Setting up Instance Identity for SFTP Gateway
TLDR - Quick Summary
What: Use EC2 instance IAM role for S3 access (recommended over access keys)
Note: Already configured if deployed via CloudFormation
Options:
AmazonS3FullAccesspolicy (broad) or custom inline policy (specific buckets)Benefit: Credentials auto-rotated, no keys to manage
Overview
This article goes over how to set up SFTP Gateway to Use instance profile credentials, otherwise known as an Instance Identity.
Cloud Connections can then use this Identity, instead of using unique credentials, which are an AWS Access Key & Secret.
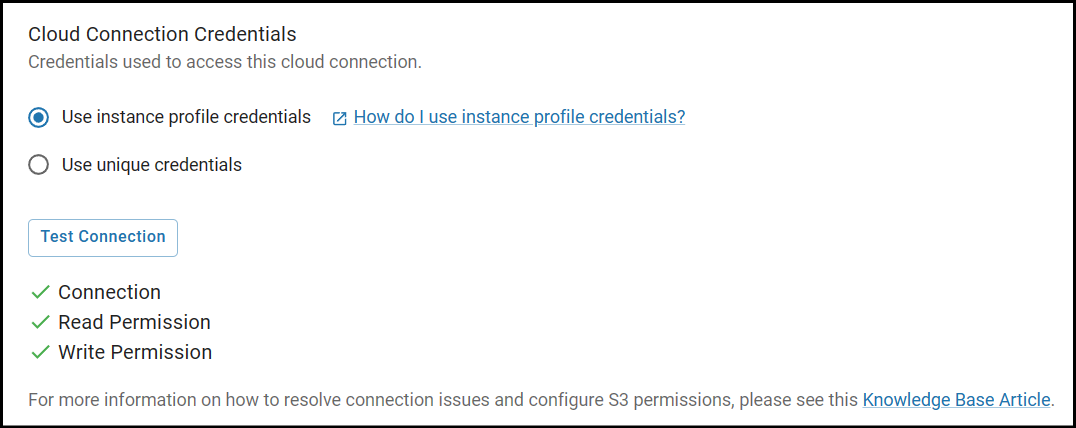
Note: If you deployed SFTP Gateway via our CloudFormation template, Instance Identity is already configured.
Configure Instance Profile Credentials
The permissions for the instance profile credentials are linked to the IAM Role of the instance. Since permissions to S3 are required for SFTP Gateway to function properly, you should always be able to use the instance profile credentials.
However, there are a couple of ways you can go about configuring the IAM Role.
One option would be to grant full access to S3 via the AmazonS3FullAccess policy. This would be ideal for users who aren't particular about having broad permissions to S3 or need to connect to many buckets within their environment.
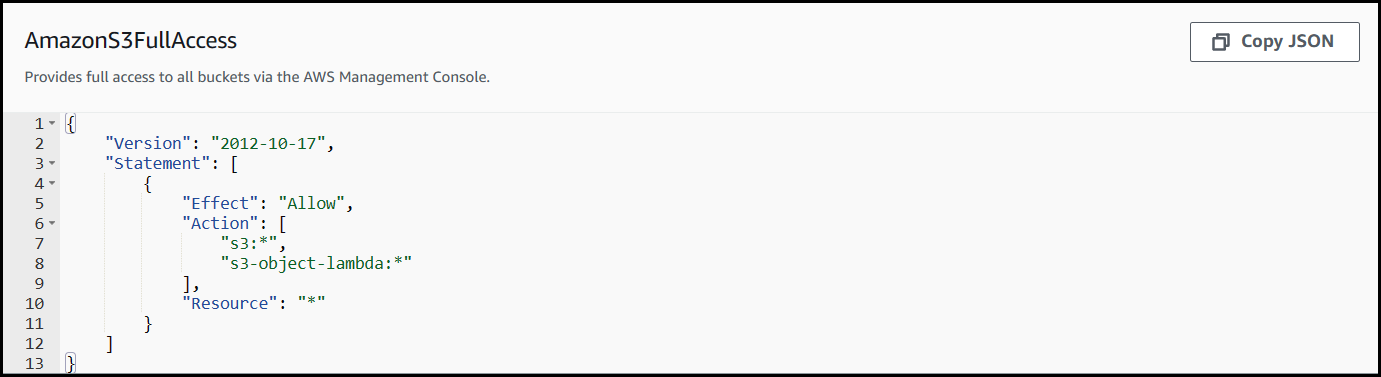
The other option you have would be to grant specific access to S3 for a single, or multiple buckets. This would be ideal for users who want to limit access to S3 and use only the necessary permissions for SFTP Gateway to function properly.
Below is an in-line policy that grants access to a single bucket. Remember to replace your-bucket-name with the value of your actual bucket name and to make this change in two locations.
Attach this policy to an IAM Role to use for your SFTP Gateway instance and you will have permissions to only the bucket(s) specified in the policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket",
"s3:ListAllMyBuckets"
],
"Resource": [
"arn:aws:s3:::your-bucket-name"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::your-bucket-name/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}