Restrict S3 access on your IAM policy
The CloudFormation template grants your SFTP Gateway EC2 instance access to all S3 buckets in your AWS account. This is because SFTP Gateway needs the ability to create custom S3 buckets, or point users to existing buckets.
Once you're done setting up your users and S3 buckets, you should lock down S3 permissions on the IAM role.
- Go to IAM > Roles
- Search for S3WritableRole
- Click on the Role created by the SFTP Gateway CloudFormation template
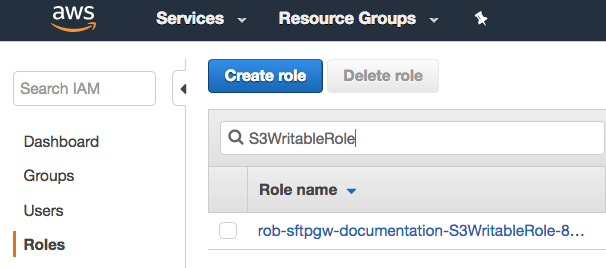
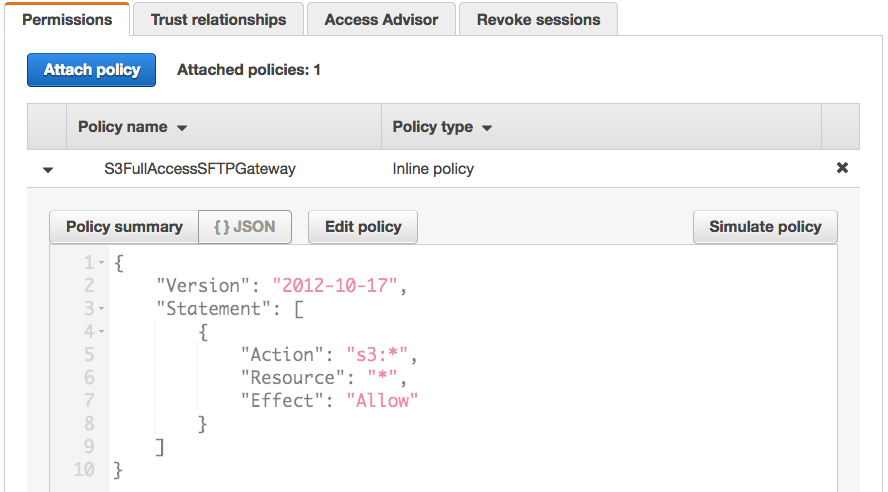
Under Policy name, you should see an inline policy called S3FullAccessSFTPGateway. Expand this, and you should
see the following JSON:
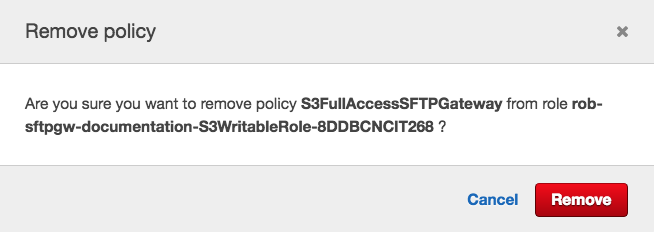
Go ahead and delete the S3FullAccessSFTPGateway inline policy by clicking the x button to the right.
In the pop-up modal, click Remove to confirm.
Next, click the + Add inline policy button on the bottom right.
Click on the JSON tab, and paste in the following (remember to replace the S3 bucket name):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:*"
],
"Resource": [
"arn:aws:s3:::sftpgateway-i-0123456789abcdefg",
"arn:aws:s3:::sftpgateway-i-0123456789abcdefg/*"
]
}
]
}
Click Review policy.
Name the policy something like "CustomS3Policy", and finally click Create policy.
The inline policy you created restricts your SFTP Gateway instance to a single S3 bucket, and all the objects within.
Feel free to edit this policy to meet the specific requirements for your environment. For example, you can grant your EC2 access to multiple buckets:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:*"
],
"Resource": [
"arn:aws:s3:::sftpgateway-i-0123456789abcdefg",
"arn:aws:s3:::sftpgateway-i-0123456789abcdefg/*",
"arn:aws:s3:::your-existing-s3-bucket",
"arn:aws:s3:::your-existing-s3-bucket/*",
]
}
]
}
Note: Even if you set all your SFTP users' upload destinations to custom S3 buckets, you should still grant
permissions to the default bucket.