Best practices for production
Here are some recommendations when using sftp gateway in a production environment:
Tailor down s3 access
When using the CloudFormation template, by default the ec2 role has s3 full access. This is necessary because sftp gateway needs to create s3 buckets when setting custom bucket paths for users.
But once you've figured out what custom s3 buckets you need to create, you should lock down the s3 permissions on your ec2 role.
This article shows you how to restrict access to a single s3 bucket.
Disk utilization monitoring
Local disk storage could fill up over time. For example, sftp users could upload files to their local directory. Or, files could pile up because a winscp user did not turn off their resume/transfer setting.
By default, ec2 instances do not log disk utilization metrics to CloudWatch.
This article walks you through installing Amazon CloudWatch monitoring scripts for Linux, so that you can create alarms for low disk space.
Enable single thread
Prior to version 1.003.3, traffic spikes, such as sftp users uploading multiple small files for a data lake scenario, or an initial upload of a backlog of files, could quickly overwhelm an SFTP Gateway instance.
For version 1.003.3 and newer see Enable Multi-threaded Support
To improve stability, edit the file:
/home/ec2-user/.sftpgateway/sftpgateway.properties
and make sure the singlethread property looks like this:
sftpgateway.singlethread=yes
The singlethread setting queues movetos3 operations so that files upload one at a time. This way, you won't run
into memory problems, even if users upload many files at once.
Upgrade to an m4.large instance
When testing sftp gateway for your environment, it makes sense to use a t2.micro to save money, but when moving to production, it's a good idea to upgrade the instance to an m4.large.
The t2 class is "burstable", which means it can handle brief traffic spikes. However, performance gets throttled
under sustained load. The m4 class is better suited to production because it has a higher baseline for compute,
memory, and network throughput.
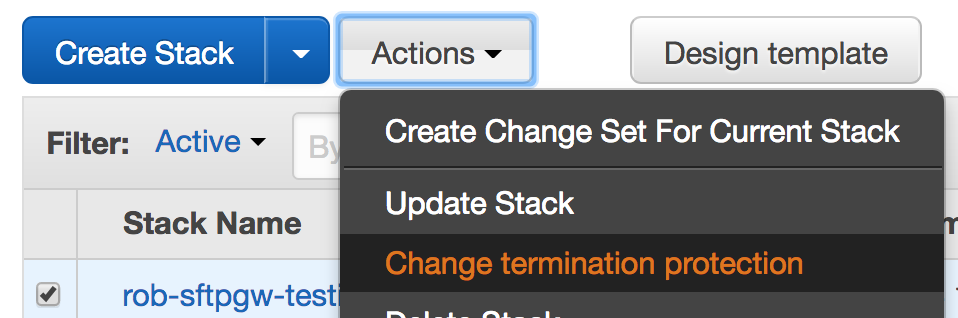
Enable termination protection
You want to enable termination protection on your production resources, so they don't get accidentally deleted.
To do this in CloudFormation, go to actions > change termination protection
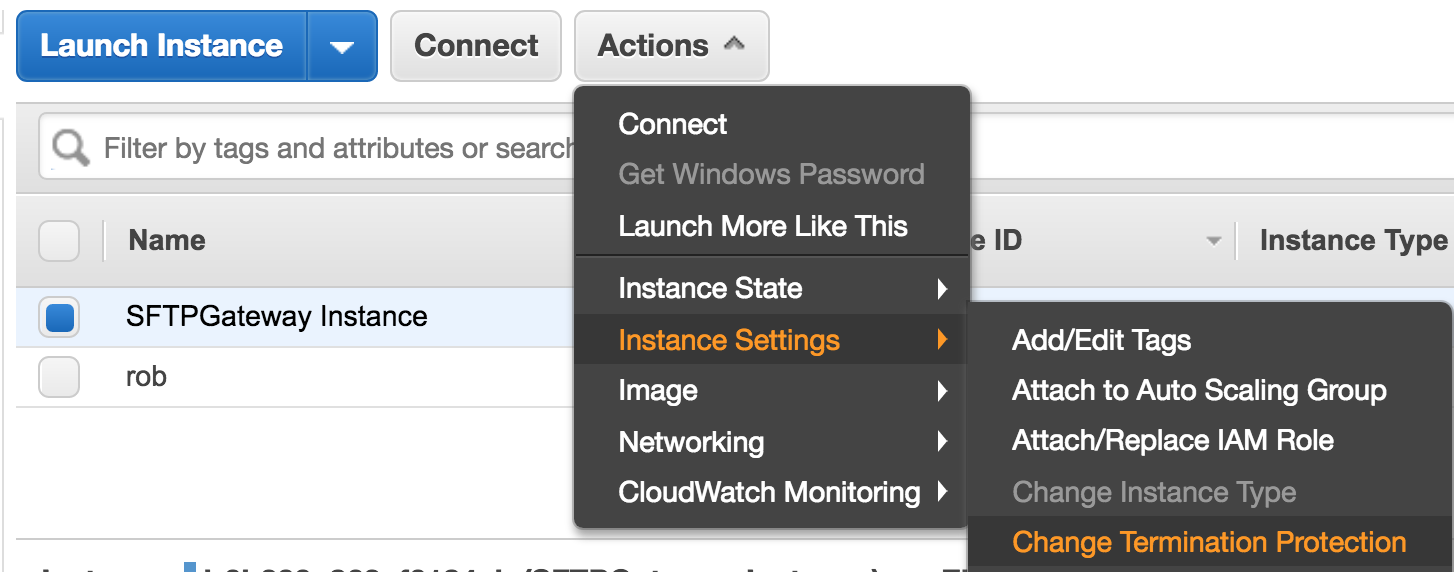
You also want to enable termination protection on the EC2 instance itself. go to actions > instance settings > change termination protection
Take a final snapshot of your server
Once you have configured your settings and provisioned users, take a snapshot of your server. Go to EC2 > check the box next to your instance > actions > image > create image. If for some reason your server gets mis-configured or corrupted, you can spin up a known good working ami.
Reduce the cost of running sftp gateway
Once you have a production instance running around the clock, there are some things you can do to reduce long term costs. SFTP Gateway has an annual pricing option that costs less than the hourly rate, and EC2 offers reserved instances that provide savings options as well.
For more information, check out this article
Assign an Elastic IP address
It is recommended that your SFTP Gateway instance have an elastic IP address assigned to it, so that the public IP address will persist through server shutdown and restart. An instances that does not have an Elastic IP address will loose it's public IPv4 address each time the instance is shutdown.
If you launched your SFTP Gateway instance from our CloudFormation Template, then your instance will already have an Elastic IP address assigned to it.
For instructions on how to assign an Elastic IP address to your EC2 instance, see this AWS Elastic IP documentation.