FileZilla Setup
Setup using the AWS CloudFormation template is recommended. If the SFTP Gateway was setup using a single AMI only, then certain AWS resources must be configured after first launching the instance.
To log into the SFTP Gateway server using SSH, follow the GIF below. Be sure to enter ec2-user for the user, your
public IP for the host, and select the key file you used when launching the instance.
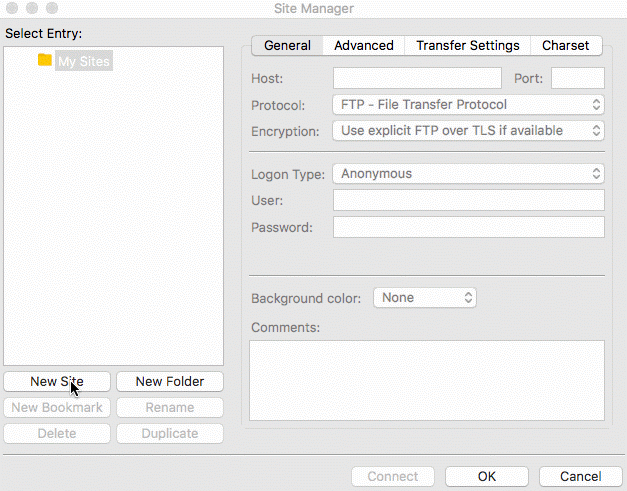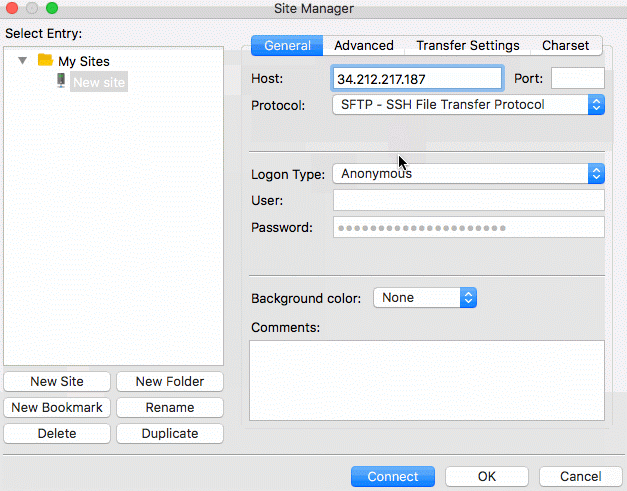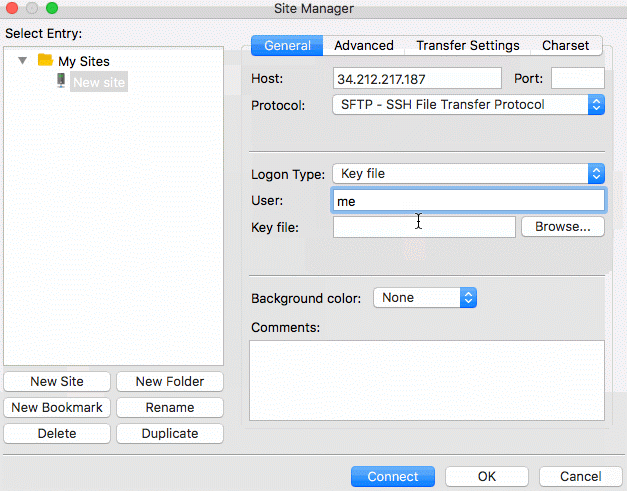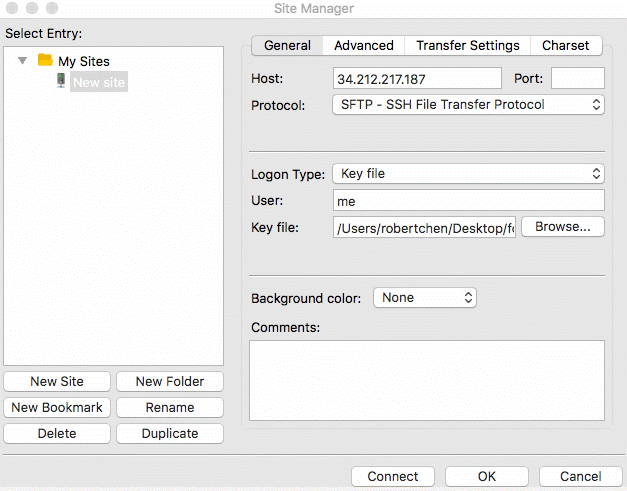
Once logged in, run the following command to setup the S3 bucket and other necessary properties:
sudo sftpgatewaysetup. The EC2 instance that is launched must have an IAM Role that has AmazonS3FullAccess
permission for proper setup.
The AMI comes preloaded with administration commands to add and delete users.
From the primary ec2-user user account, run the following command to add a new user: sudo addsftpuser <username>.
Running this command will do the following things:
- Create the new Linux user
- Disable the users login shell so they can only SFTP and not SSH to the server
- Setup the appropriate home directory for SFTP
- Create user's new SSH key and email the key to a chosen address
Uploads will only occur within the user's upload directory.
Users can be deleted by running the following command from the primary ec2-user account
sudo deletesftpuser <username>. The user's account, their SSH key, and their home directory along with everything in
it, will be deleted. Be sure to backup the home directory before running this command if you want to keep the files.
Connecting as a user
When creating a new user, the user's SSH key is emailed to a chosen address. In order to SFTP into the server as that user, you need to convert the emailed plaintext key into a usable .pem key.
Mac
- In a terminal window, run
nano userPrivateKey.pemand paste the contents of the email, including the start and end tags. - Press Ctrl+X, then Y when prompted to save the file.
- Run
chmod 600 userPrivateKey.pemto make sure the file permissions are correct. - You can now SFTP into the server as the new user by running
sftp -i userPrivateKey.pem <user>@<public ip>.