Cloud connections
TLDR - Quick Summary
What: Cloud Connection = S3 bucket settings (bucket name, region, encryption, credentials)
Encryption Options: SSE-S3 (managed), KMS (separate key permissions), or No Encryption (bucket default)
Credentials: Instance profile (recommended, auto-rotated) or unique IAM access keys
Usage: Create Cloud Connection, then map Folders to it; multiple Folders can share one Connection
Overview
A Cloud Connection defines a group of settings for connecting to an S3 Bucket.
This includes the S3 Bucket name and prefix.
But it also includes other information like the region, encryption
type, whether you want to use the EC2 instance profile or an AWS access
key/secret.
In order to use a Cloud Connection, you will need to map a Folder to it. A Folder is a logical mapping, similar to a mount point.
This article goes over how to create a new Cloud Connection.
Cloud Connections
A Cloud Connection defines a S3 Bucket destination, and its related settings.
Here is an example of a Cloud Connection:
- S3 Bucket:
s3://rob-test-bucket - S3 Encryption Option:
SSE-S3 - Cloud Connection Credentials: Uses the instance profile credentials
Once a Cloud Connection is defined, you can start creating Folders (every folder must point to a Cloud Connection).
You can point multiple Folders to a single Cloud Connection. This way, the Cloud Connection becomes a single point of change (e.g. you need to rotate an AWS Access key).
Click on Create AWS Connection, and you will see this page:
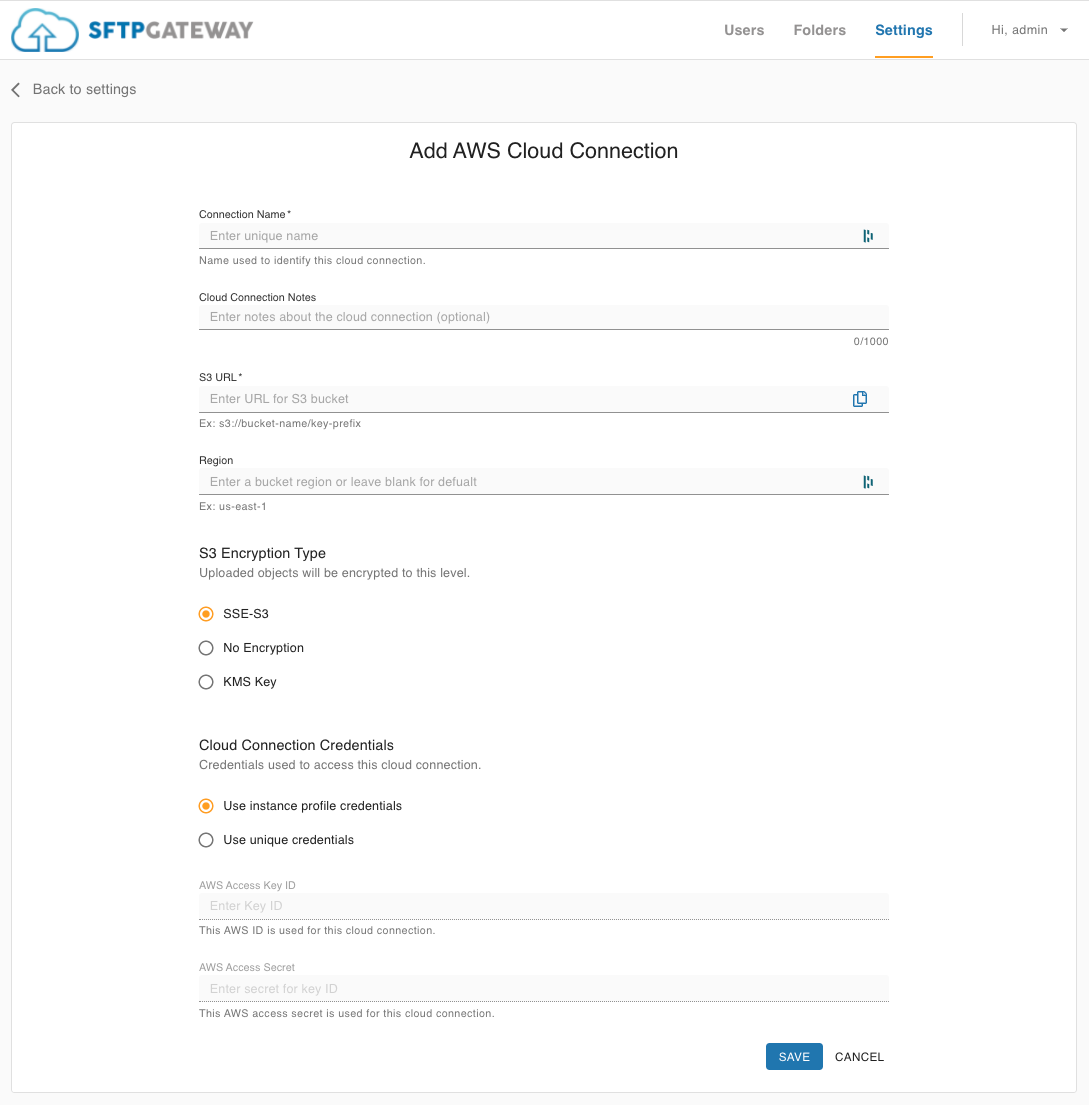
Fill out the following fields:
Connection Name:
A name you define in order to refer to this Cloud Connection.
Cloud Connection Notes:
Optional field for providing more context about this Cloud Connection.
S3 URL:
Enter the S3 Bucket name. Remember to follow the standard S3 Bucket naming convention:
- Has to be globally unique (cannot conflict with S3 buckets in other AWS accounts)
- Lowercase letters (no uppercase allowed), numbers, and hyphens
- Must have fewer than 63 characters
- Only include the S3 bucket (i.e. don't include the folder path)
Region:
The AWS region in which the S3 Bucket is located. If left blank the region of the SFTP Gateway server will be used.
S3 Encryption Option:
S3 objects are encrypted at the time of upload. The encryption method you define on the Cloud Connection will apply to all subsequently uploaded S3 objects.
- SSE-S3: The S3 service manages encryption behind the scenes. S3 objects are encrypted at rest, and the S3 service automatically decrypts the object so long as you have read-access.
- KMS: KMS encryption offers more security value, because KMS key permissions are decoupled from S3 access permissions.
- No Encryption: Do not override encryption settings, so that objects are encrypted using the S3 bucket's default encryption setting.
Cloud Connection Credentials:
The Use instance profile credentials option leverages the IAM permissions on the EC2 instance. This is the recommended approach, because the access key credentials are handled transparently, and rotated for you automatically.
If you want to restrict S3 permissions on a per-user basis, select the Use unique credentials option. You can set AWS Access Key credentials on the Cloud Connection. And then each SFTP can have their own dedicated Cloud Connection.
For creating the unique credentials, refer to this documentation.