CloudFormation: HA new network
Overview
SFTP Gateway versions 3.3.1 and later have a high availability (HA) feature.
This article shows you how to deploy SFTP Gateway with an HA configuration into a new VPC network.
CloudFormation AWS Marketplace deployment instructions
To deploy the HA New Network CloudFormation template, go to the AWS Marketplace.
You first need to subscribe to the SFTP Gateway product. Doing so allows your AWS account to use the SFTP Gateway AMI.
Click here to open the AWS Marketplace page for SFTP Gateway.
Click the Continue to Subscribe button.
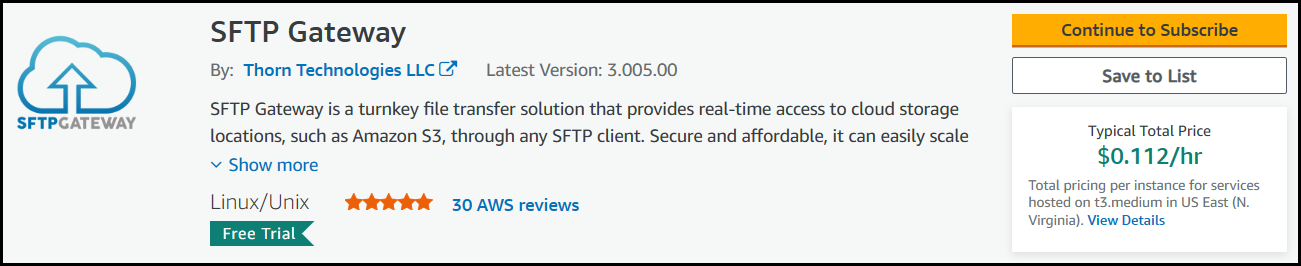
Once you are subscribed, click Continue to Configuration.
Under the Fulfillment Option, choose CloudFormation Template and pick the following option:
- SFTP Gateway (High Availability-New Network)
Under the Software version, select the latest version.
Under Region, select the appropriate region.
Once you are finished click the Continue to Launch button.
On the Launch this software page, under Choose Action, select Launch CloudFormation.
Click Launch.
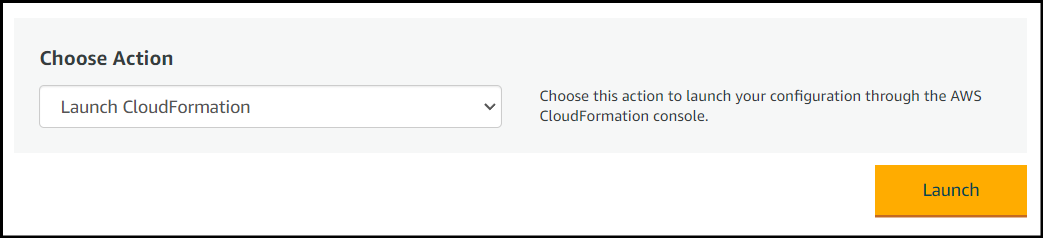
This will take you to the CloudFormation service in the AWS console.
Spinning up an HA CloudFormation stack
If you followed the instructions in the previous section, you should now be in the CloudFormation service within the AWS console.
The Template source should be pointing to a location on S3 corresponding to the CloudFormation template you specified.
You also have the ability to download the CloudFormation template via this link.
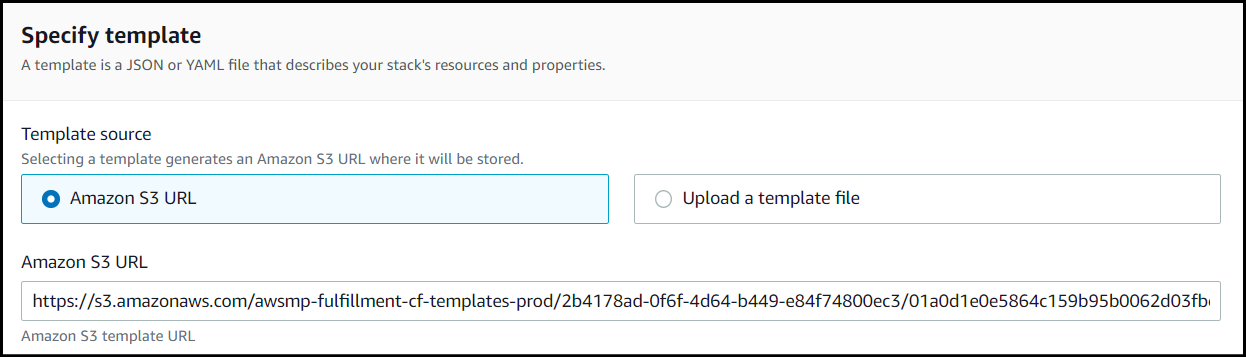
To spin up a High Availability (New Network) CloudFormation stack of SFTP Gateway:
The Template source is already selected, so click Next to continue.
Enter the details for the stack:
Stack name: The name of your CloudFormation stack.
Bucket Access: The default is
restricted, which limits access to S3 buckets following a naming convention. Chooseopento allow access to all S3 buckets.EC2 Type: Defaults to
t3.medium. We recommend usingm5.largefor production workloads.Disk Volume Size: Defaults to
32 GB. We use S3 as the file system, so this should be enough to accommodate the OS and rotated logs.Key Pair: Choose a
Key Pairthat you have access to.Desired Capacity: Defaults to
2. This determines how many instances you want to run.VPC IP Range: Select a Class C IP range for your VPC. Defaults to
192.168.1.0/24.Input CIDR: Enter a CIDR range (e.g.
1.2.3.4/32) that represents the IP address your workstation. This opens an ingress rule for sysadmin use.SFTP Input CIDR: Enter a CIDR range for the SFTP service. Defaults to
0.0.0.0/0.DB Class: This is the database service instance class. Defaults to
db.t3.micro, since SFTP Gateway is not database-heavy.
Stack Options: The stack options page can be left as is. Scroll to the bottom of the page and click Next.
Review and create stack.
- You must check the box that reads I acknowledge that AWS CloudFormation might create IAM resources to give CloudFormation permission to create IAM resources.
The stack creation progress can be monitored by selecting the stack and viewing the Events tab. Any errors that occur during creation will appear in the event log.
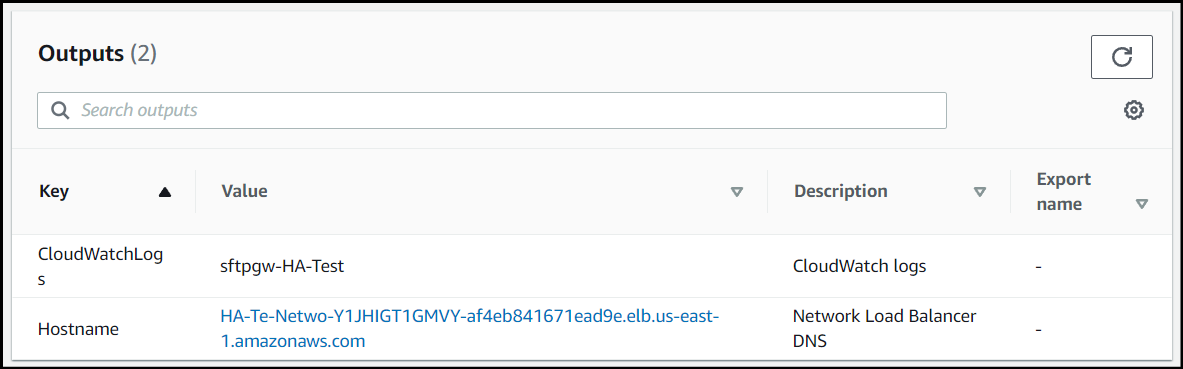
When the CloudFormation stack is created, go to the Outputs tab.
For the Hostname field, there will be a link to the Network Load Balancer's DNS hostname. Click this link, and it will take you to the web admin portal.
Then, configure SFTP Gateway as you normally would, by creating the first web admin account in the First Launch Experience.