Configuring an SSL cert for High Availability via ACM
TLDR - Quick Summary
What: Configure SSL certificate for HA deployment using AWS Certificate Manager
Steps: Create ACM cert, validate via DNS CNAME, create TLS Target Group, modify NLB 443 listener to TLS
Final Step: Attach TLS Target Group to Auto Scaling Group
Overview
The Network Load Balancer on AWS supports SSL termination via a TLS listener. The NLB can also use TLS to connect to the instance behind the load balancer, making end-to-end encryption.
Before getting started, you’ll need to create a certificate in ACM. This is very straight forward to do if using Route 53 for DNS.
Creating a certificate in ACM
First, navigate to the AWS Certificate Manager service.
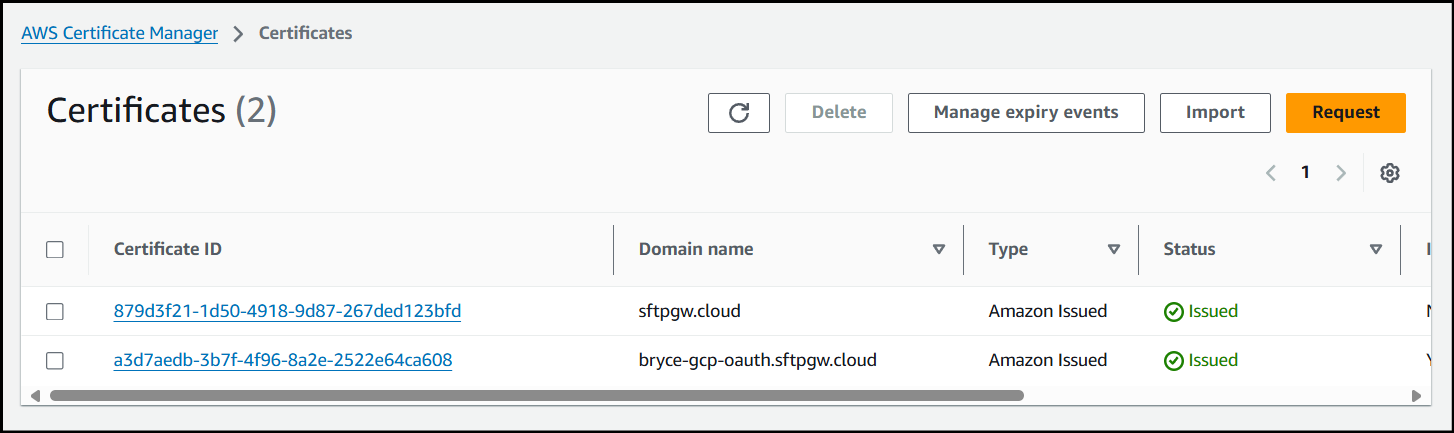
Next, click Request to create a new certificate.
In this example, we will be using a public certificate.
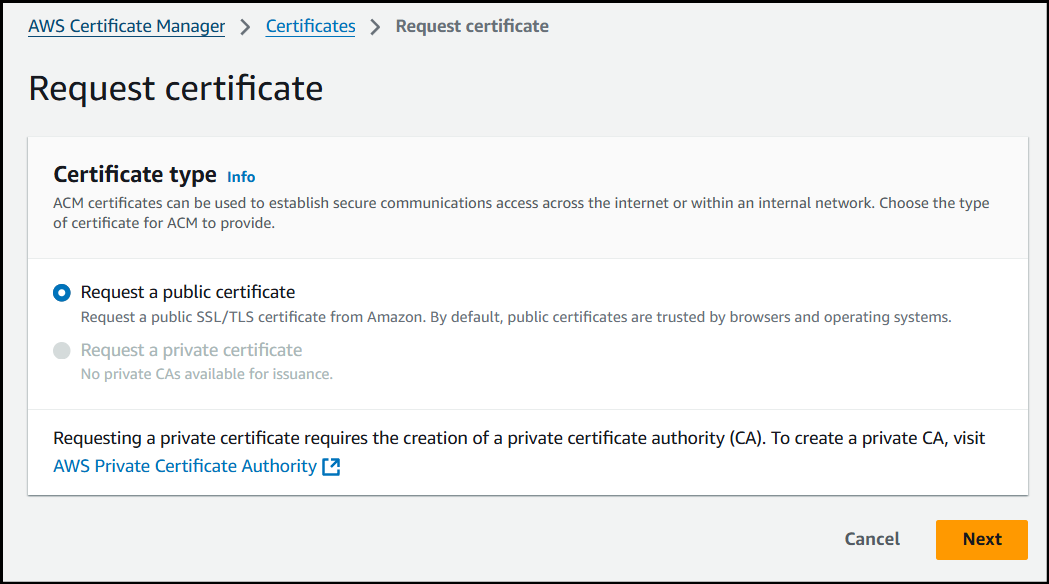
Enter the FQDN (Fully qualified domain name) or Hostname you plan to use. In this example I will be using DNS validation.
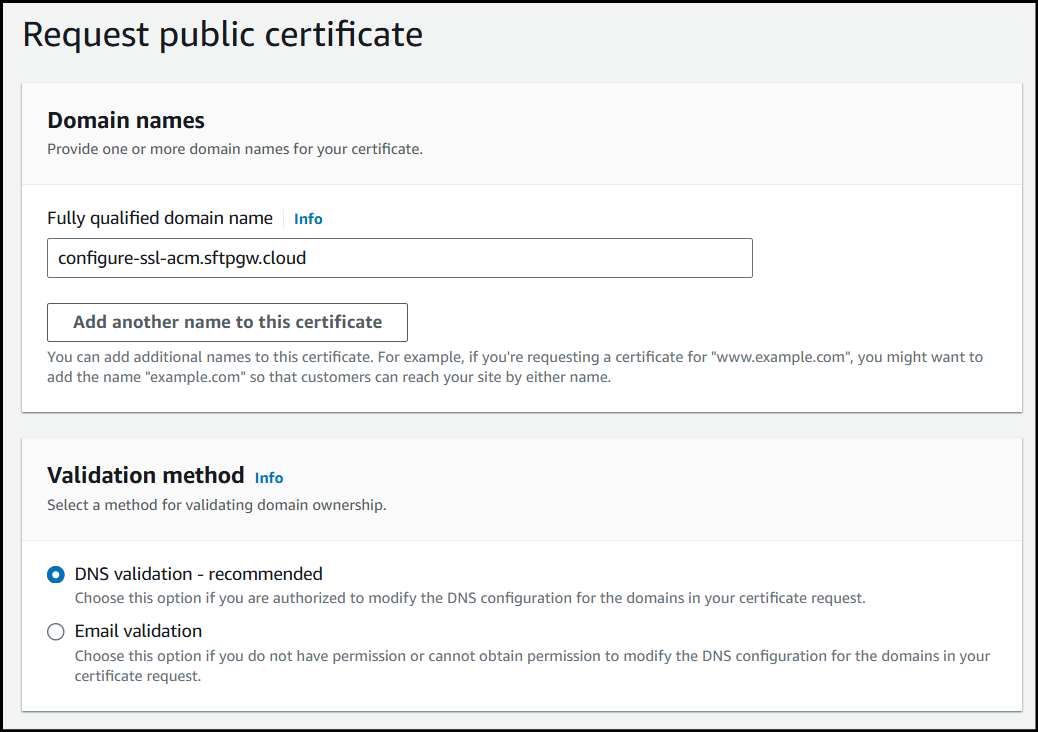
Select the Key algorithm you'd like to use for your cert and then click Request to create the certificate.
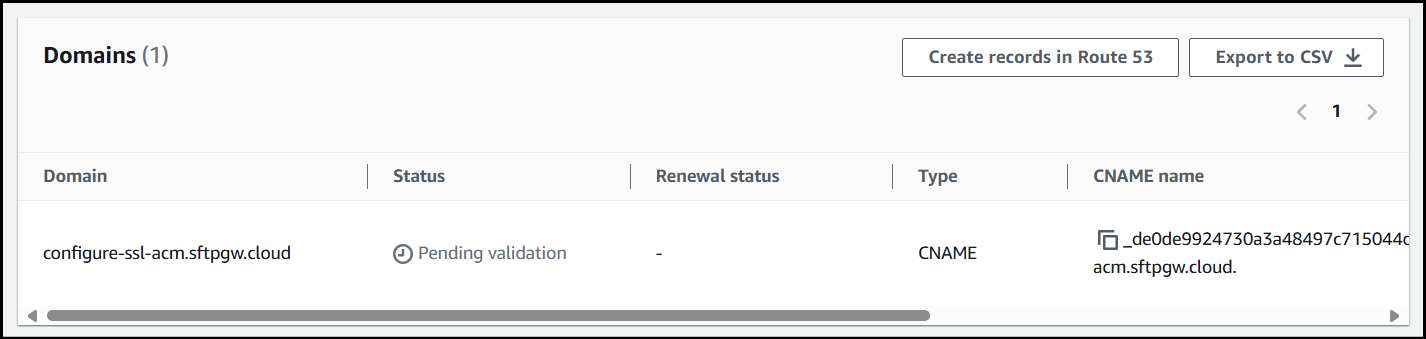
Now that the cert has been created, in order to get past Pending validation, we need to create a new CNAME record for our domain.
Creating a CNAME record
In this example, I will be using a domain hosted in Route 53.
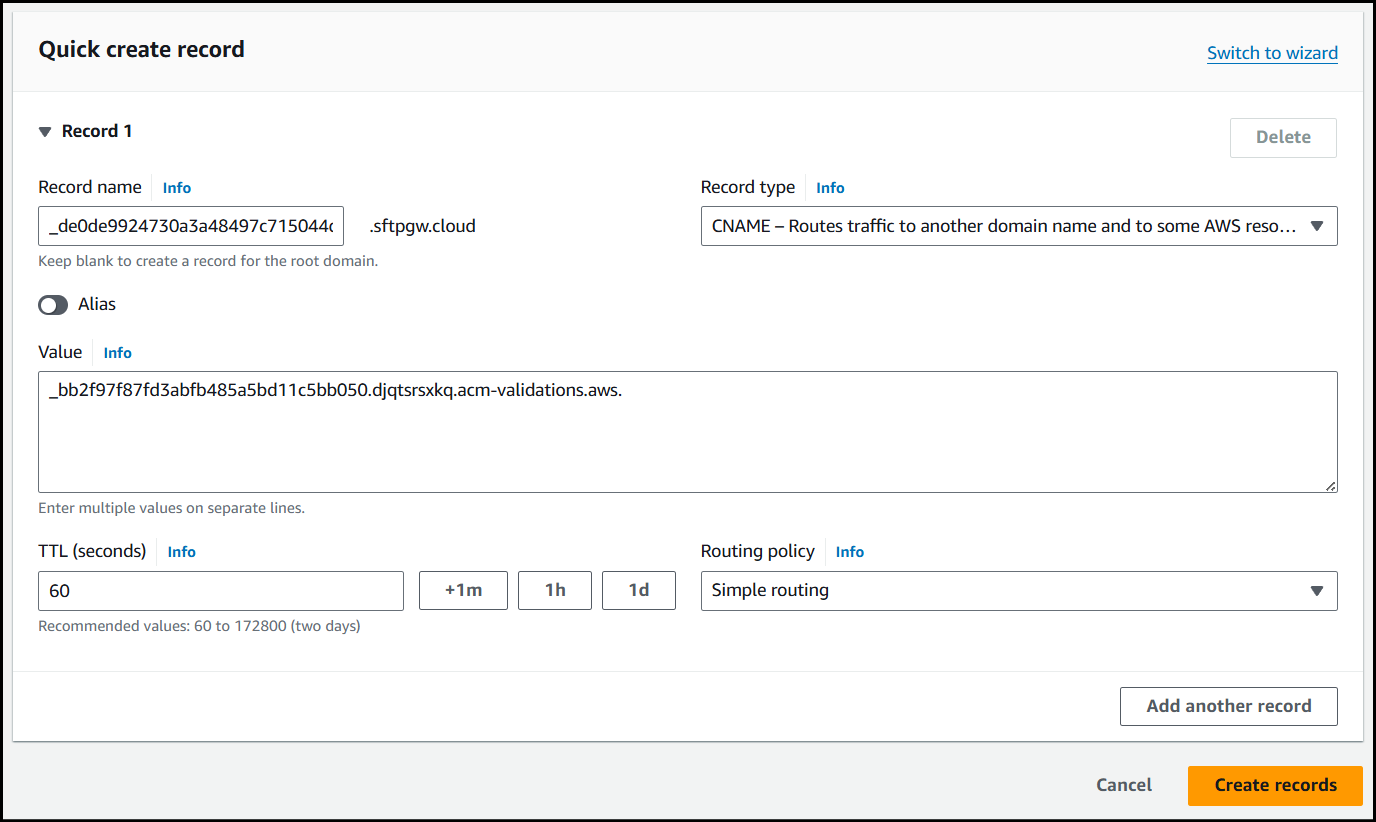
Once inside my domain, I will create a new CNAME record using the below values for reference:
Record Name - _de0de9924730a3a48497c715044d0cc4.configure-ssl-acm.sftpgw.cloud
When creating the record name I just used _de0de9924730a3a48497c715044d0cc4.configure-ssl-acm since .sftpgw.cloud is already being appended to the end of the name.
Record Type - CNAME
Record Value - _bb2f97f87fd3abfb485a5bd11c5bb050.djqtsrsxkq.acm-validations.aws.
Once the record has been created, navigate back to your certificate in ACM.
It'll likely still have the Pending validation message.
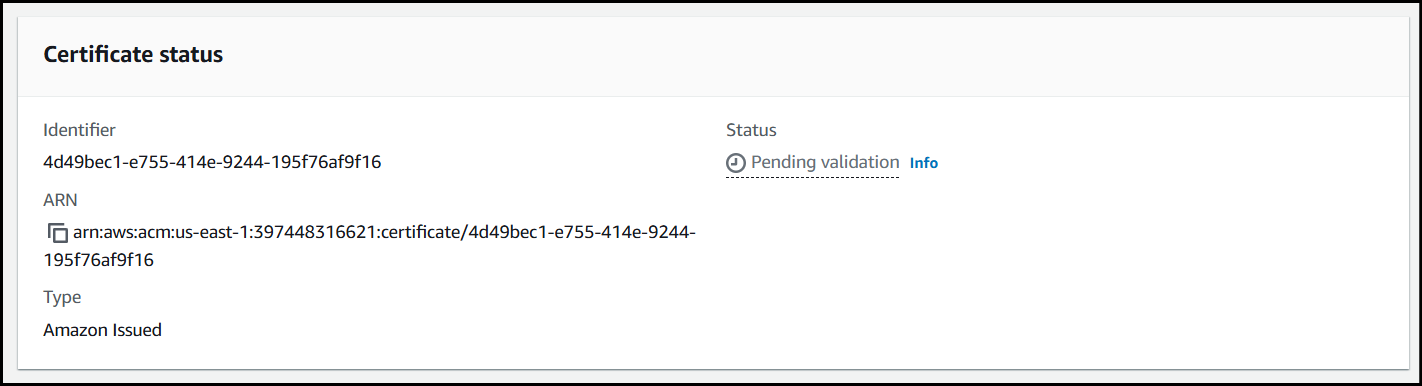
Wait around 5-10 minutes and refresh the page, where you should see your certificate has been issued.
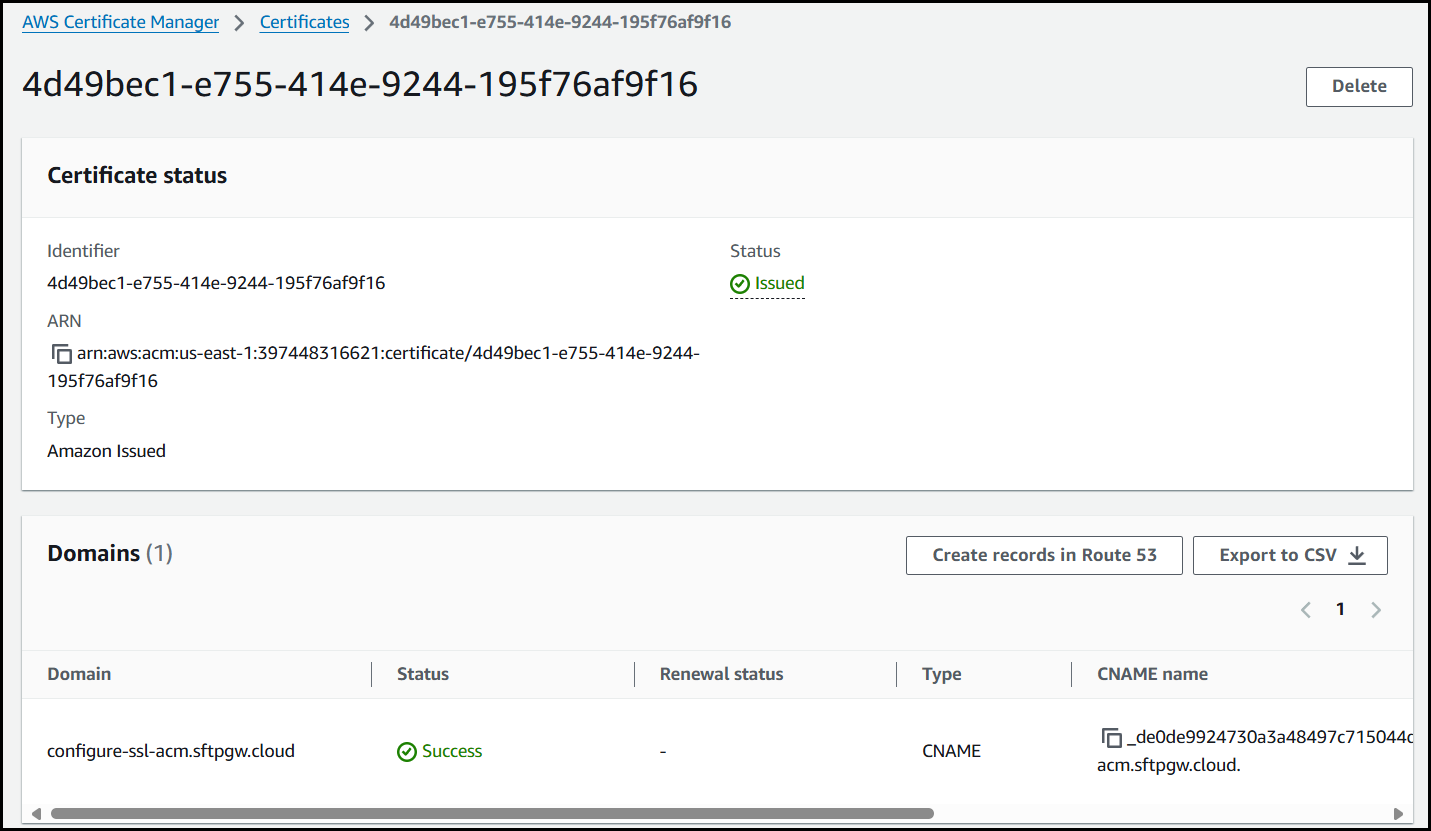
Now that the cert has been issued, we can begin configuration of our HA deployment to use the ACM cert.
Create a Target Group
Navigate to the EC2 service & the Target groups section.
Click Create target group to configure a new group.
Choose Instances as the target type.
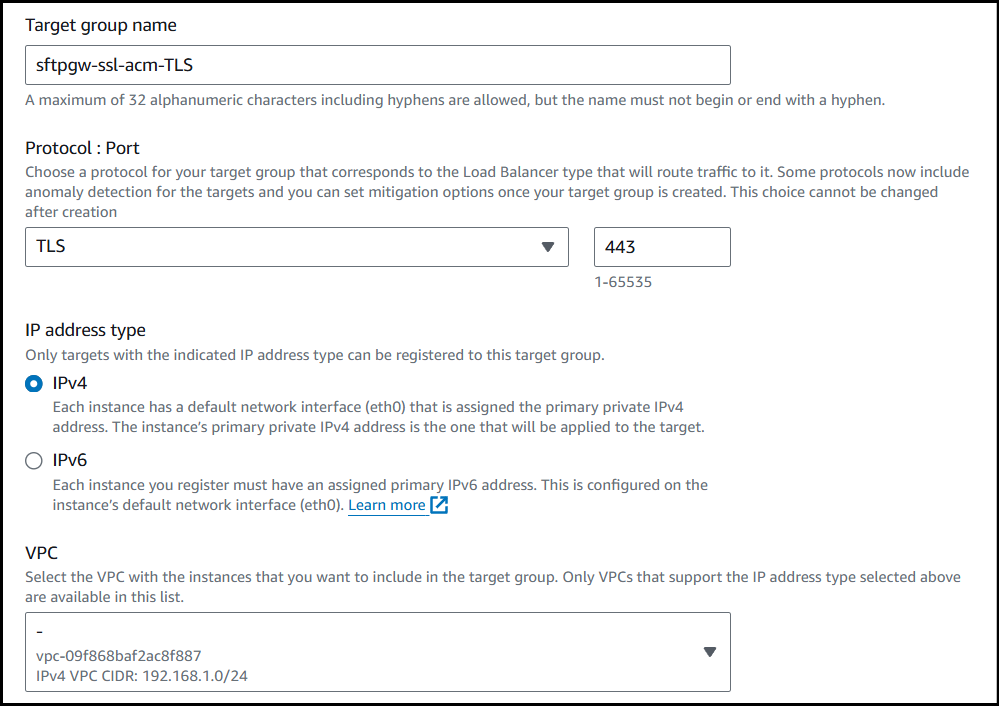
Create a Target group name (put TLS in it).
Set Protocol: Port to TLS on port
443.Choose the VPC where your instances are located.
Set the Health check protocol to HTTPS with a path of /
After configuring the Health checks, at the bottom of the page click Next.
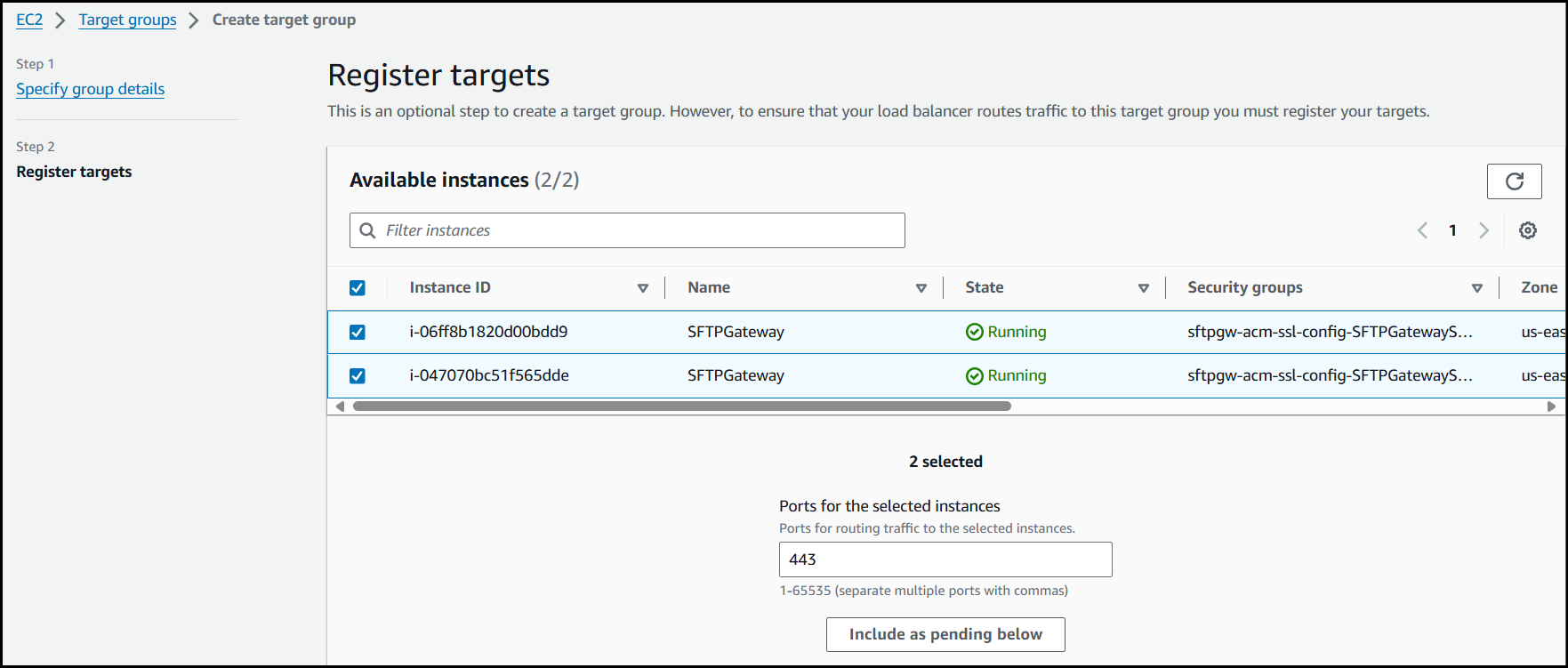
Select the running instances in your Auto Scaling Group and click Include as pending below.
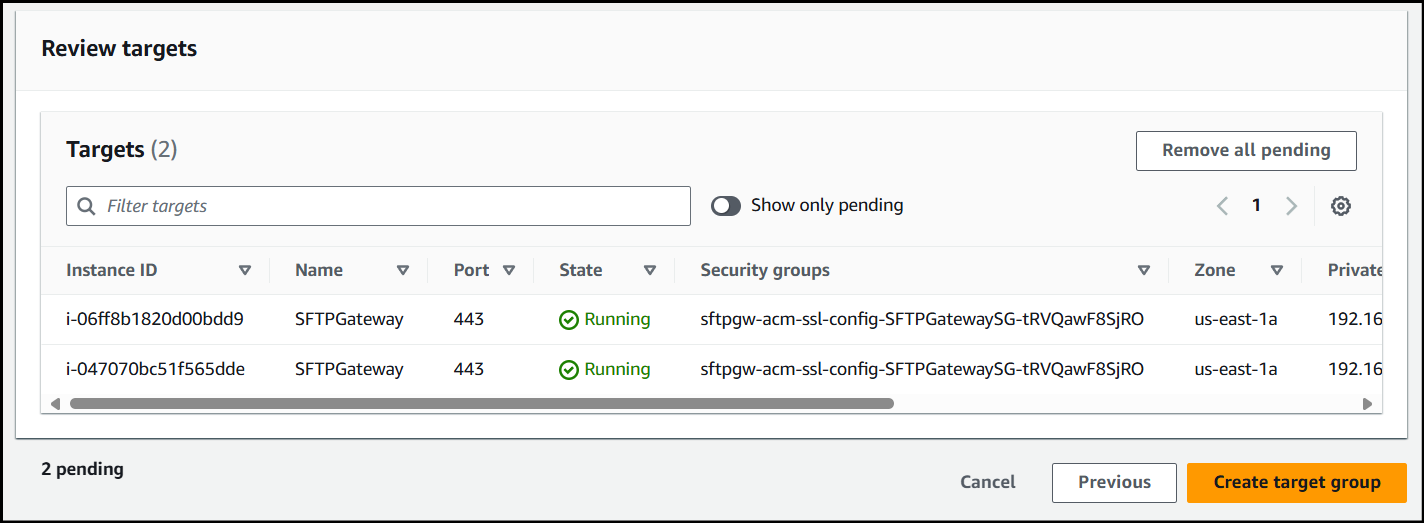
Verify the instances you've selected are in the ASG and click Create target group.
Now that we've created the TLS target group, we need to modify the HTTPS listener on the LB.
Modify the 443 listener on the Load Balancer
Navigate to the EC2 service & the Load Balancer section.
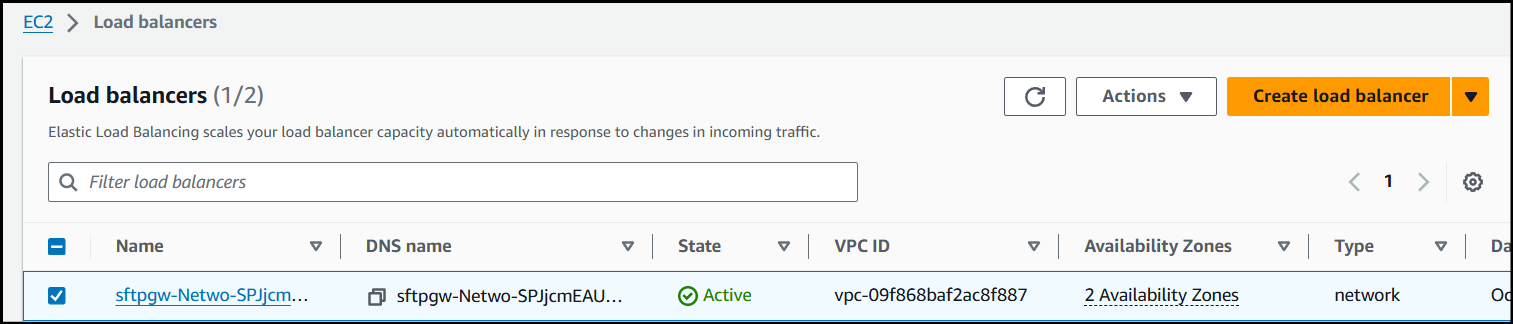
Navigate to the Listeners section on your Load Balancer and edit the TCP listener on port 443.
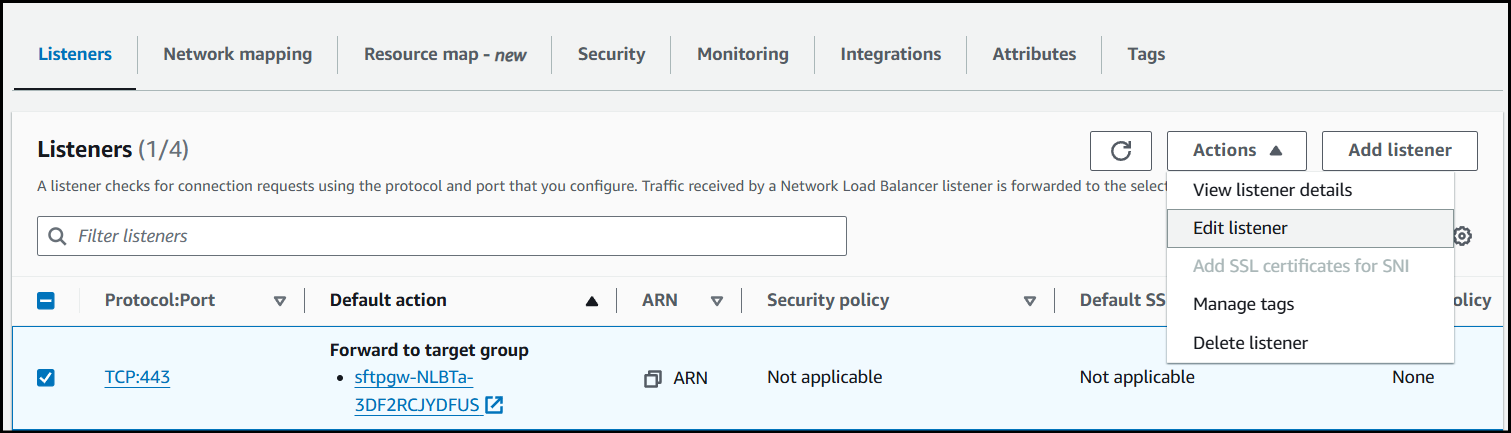
Change the Listener Protocol from TCP to
TLS.Change the Default action to forward to the Target Group created earlier.
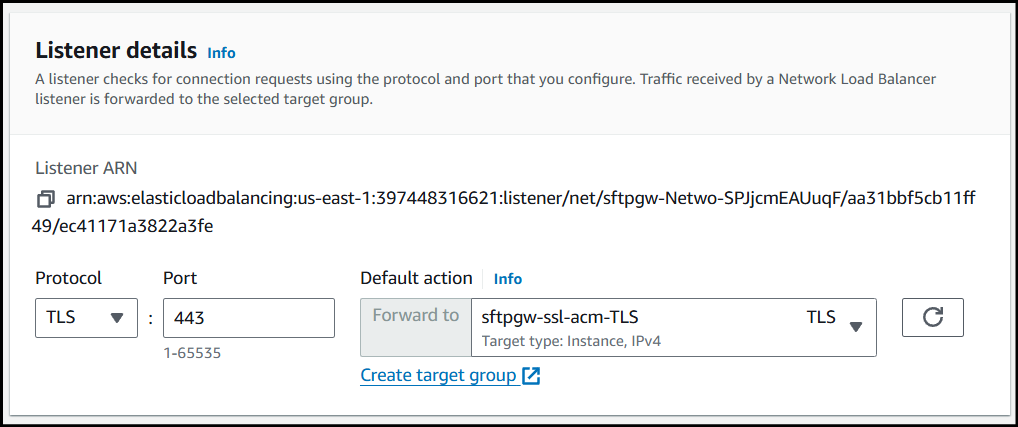
In the Secure listener settings section, set the Default SSL/TLS server certificate to the ACM certificate created in the first step.
After selecting the certificate, at the bottom of the page, click Save changes.
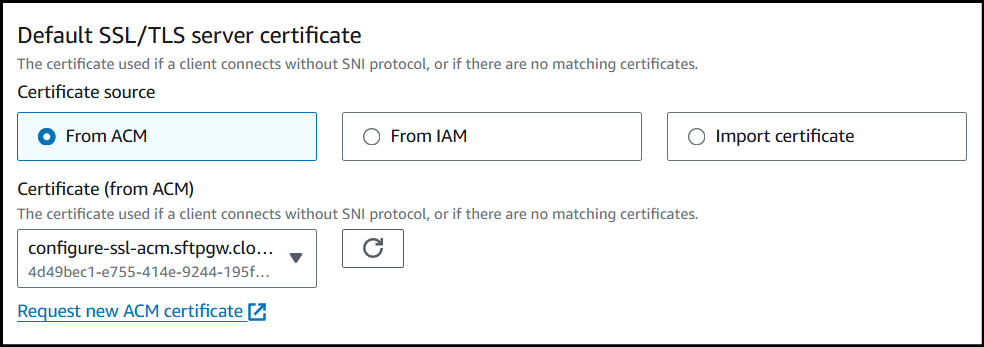
At this point, the SSL certificate should work to secure https access.
Attach the Target Group to the Autoscaling Group
Finally, we need to attach the TLS Target Group to the ASG.
Navigate to the EC2 service & the Auto Scaling groups section.
Open the Auto Scaling group and click Edit on the Load balancing section.
Add the TLS Target Group (bottom group in this example) created earlier to the Application, Network or Gateway Load Balancer target groups section & at the bottom click Update.
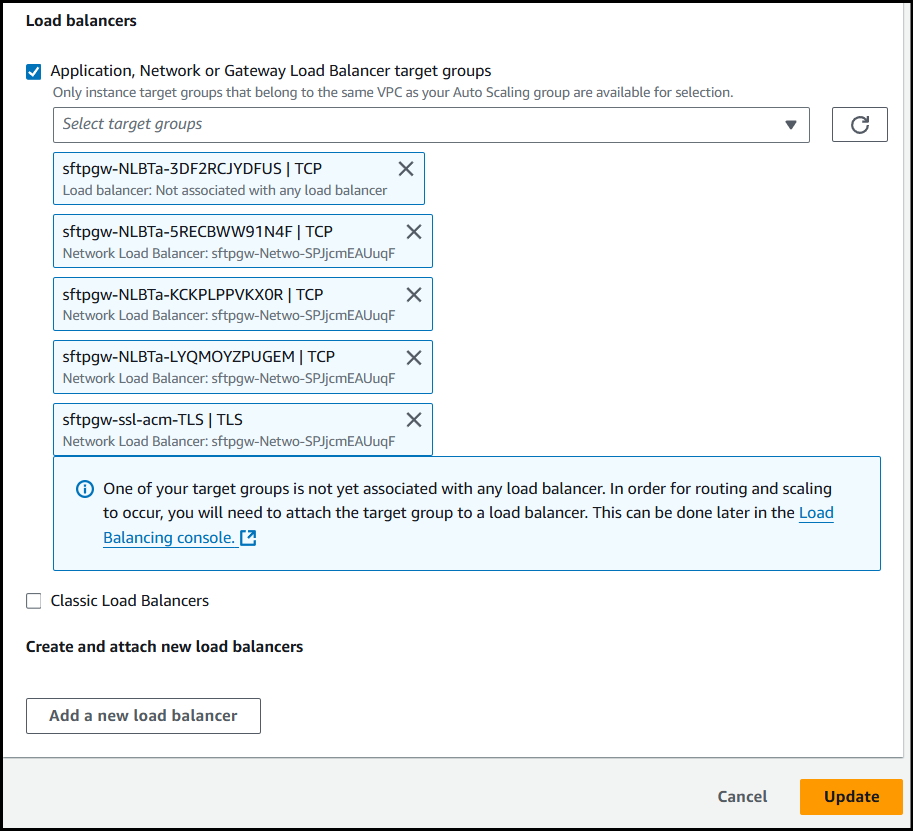
At this point, the SSL certificate is valid and new instances will be valid targets.