Securing Against Latest CVEs
TLDR - Quick Summary
What: Secure SFTP Gateway against latest CVEs (Terrapin Attack, kernel vulnerabilities)
Terrapin Fix: Disable chacha20-poly1305 and ETM MAC algorithms in Security Settings
Updates:
sudo apt update && sudo apt upgrade openssh-server -yandsudo apt upgrade linux-generic -y
Overview
SFTP Gateway should be secure by default, but recent vulnerabilities (CVEs) may require additional configuration changes. This guide identifies which encryption algorithms and settings should be disabled to mitigate known security risks.
Below is an analysis of the highest priority CVEs affecting SFTP security, followed by recommended configuration changes.
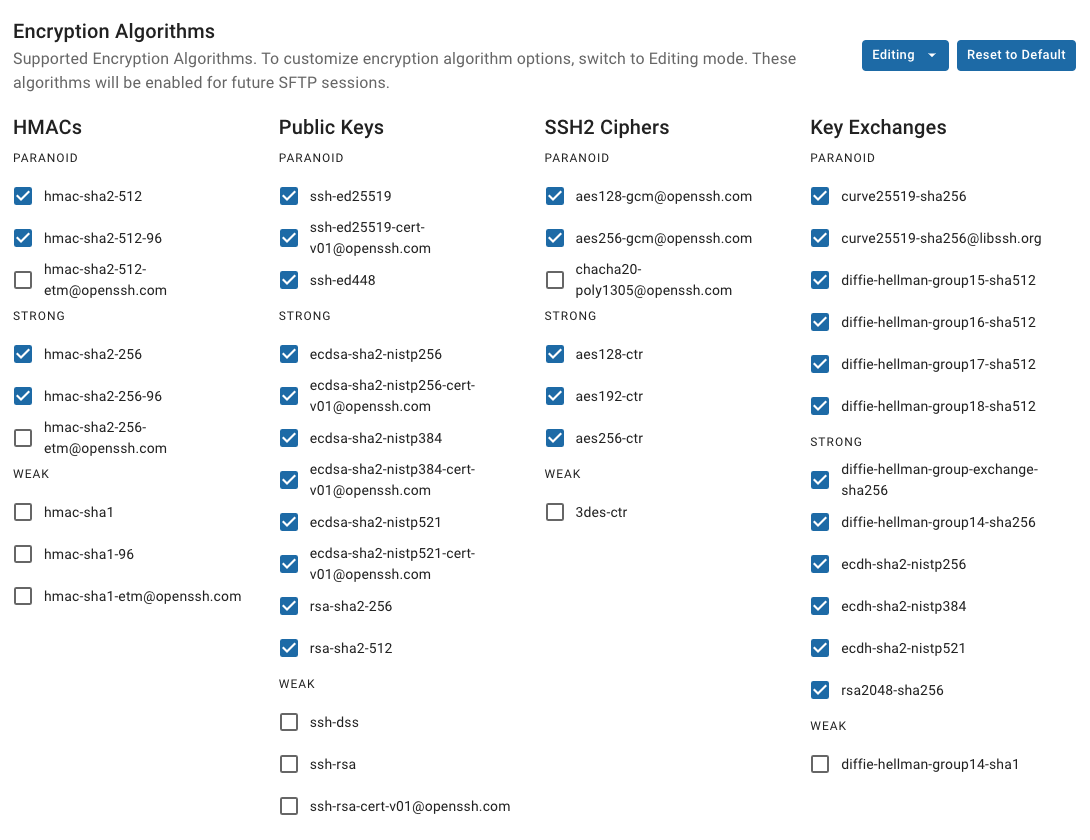
Current Default Security Settings
CVE-2024-6387 – OpenSSH Signal Handling Vulnerability
- Details: This CVE exploits a race condition in OpenSSH’s signal handling, allowing remote unauthenticated attackers to execute arbitrary code.
- Reference: CVE-2024-6387
- Action Required: Ensure OpenSSH is updated to a patched version.
Steps to Update OpenSSH
- Connect to the server via SSH.
- Run the following command:
sudo apt update && sudo apt upgrade openssh-server -y
- Restart the SSH service:
sudo systemctl restart ssh
CVE-2023-48795 – SSH Protocol Vulnerability (Terrapin Attack)
- Details: This CVE describes a vulnerability in certain SSH encryption modes that allow attackers to downgrade encryption security.
- Reference: CVE-2023-48795
Steps to Disable Insecure Algorithms
- Log into the SFTP Gateway admin interface.
- Navigate to Security Settings.
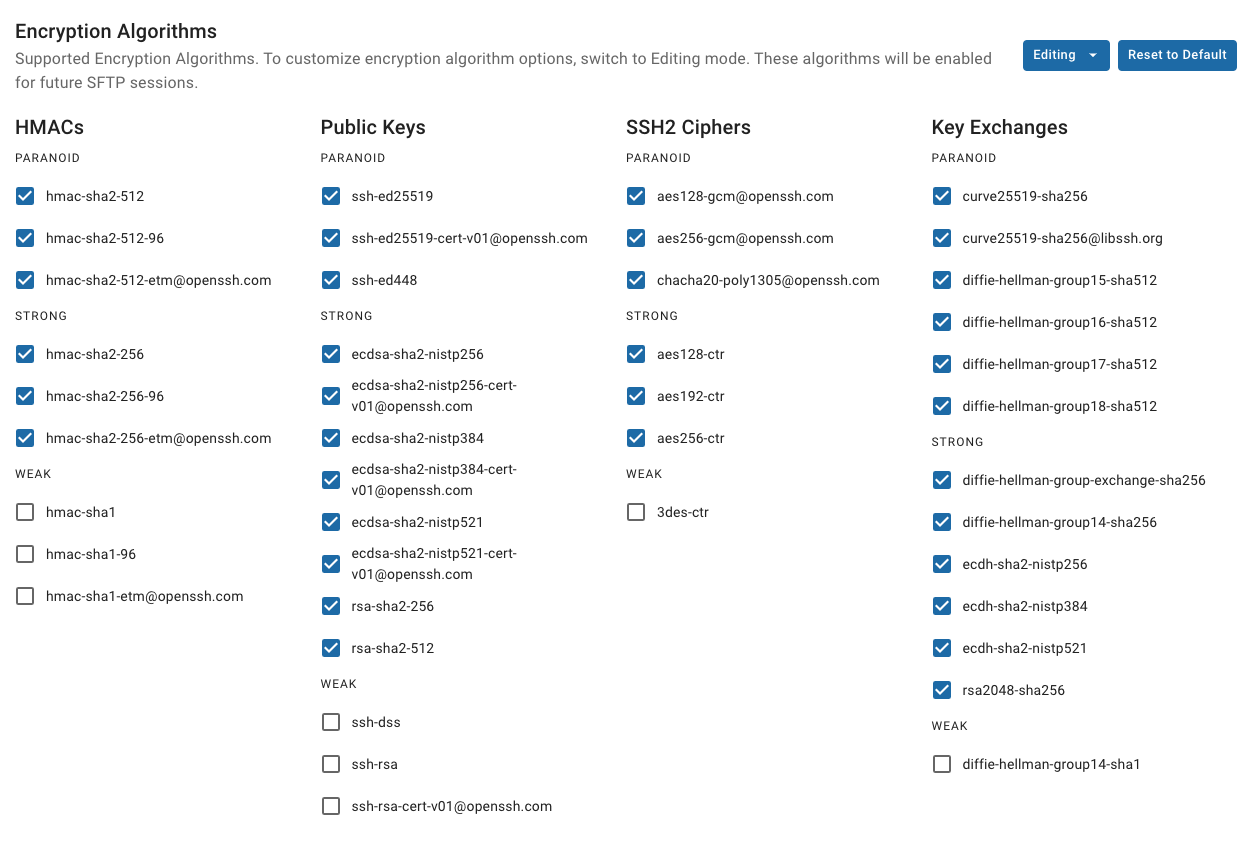
- Uncheck the following algorithms:
- chacha20-poly1305@openssh.com
- hmac-sha2-512-etm@openssh.com
- hmac-sha2-256-etm@openssh.com
- hmac-sha1-etm@openssh.com
- hmac-md5-etm@openssh.com
- Save changes and restart the SFTP service.
Kernel Vulnerabilities
- Details: Multiple kernel-related CVEs have been identified that can impact SFTP Gateway security.
- Reference: Kernel CVEs
- Action Required: Ensure that the Linux kernel is updated to the latest secure version.
Steps to Update Kernel
- Connect to the server via SSH.
- Run the following command:
sudo apt update && sudo apt upgrade linux-generic -y
- Reboot the system to apply changes:
sudo reboot
Final Security Setting