Azure AAD Integration with the Web Admin UI
Note: This page applies to SFTP Gateway version 2.x.
Visit Here for documentation on version 3.x.
Overview
With SFTP Gateway 2.001.00, you can now integrate the web admin UI login page with AAD authentication. In other words, you can log into the SFTP Gateway web admin page, using your AAD login.
There are a lot of steps involved. But at a very high level, you will be performing three steps:
- Create an App Registration, and configure it (the majority of the steps)
- Grant users in AAD access to this App Registration
- Point SFTP Gateway to the App Registration
Note: This article does not cover how to integrate SFTP users with AAD integration.
Create an App Registration in the Azure Portal
Open the Azure Portal and search for App Registrations.
Click + New Registration. You'll see the following screen:
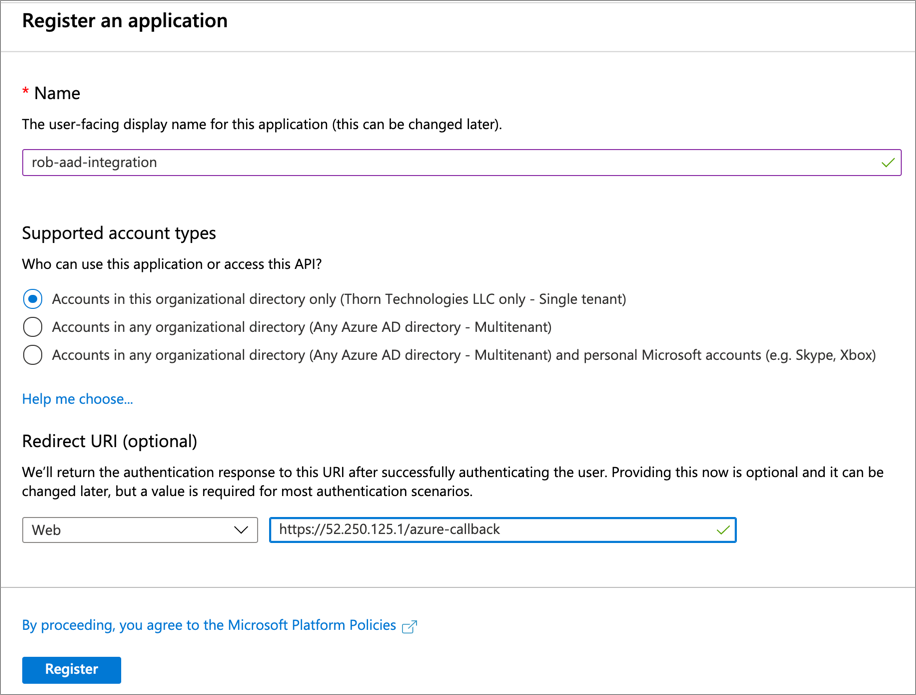
Enter a Name for your App Registration.
For Redirect URI, choose Web from the drop-down, and paste in the following URL:
https://<sftp-gateway-public-ip>/azure-callback
Click Register.
Edit the App Registration (Authentication tab)
Within the App Registration, click on the Authentication link on the left.
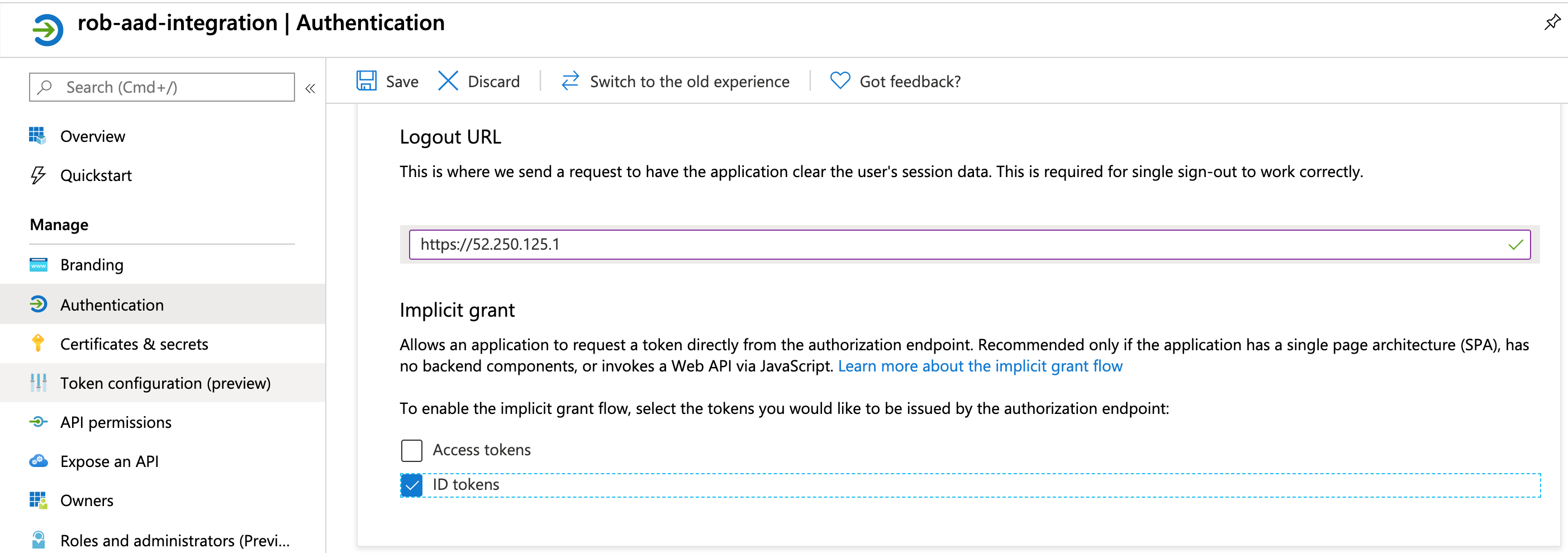
Set the Logout URL to:
https://<sftp-gateway-public-ip>
Check the box next to ID tokens.
Click Save.
Edit the App Registration (Token Configuration tab)
Within the App Registration, click on the Token Configuration link on the left.
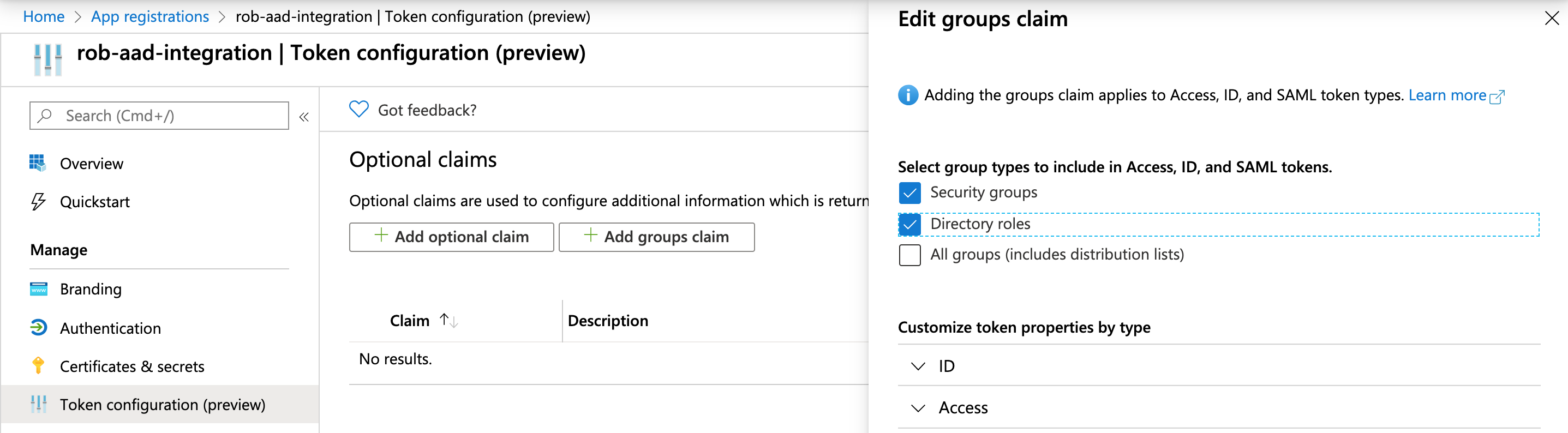
Click on Add groups claim.
Check the boxes for Security groups and Directory roles.
Click Add.
Generate a GUID
For this step, you will need to generate a GUID.
In Bash, you can run the command:
uuidgen
And you will get the following output:
616219BD-9014-4B6E-9FBE-676DC9014A6E
Or, you can go to this website to generate a GUID: https://www.guidgenerator.com/online-guid-generator.aspx
Edit the App Registration (Manifest tab)
Within the App Registration, click on the Manifest link on the left.
You should see a massive JSON object.
Around line 8, you should see this line:
"appRoles": [],
Insert the following JSON object, so that it looks like this:
"appRoles": [
{
"allowedMemberTypes": [
"User"
],
"description": "SFTPGW Admin access",
"displayName": "SFTPGWAdmin",
"id": "<Generated GUID>",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "SFTPGW_Admin"
}
],
Make sure you replace <Generated GUID> with the GUID that you created
earlier.
Click Save.
Add users in AAD
In the Azure Portal, go to Azure Active Directory.

On the left, click on Enterprise applications.
Search for your App Registration's name that you created earlier. (If it doesn't show up, choose Enterprise Applications from the drop-down menu.)
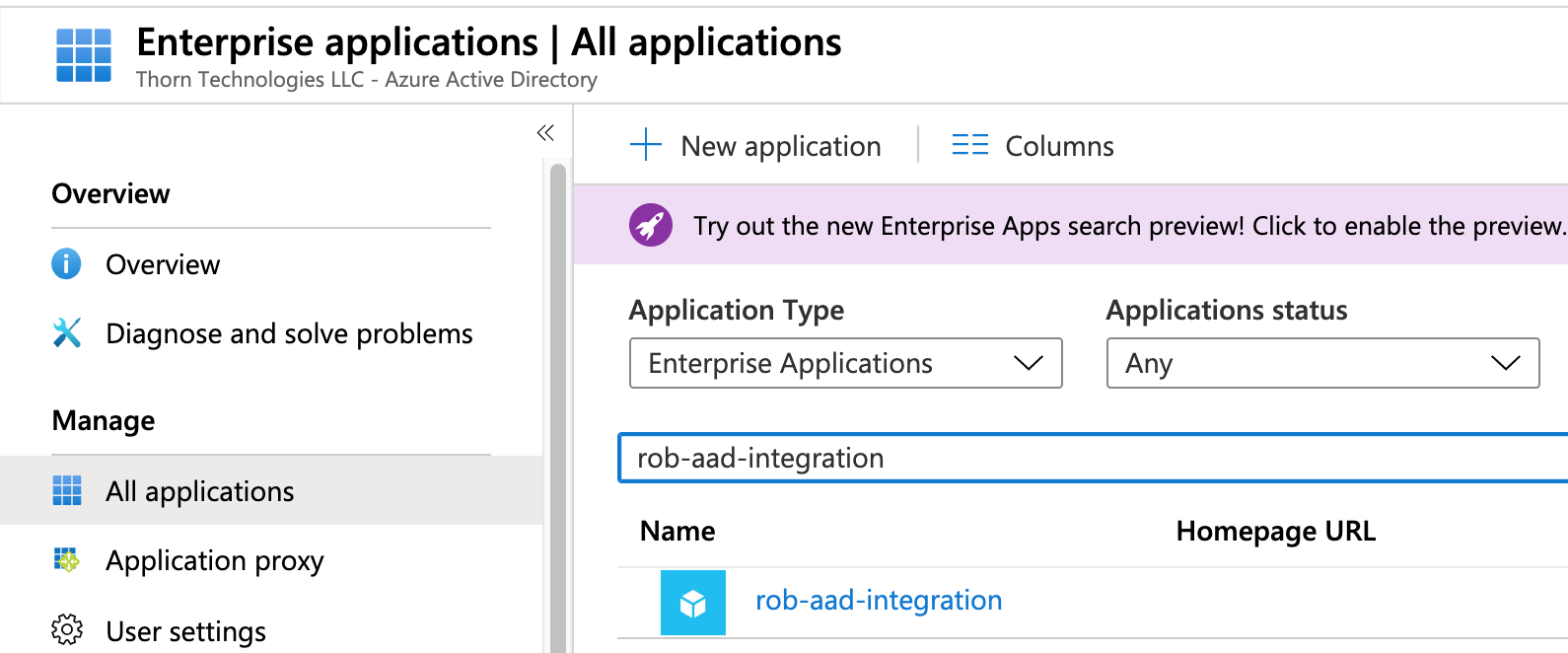
Click on your Application. You will see this screen:
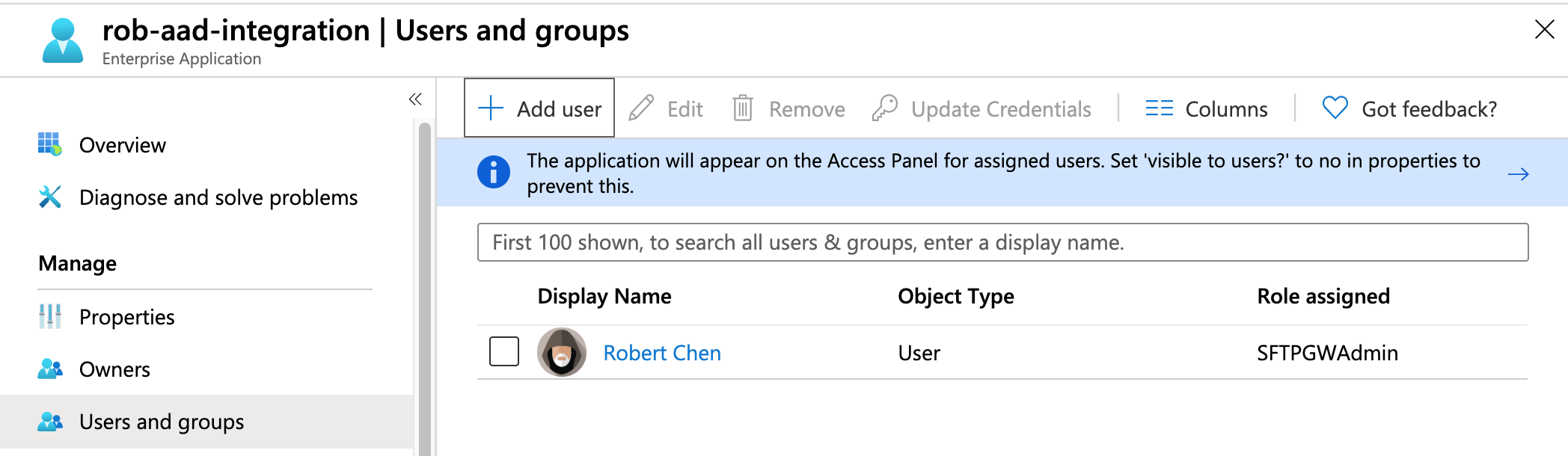
On the left, click on Users and Groups.
Click on + Add user.
You will see an Add Assignment page. Select the users that you wish to grant access, and then click Assign.
Get App Registration IDs
In the Azure Portal, go back to App Registrations.

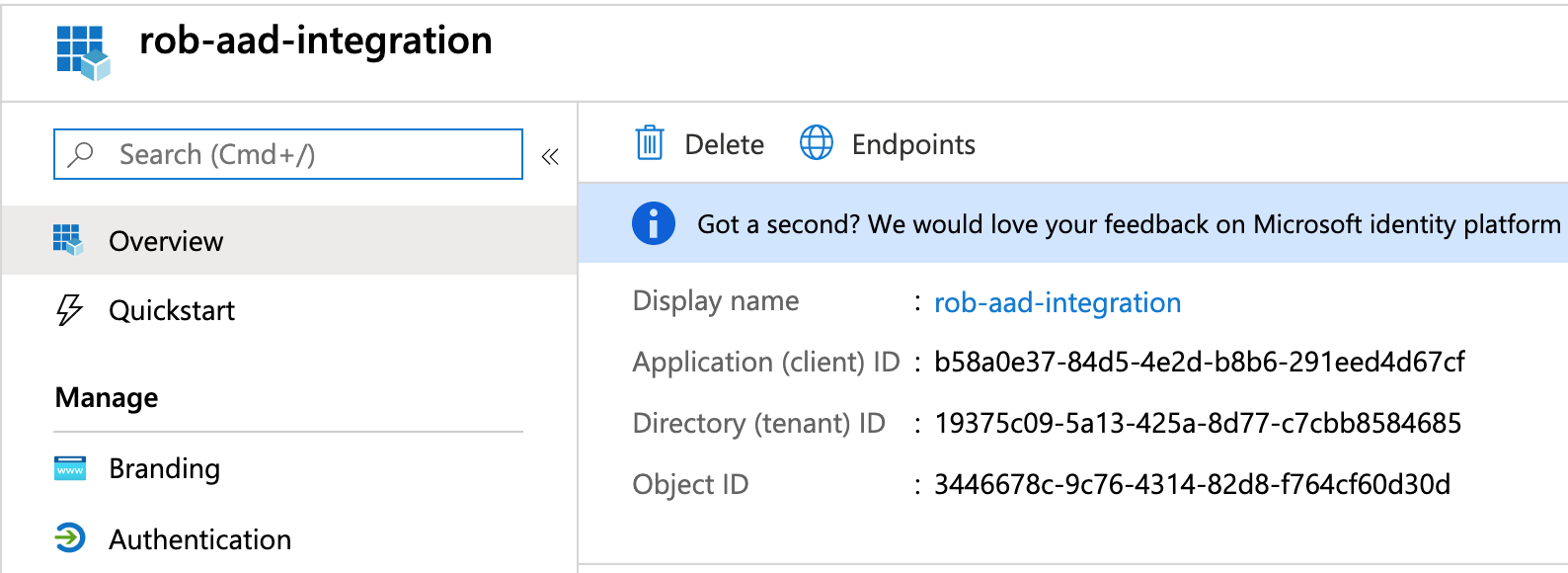
Click on the App Registration that you created earlier.
On the Overview page, note the Application (client) ID and the Directory (tenant) ID.
Run a command on SFTP Gateway
SSH into SFTP Gateway, and run the following command:
sudo setup-azure-ad-integration \
--client-id <CLIENT_ID> \
--tenant-id <TENANT_ID>
- CLIENT_ID: This is the Application (client) ID
- TENANT_ID: This is the Directory (tenant) ID
Test the changes in the web browser
If you are logged into the web admin UI, click the logout button on the top right.
Refresh the browser.
On the login page, you should see the following link toward the bottom that says Login with Azure SSO Credentials.
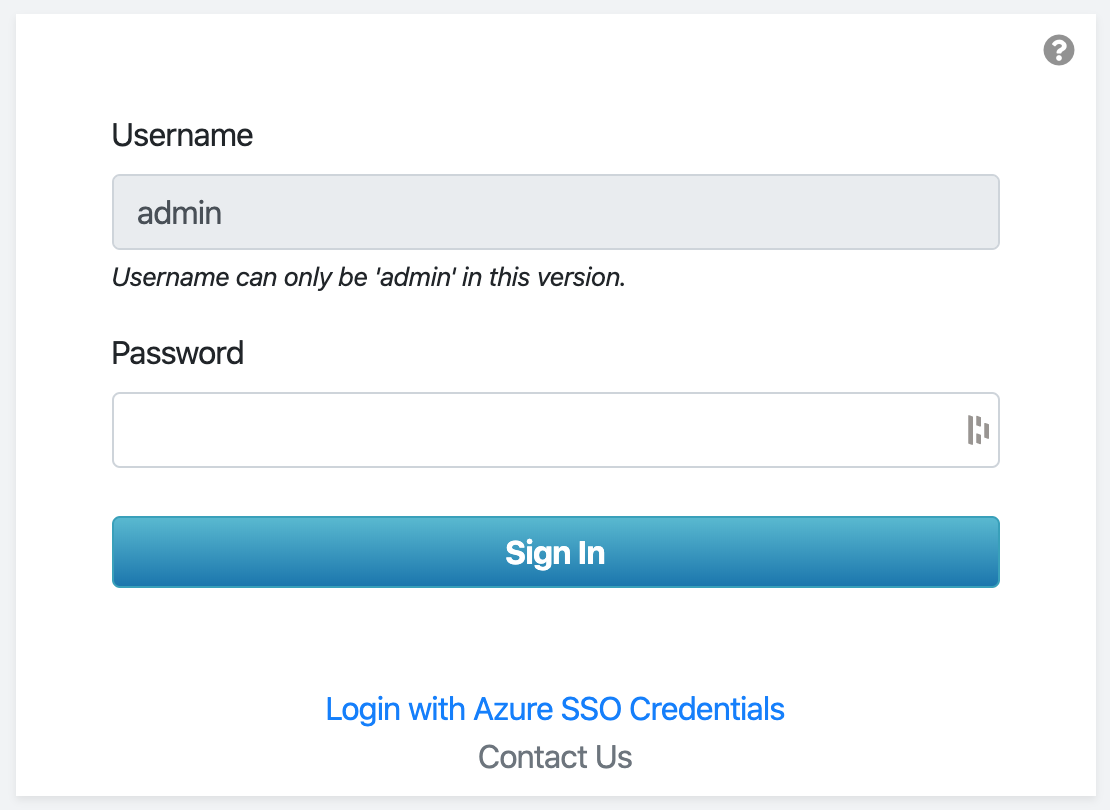
You will be redirected to login.microsoftonline.com to enter your AAD credentials.
Once logged in, you will be authenticated to the SFTP Gateway web admin UI.
Note: If you see the resetadminpassword modal, close it using the (X) button at the top right.
To remove the AAD integration
If you later decide to remove AAD integration with the web admin UI, you can run the following command:
sudo setup-azure-ad-integration --remove
Note: You might need to force refresh your browser before the Login with Azure SSO Credentials link disappears.