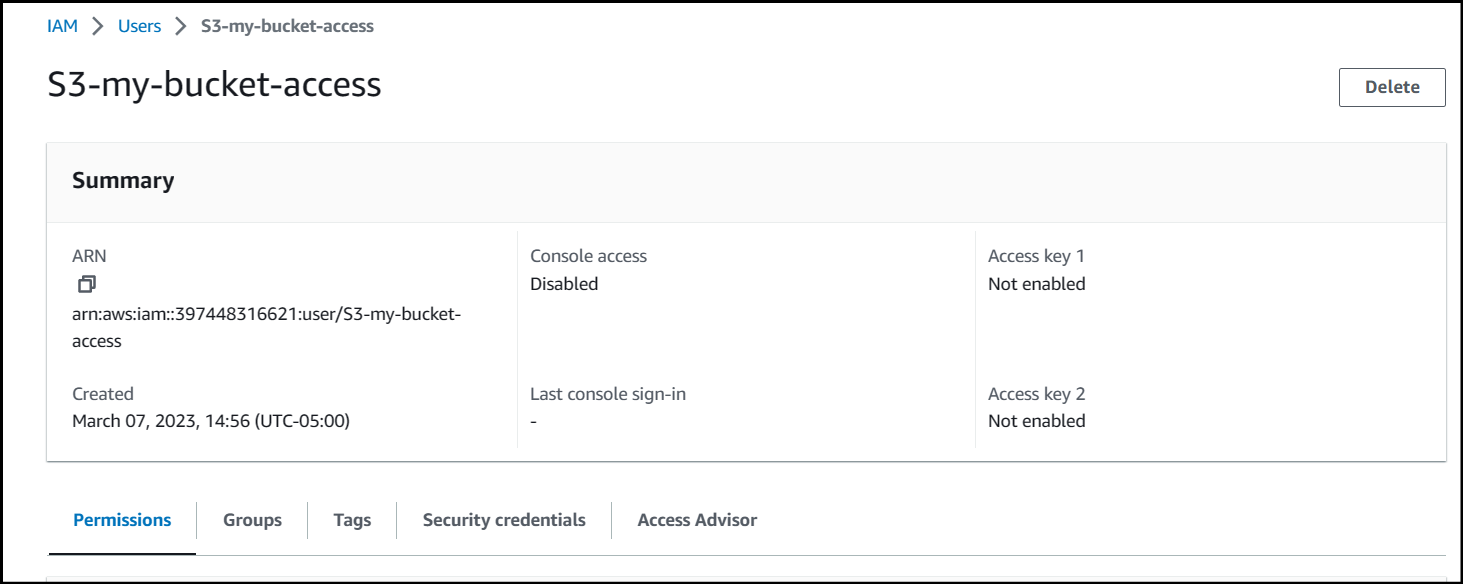
Create the Credentials
Our StorageLink service requires an access key and secret in order to leverage the permissions of the IAM user.
Navigate to the Security credentials tab, and scroll down until you see the Access keys section.
Click Create access key. Navigate through the steps and click Create access key again.
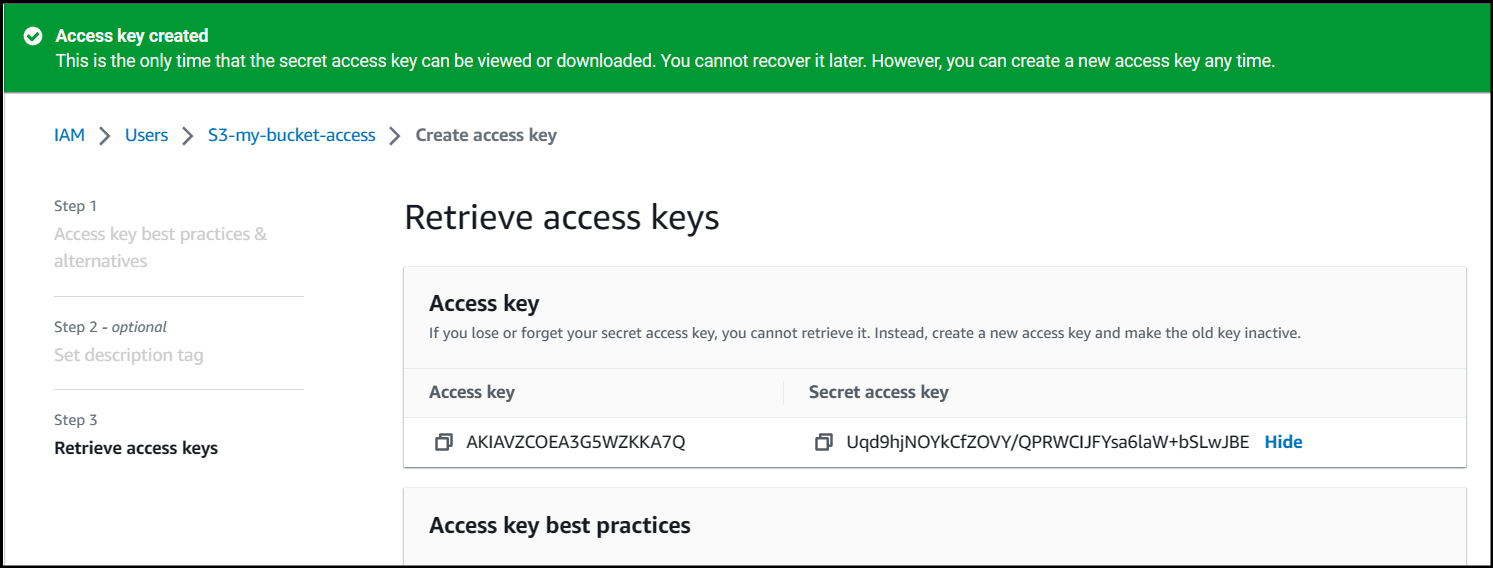
Make sure to store the value of the Access key and especially the Secret access key.
Configure your Cloud Connection
Now that you have the Access key and Secret access key values, you can enter these values for your Cloud Connection Credentials.
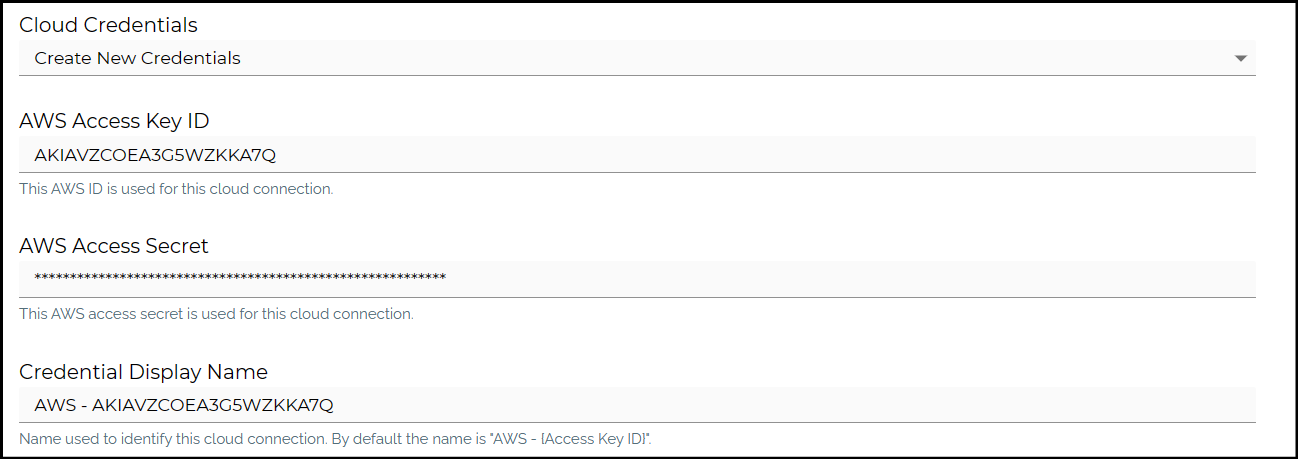
Once you've configured the Cloud Connection Credentials, use the Test Connection feature to make sure you have access to your desired S3 bucket.
