Encrypting local server data at rest
For compliance reasons, you may need to encrypt the data at rest when files are stored locally on the SFTP Gateway
instance. These files could reside in the user's local, shared, or downloads directories.
The approach outlined here is to mount an encrypted EBS volume onto /home. This involves 4 main steps:
- Back up the ec2-user's home directory, so you can SSH in after a reboot
- Create an EBS encrypted volume
- Attach the volume
- Mount the volume
- Make sure the volume mounts on subsequent reboots
Credit goes to this helpful tutorial
Back up the ec2-user's home directory
The ec2-user's home directory contains a few important hidden folders:
.ssh: This is what allows your key pair to SSH into the instance.sftpgateway: Contains a config file that is global to the SFTP Gateway instance- Other bash settings that are useful
The following backs up the entire folder:
sudo su
cp -a /home/ec2-user/ /root
Create an EBS encrypted volume
- EC2 > Volumes > Create Volume
- Change size to 32 GB (default is 100, but use a sensible size)
- Make sure the Volume's AZ matches the instance’s AZ
- Check the box for Encryption
- Add a Tag (Name=sftpgw-ebs-encrypted). You're going to have a lot of volumes, so this is the best way to identify it later
- Click Create Volume
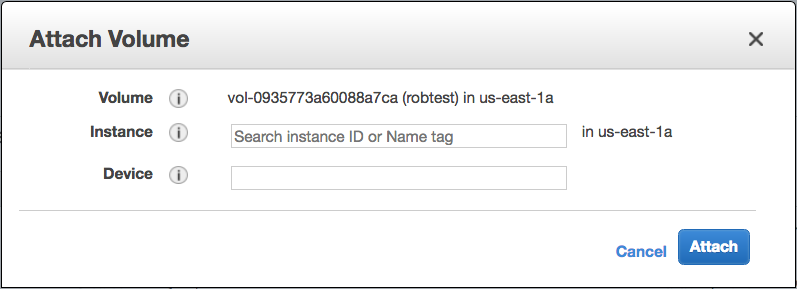
Attach the volume
- Click the link that takes you to the volume you just created
- Select your new volume
- Go to Actions > Attach Volume
- Select your EC2 instance from the drop down menu
- Click Attach
Mount the volume
The following initializes the volume's file system, and then mounts it on /home:
mkfs -t ext4 /dev/xvdf
mount /dev/xvdf /home
This restores the ec2-user's home directory (and removes the lost+found folder):
mv /root/ec2-user/ /home/
rmdir /home/lost+found
Make sure the volume mounts on subsequent reboots
Back up the fstab file:
cp /etc/fstab /etc/fstab-orig
Append the following line to /etc/fstab:
/dev/xvdf /home ext4 defaults,nofail
Make sure there are no errors:
mount -a
Reboot, and make sure it comes back up.
init 6