Azure AAD Integration with the Web Admin UI
TLDR - Quick Summary
What: Integrate Azure AD authentication with web admin portal (v3.4.0+)
Steps: Create App Registration > Grant users access > Configure Identity Provider in SFTP Gateway Settings
Note: AAD is for web admin only, not SFTP authentication
Overview
With SFTP Gateway v3.004.00, you can now integrate the web admin portal with AAD authentication. In other words, web admins can leverage their existing AAD credentials instead of managing another account just for SFTP Gateway.
Configuring AAD authentication is a process. At a high level, you will be performing three steps:
- Create an App Registration
- Grant users access to this App Registration
- Point SFTP Gateway to the App Registration
Note: AAD cannot be used for SFTP authentication.
Create an App Registration in the Azure Portal
Open the Azure Portal and search for App Registrations.
Click + New Registration. You'll see the following screen:
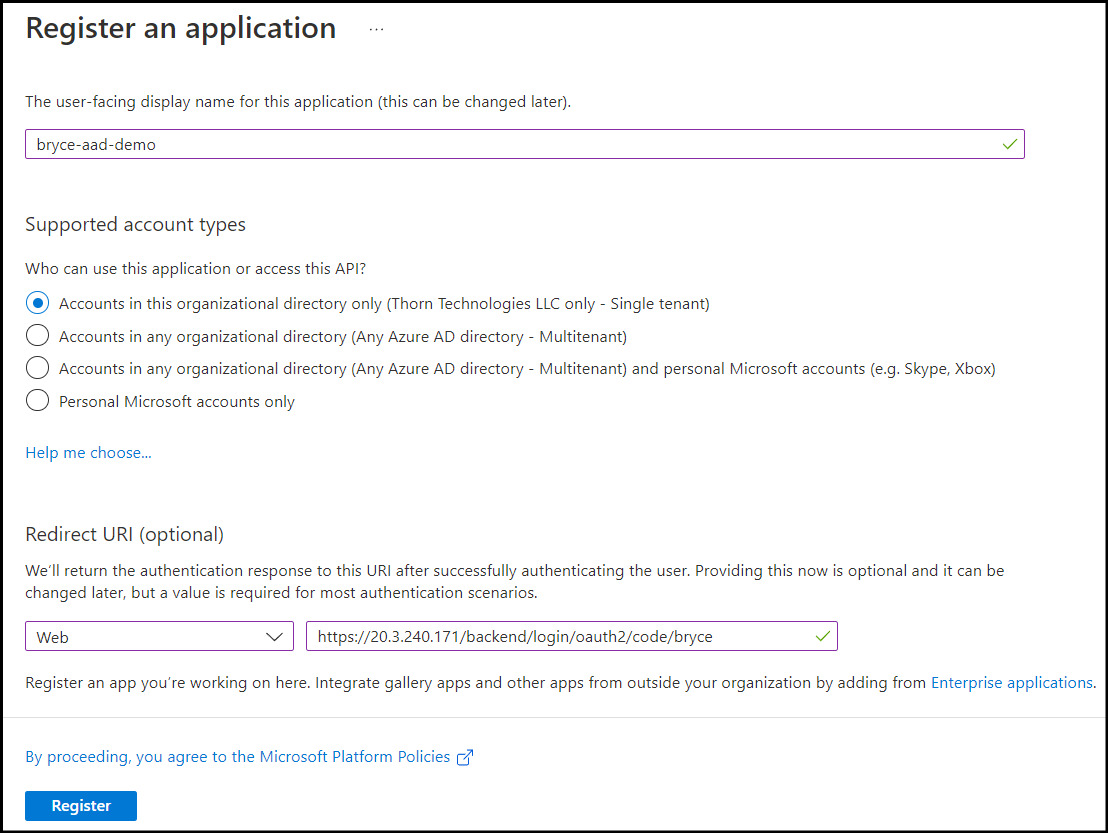
Enter a Name for your App Registration.
For the Redirect URI, choose Web from the drop-down, and paste in the following URL:
https://<sftp-gateway-public-ip>/backend/login/oauth2/code/<custom name>
Note: If you're using a hostname instead of an IP address for the Web Interface, use that value instead.
The custom name can be any value you'd like, but make sure to write it down, as you'll need it later on.
Once everything has been configured, click Register.
Add users to your application.
In the Azure Portal, go to Enterprise applications.
By default, all users in your Azure Active Directory will have access and be able to log in with their Azure credentials to SFTP Gateway. If you would like to configure access so that only select users or groups have permissions, follow the instructions below.
Once inside Enterprise applications, search for your App Registration's name that you created earlier.
Click on your Application.
Navigate to the Properties section on the left sidebar. Set Assignment required? to Yes, and then at the top, click Save. This will make it so any user or group not specifically added to the Application is denied access.
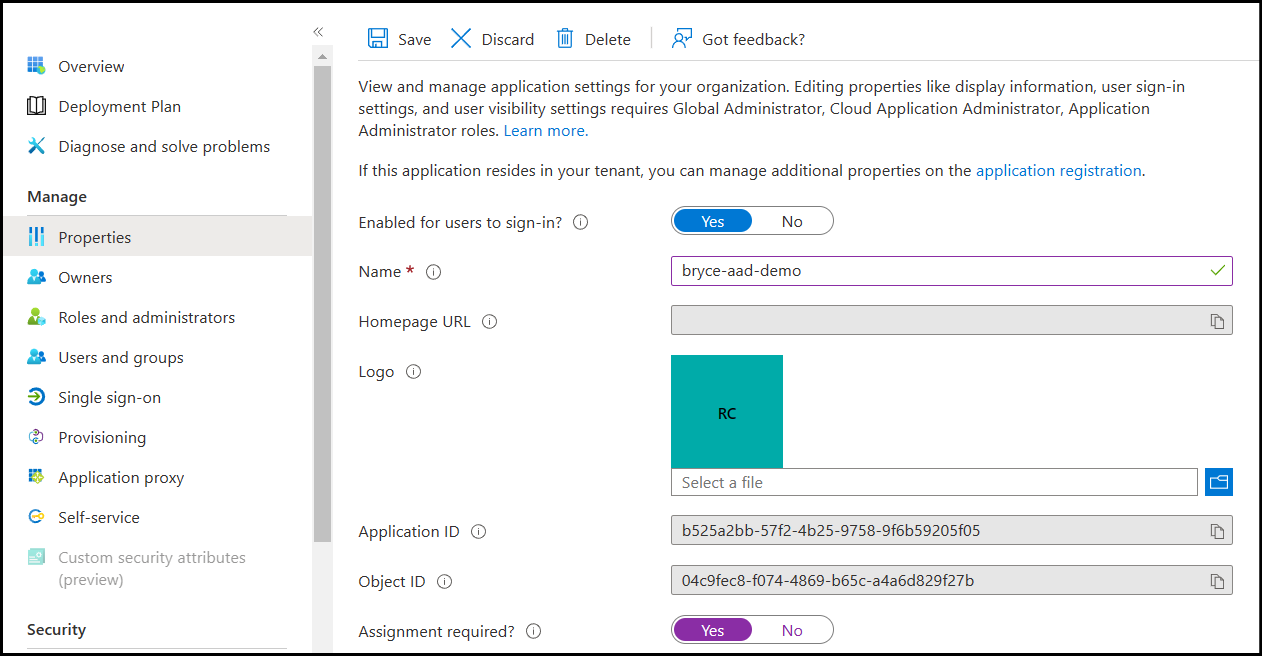
On the left, click on Users and Groups.
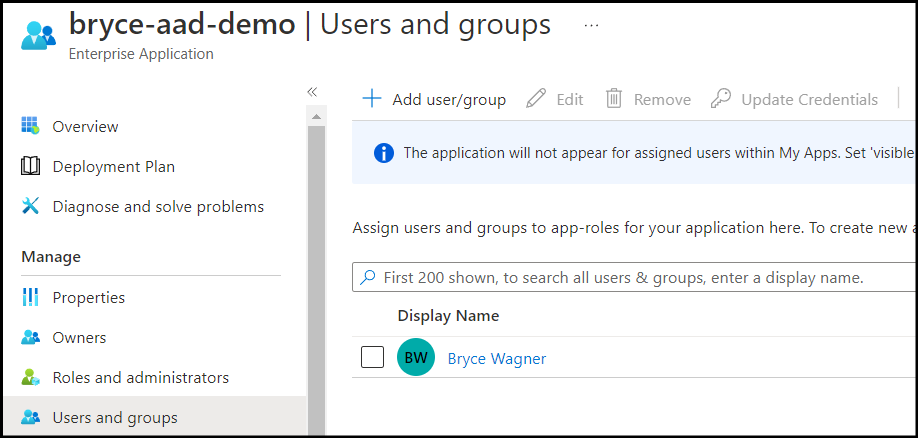
Click on + Add user/group.
You will see an Add Assignment page. Select the users that you wish to grant access, and then click Assign.
Get App Registration IDs
For the final step to get everything working, SFTP Gateway needs the App Registration IDs.
In the Azure Portal, go back to App Registrations.

Click on the App Registration that you created earlier.
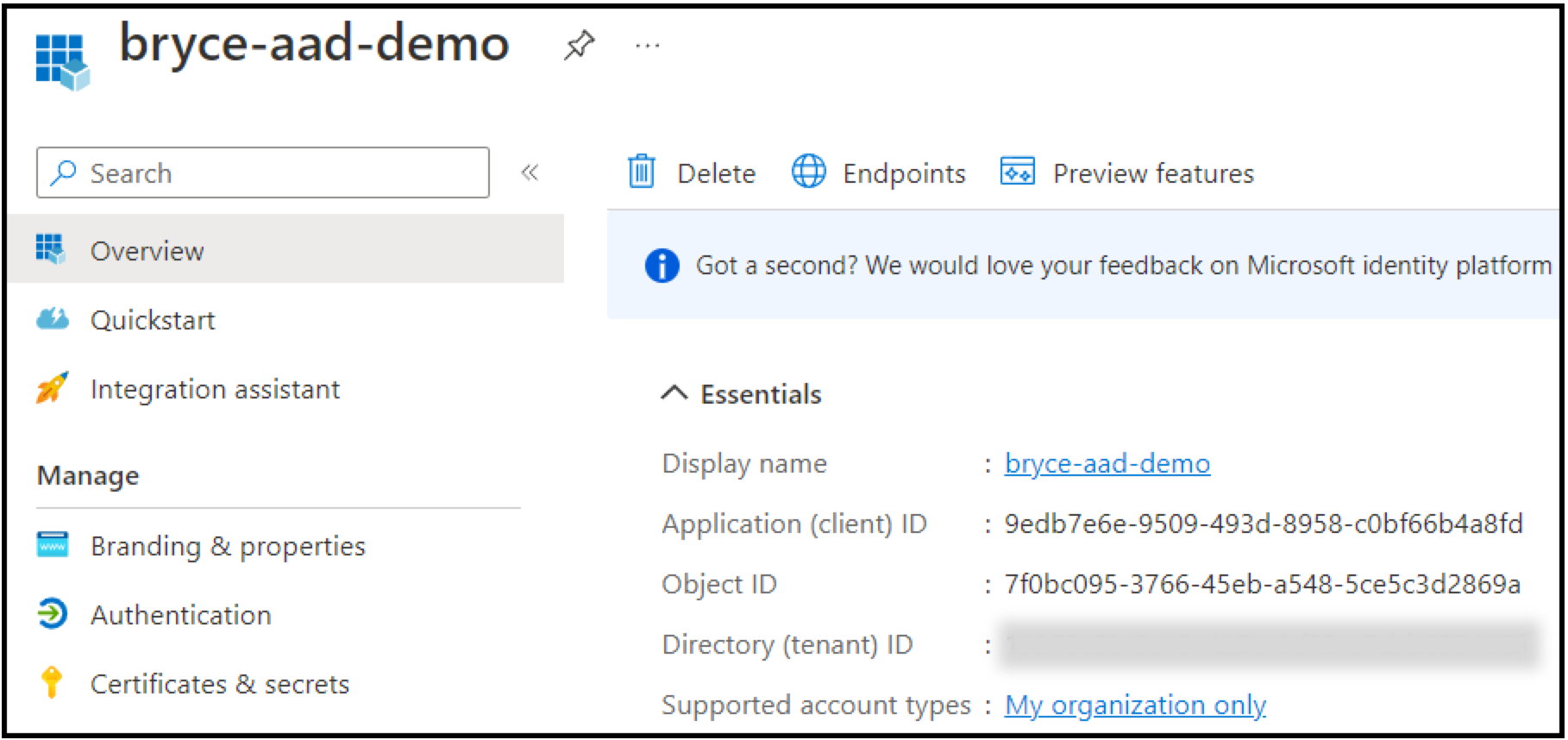
On the Overview page, copy and store the Application (client) ID and the Directory (tenant) ID. You will need these values later when creating the Identity Provider in SFTP Gateway.
On the Certificates & secrets page, under Client secrets, click + New client secret.
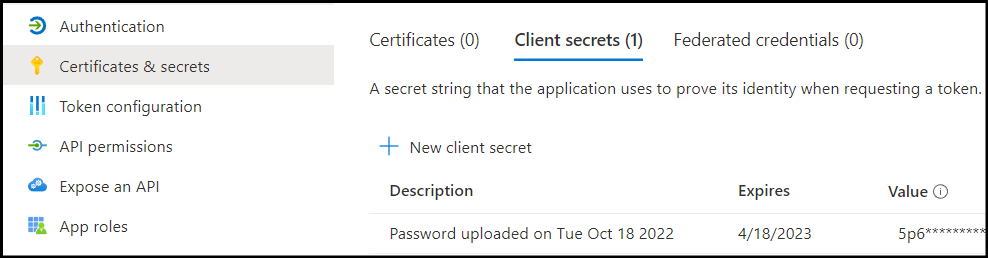
Copy the Value of the new client secret and store it, as you will need it in the next section.
Configure the Identity Provider on SFTP Gateway
In the SFTP Gateway web admin portal, go to Settings.
Under Identity Providers, click Add new IdP.
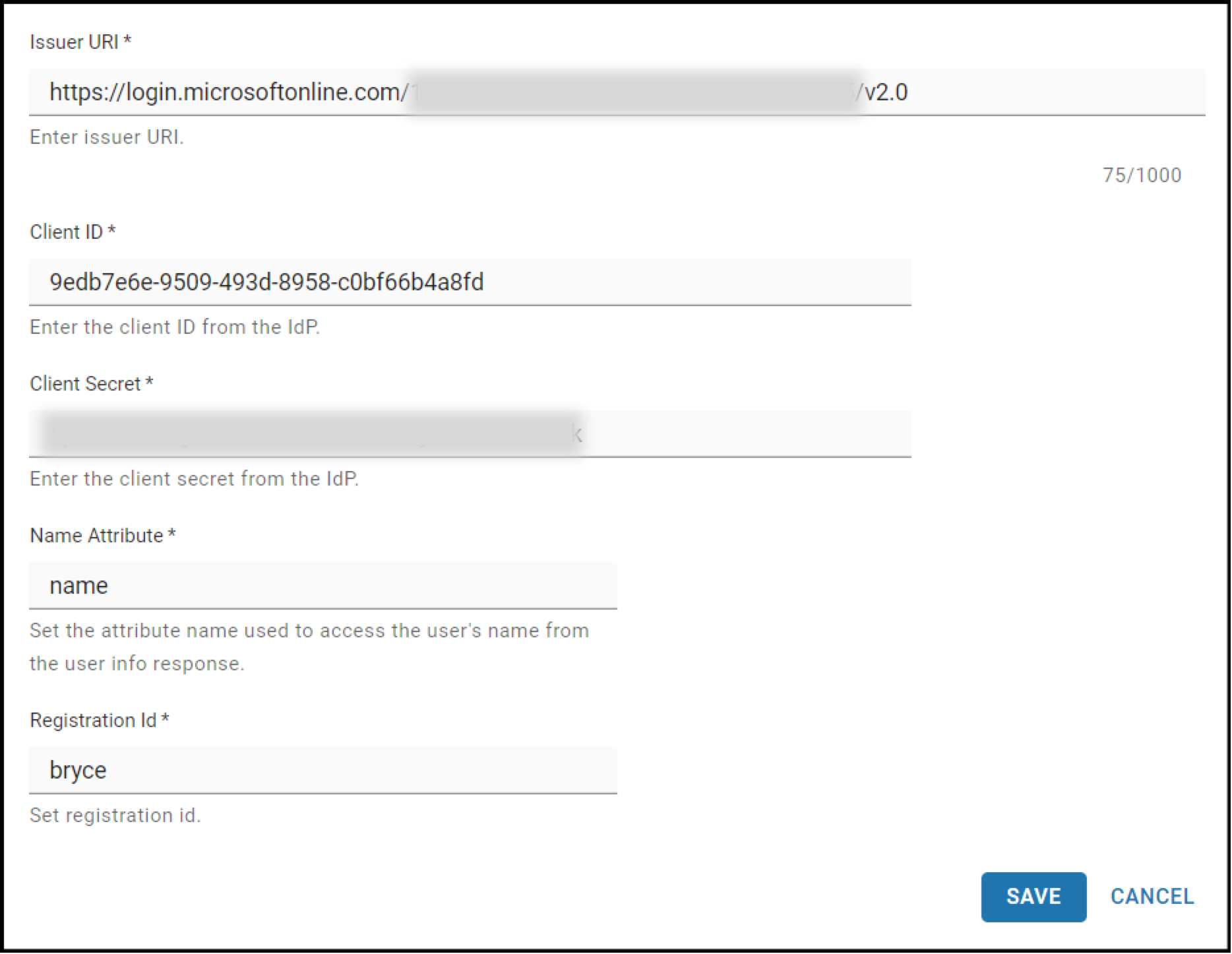
For the new Identity Provider, fill in the following fields:
Identity Provider Display Name: This is the name for the Identity Provider that will be displayed at the login screen for Web Admin Users.
Issuer URI: Paste in this text
https://login.microsoftonline.com/{TENANT_ID}/v2.0. Replace the placeholder value with the tenant ID you copied earlier from the overview page of the App Registration.Client ID: Paste in the client ID you copied earlier from the overview page of the App Registration.
Client Secret: Paste in the client secret value you copied earlier from the Client secrets page.
Name Attribute: Set this value to
name.Registration ID: Use the custom name you made for the Redirect URI when creating the Registration App.
Scopes: Set this value to
openid.
Test the changes in the web browser
If you are logged into the web admin UI, click the logout button on the top right.
Refresh the browser.
On the login page, you should see the Display name for your Identity Provider.

You will be redirected to login.microsoftonline.com to enter your
AAD credentials.
Once logged in, you will be authenticated to the SFTP Gateway web admin portal.