Deploy SFTP Gateway on EKS - Beta
TLDR - Quick Summary
What: Deploy SFTP Gateway as containerized app on Amazon EKS (Beta)
Prerequisites: AWS CLI v2, eksctl, kubectl, Helm v3
Steps: Create EKS cluster, install AWS Load Balancer Controller, apply Kubernetes manifest
Access: Sign up for Beta at https://thorntech.com/containerized-sftp-gateway-beta
Sign up for SFTP Gateway Beta
This documentation is intended for Beta customers and is not suitable for Production implementation, use it at your own risk. These are reference templates that are meant for demonstration purposes only, intended to show you how you can get started with container deployment. To gain access to our public ECR images and license key mentioned in the documentation, sign up for our Beta program.
Use this form to sign up for our Beta program:
https://thorntech.com/containerized-sftp-gateway-beta
Overview
In this article we'll walk through deploying SFTP Gateway as a containerized application on EKS. This involves creating an EKS cluster and applying your manifest to the cluster nodes to get the application up and running.
Afterwards, you're able to access your deployment by navigating to your web browser and creating your initial Web Admin account.
Prerequisites
Before starting, ensure you have the following tools installed:
- AWS CLI v2: Installation guide
- eksctl: Installation guide
- kubectl: Installation guide
- Helm v3: Installation guide
Verify installations:
aws --version # Should be >= 2.15
eksctl version # Should be >= 0.100
kubectl version --client
helm version # Should be >= 3.0
Create the EKS Cluster
The first step is to create the EKS cluster.
Create the cluster config file on your local machine and run the command to create the EKS cluster (This can take up to 20 minutes to create):
eksctl create cluster -f eks-cluster.yaml
Here is the content of the eks-cluster.yaml file:
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: sftpgateway-cluster
region: us-east-1
version: "1.32"
iam:
withOIDC: true
managedNodeGroups:
- name: sftpgateway-nodes
instanceType: t3.large
desiredCapacity: 2
minSize: 1
maxSize: 4
volumeSize: 50
iam:
withAddonPolicies:
imageBuilder: true
autoScaler: true
externalDNS: true
certManager: true
appMesh: true
ebs: true
fsx: true
efs: true
albIngress: true
cloudWatch: true
cloudWatch:
clusterLogging:
enableTypes: ["audit", "authenticator", "controllerManager"]
addons:
- name: vpc-cni
- name: coredns
- name: kube-proxy
- name: aws-ebs-csi-driver
Once the EKS Cluster is created, we want to update our kubectl configuration to connect to the new cluster as it doesn’t know it exists or how to connect to it by default.
We do this so we can get a status of the current nodes in our cluster:
aws eks update-kubeconfig --region us-east-1 --name sftpgateway-cluster
Afterwards, we can get the status on the nodes in the cluster:
kubectl get nodes
Create Load Balancer Controller
Now that the EKS Cluster has created, we'll first create an IAM Service Account for the LB Controller to have permissions to provision the Load Balancer:
eksctl create iamserviceaccount --cluster=sftpgateway-cluster --namespace=kube-system --name=aws-load-balancer-controller --role-name=AmazonEKSLoadBalancerControllerRole --attach-policy-arn=arn:aws:iam::aws:policy/ElasticLoadBalancingFullAccess --attach-policy-arn=arn:aws:iam::aws:policy/AmazonVPCFullAccess --approve
Add an AWS EKS Helm Repository to install the EKS LB controller:
helm repo add eks https://aws.github.io/eks-charts
helm repo update
Install AWS Load Balancer Controller (Without this you won’t be able to connect to the nodes):
helm install aws-load-balancer-controller eks/aws-load-balancer-controller -n kube-system --set clusterName=sftpgateway-cluster --set serviceAccount.create=false --set serviceAccount.name=aws-load-balancer-controller
Verify the Installation:
kubectl wait --for=condition=ready pod -l app.kubernetes.io/name=aws-load-balancer-controller -n kube-system --timeout=300s
kubectl get deployment -n kube-system aws-load-balancer-controller
Manifest customization
To deploy our complete application containing the database, backend and admin-ui images, we want to apply the manifest file to the cluster nodes.
Create the following manifest file on your local machine (see the file contents at the bottom of the page).
Note: To obtain the ECR images & custom license key, make sure to sign up for our Beta program: https://thorntech.com/containerized-sftp-gateway-beta
Before applying the manifest, make the following changes to the sftpgateway-config section:
---
apiVersion: v1
kind: ConfigMap
metadata:
name: sftpgateway-config
namespace: sftpgateway
data:
SPRING_PROFILES_ACTIVE: "production"
LOGGING_LEVEL_ROOT: "INFO"
SPRING_DATASOURCE_URL: "jdbc:postgresql://postgres-service:5432/sftpgw"
SPRING_DATASOURCE_USERNAME: "sftpgw"
SECURITY_CLIENT_ID: "1234"
SERVER_PORT: "8080"
HOME: "/home/sftpgw"
FEATURES_INSTANCE_CLOUD_PROVIDER: "aws"
BACKEND_URL: "http://backend-service:8080/"
SFTP_PORT: "2222"
CLOUD_PROVIDER: "aws"
---
Add the following variables below the CLOUD_PROVIDER: "aws" variable to configure your connection to your S3 Bucket:
FEATURES_FIRST_CONNECTION_NAME: "S3 Bucket Cloud Connection"
FEATURES_FIRST_CONNECTION_REGION: us-east-1
FEATURES_FIRST_CONNECTION_BASE_PREFIX: "my-s3-bucket-name"
For locking down Web UI & SFTP Access, modify the following line (This line exists in two locations, once under the sftp-service which controls access over SFTP/port 22 and once under the frontend-service which controls access to the Web Interface. By default both services are accessible to the world):
service.beta.kubernetes.io/aws-load-balancer-source-ranges: "0.0.0.0/0"
Additionally, the built-in license included in the backend image only supports 5 SFTP users. If you want to increase the limit, this can be achieved by adding a new environment variable under sftpgateway-config:
Note: To obtain the custom license key (The license expires in September 2026), make sure to sign up for our Beta program: https://thorntech.com/containerized-sftp-gateway-beta
LICENSE: [Sign up for our Beta program to get the license key]
Apply the Manifest
Once your manifest file is ready, we can run this command to apply the manifest to the worker nodes:
kubectl apply -f sftpgw-manifest.yaml
we can monitor the status of the deployment with the following command (This will tail the logs of the backend node and this process can take up to 10 minutes):
kubectl rollout status deployment/backend -n sftpgateway
Access your deployment
Once you see the application is in a ready state, you can obtain the external IPs of the front-end for Web UI access and the backend for SFTP access:
kubectl get services -n sftpgateway -o wide
The output will look something like this (Use the External IP of the frontend-service to connect to the Web Interface and use the External IP of the sftp-service for connecting via SFTP over port 22):
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
backend-service ClusterIP 10.100.203.13 8080/TCP 27m app=backend
frontend-service LoadBalancer 10.100.41.207 k8s-sftpgate-frontend-0322e8c481-6ea4c7c6026a7536.elb.us-east-1.amazonaws.com 80:32590/TCP,443:31395/TCP 27m app=frontend
postgres-service ClusterIP 10.100.143.212 5432/TCP 27m app=postgres
sftp-service LoadBalancer 10.100.168.234 k8s-sftpgate-sftpserv-6dd8490a3e-57033d92a97db05a.elb.us-east-1.amazonaws.com 22:31821/TCP 27m app=backend
Once your container has deployed successfully, access it by navigating to the External IP of the frontend-service on a web browser.
Setting up SFTP Gateway
After accessing the Web UI, create your initial Web Admin account & Sign in:
Even though the initial Cloud Connection is automatically configured with bucket/container details, you'll need to specify valid credentials.
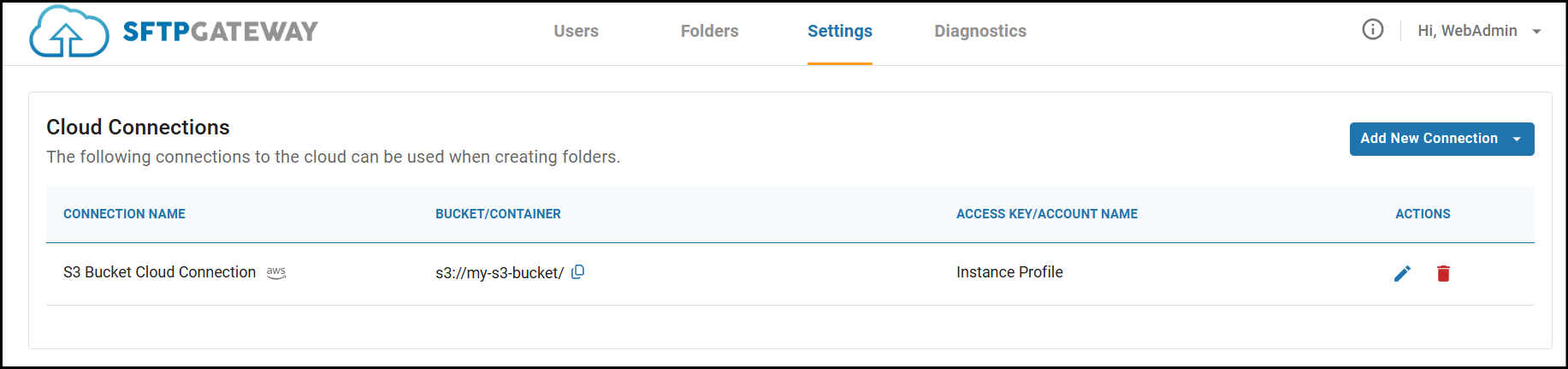
Here is documentation going over how to obtain the credentials for your S3 Bucket:
AWS S3 Bucket Credentials - AWS Documentation for the Access Key ID & Secret Access Key ID
Once your connection has been configured and returns 3 green check marks for the Test Connection, navigate to the Users tab and create first your SFTP user:
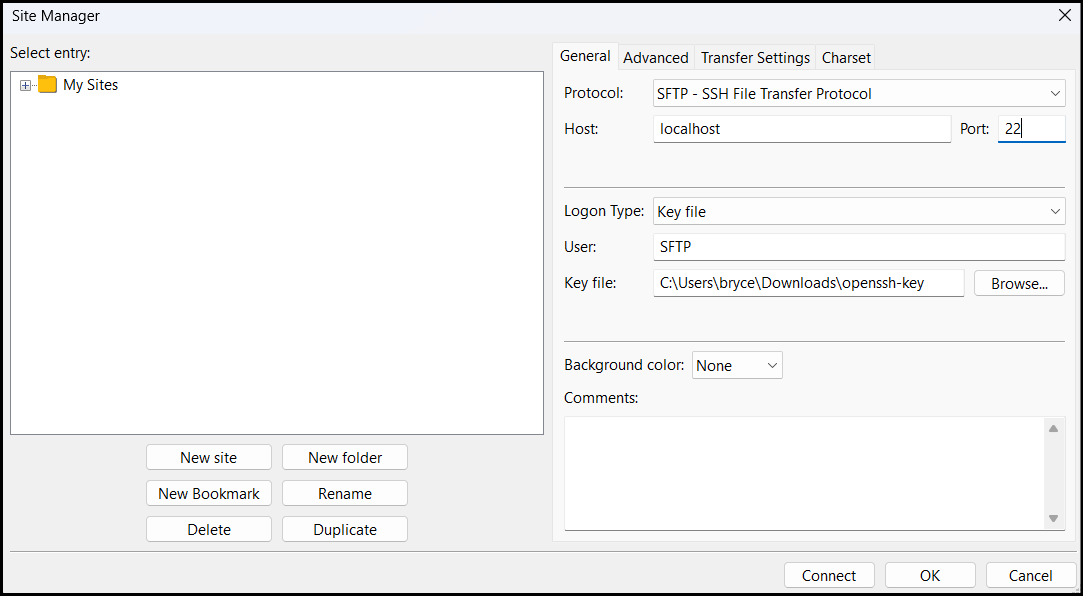
Once created, connect with your SFTP user from an SFTP client such as FileZilla:
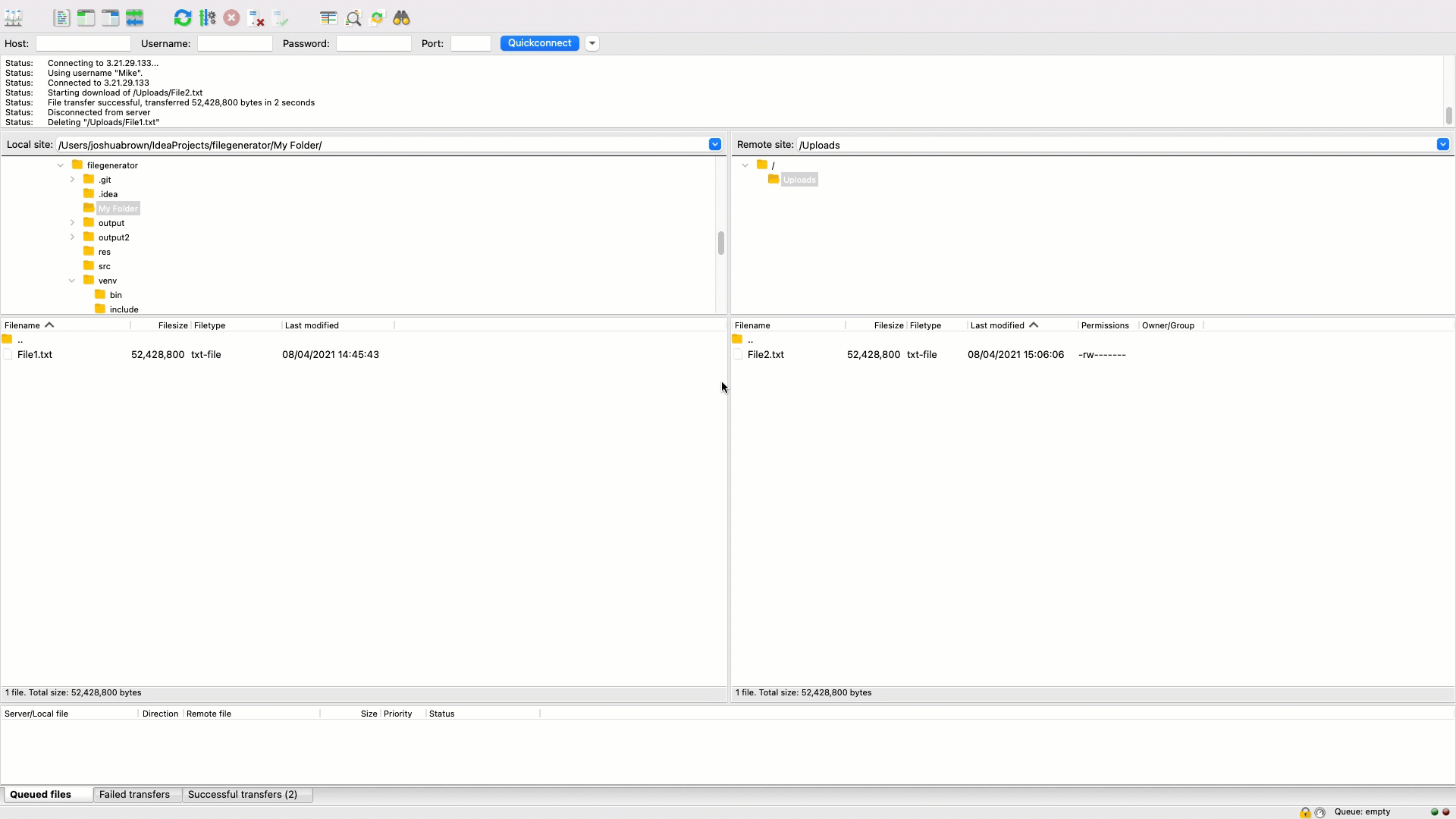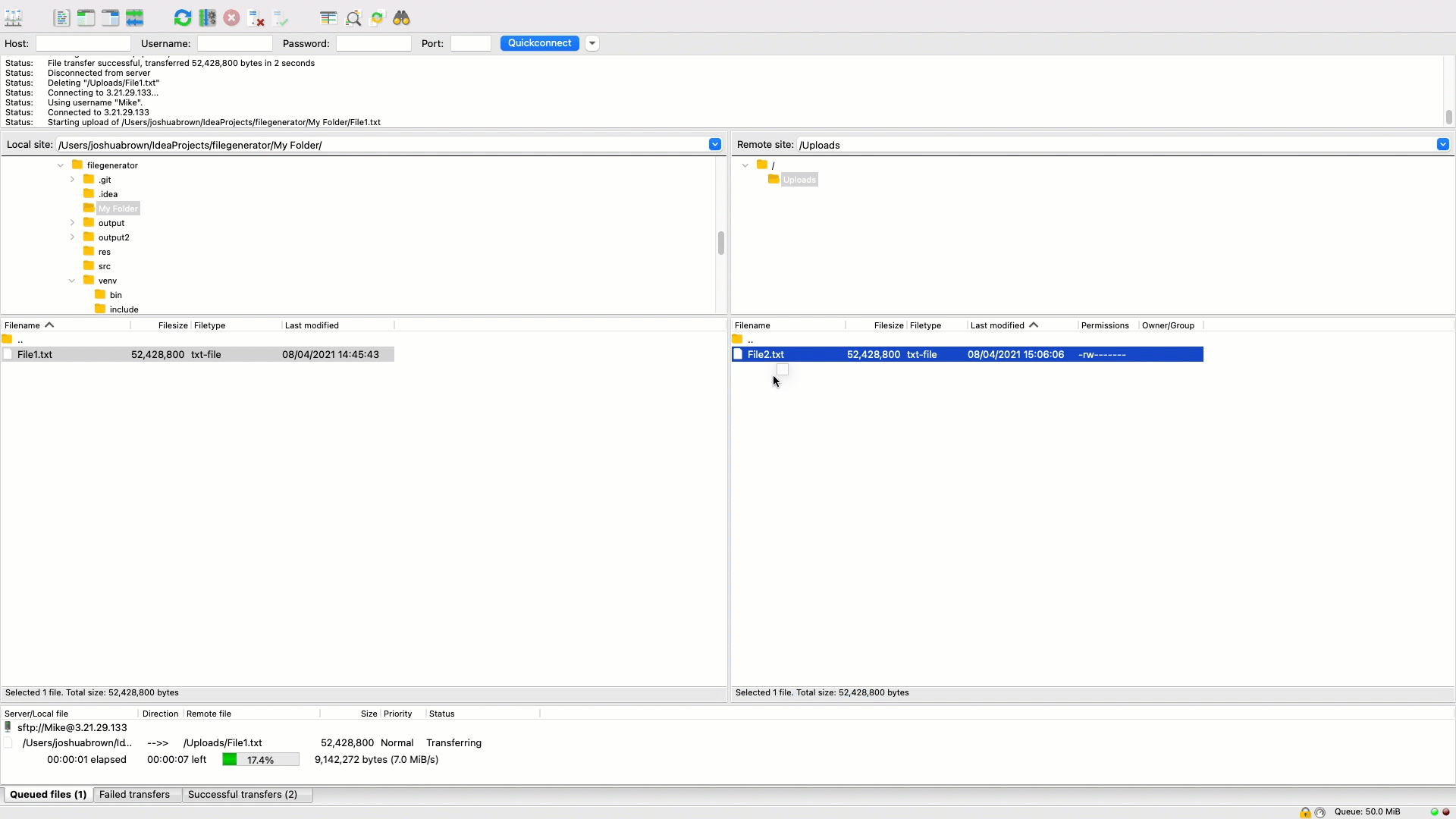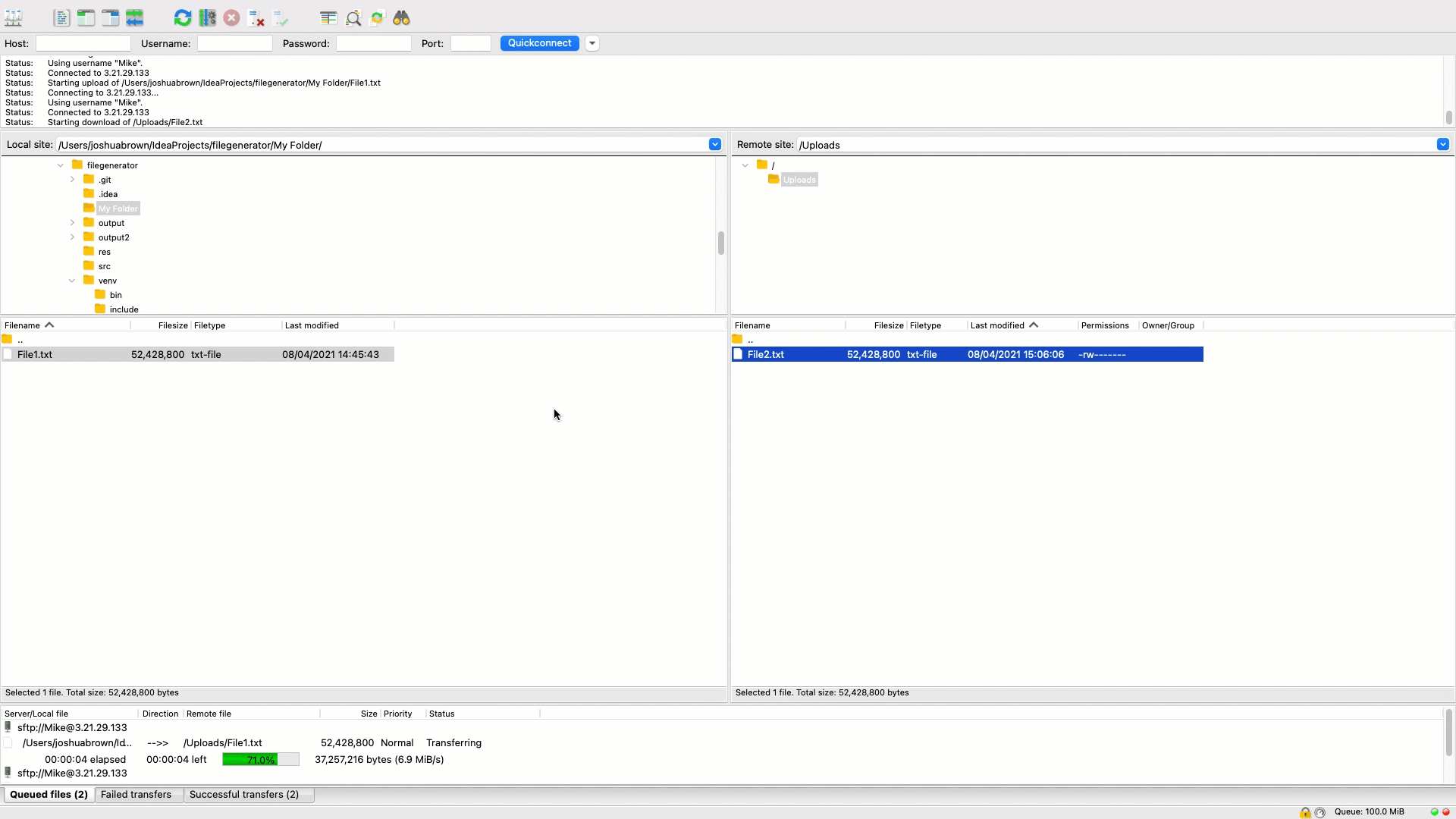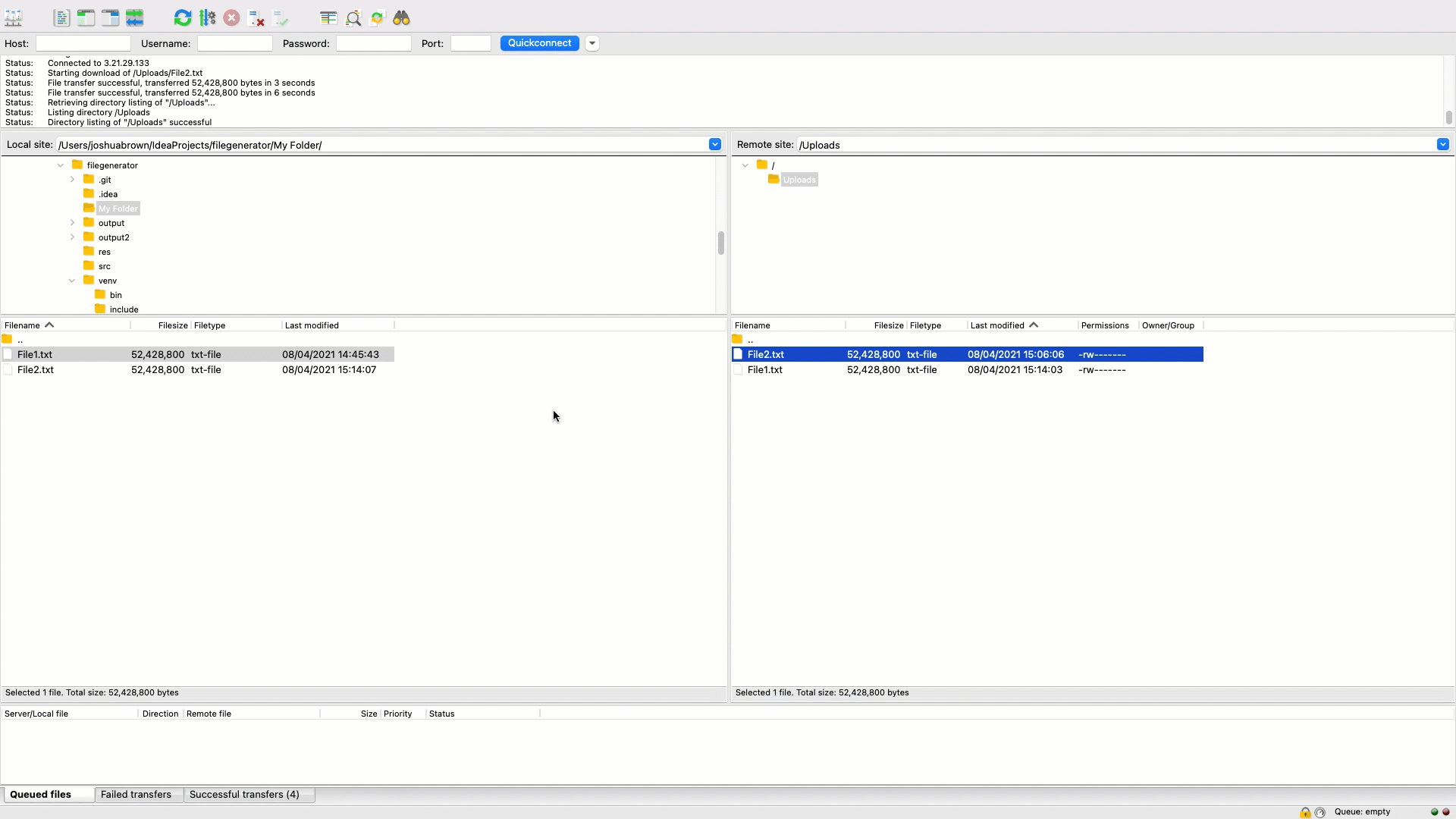
Upload a file to your Cloud Storage Location:
That's it, you've now successfully deployed SFTP Gateway in a containerized version and are connected to Cloud Storage.
Manifest File Contents
Here is the content of the sftpgw-manifest.yaml file:
apiVersion: v1
kind: Namespace
metadata:
name: sftpgateway
---
apiVersion: v1
kind: ConfigMap
metadata:
name: sftpgateway-config
namespace: sftpgateway
data:
SPRING_PROFILES_ACTIVE: "production"
LOGGING_LEVEL_ROOT: "INFO"
SPRING_DATASOURCE_URL: "jdbc:postgresql://postgres-service:5432/sftpgw"
SPRING_DATASOURCE_USERNAME: "sftpgw"
SECURITY_CLIENT_ID: "1234"
SERVER_PORT: "8080"
HOME: "/home/sftpgw"
FEATURES_INSTANCE_CLOUD_PROVIDER: "aws"
BACKEND_URL: "http://backend-service:8080/"
LICENSE: lv3LLsZmfbLD/Yl51PE72rQWPI1dRRd5bGRAv4eqAZ/Dhq1iKPE1CCH/9rvPZigKim8H6Khsr/xHdqfuXKwGGNR7YM7MT8P6E8SG1Ip94eYuS5UyEL5zQf4WBpUNbliN0YKbpOqWJJjz91mrFB0MOcgz/8blCr06f5xskilb51YOo5fFxm2/TaTtJ+apZD0xPuk7HAUgh4V3bfy9OzqD4CHRCoWHueH8vdE8vbQzWqGJhzcyBEyN1y8CNaG4MZaJu8r/kuAkN9rCV+/NGuNomu5XunUFNEWgMMF0zBSJq//W5Ct7omQjXzUKmFc82VrdcHERZ2TgkMOKNuJYR2P6BQ==|DJbizLP/7l3i8xK+ByrKi+VDCjrtwtb1lsN6mB0MVHhr5ipTbHWK/cc+Omq6zdfQUZKN5LCZaC1+vQVHNx5Nfp4hZ4QUc0KbRWGr9s+aLVhw9f8/W/YC9waQm8jWs/BvkdRhpvzh/+gIDfNm6GBqOoFk8LQQ3MpMiQkIkptVm0xHzSh4RSUczf+J39g760a5Xlco0QRnbWXJkbacucDA+523rCty50QcfTx8yU4GgCwMpAArSZz5O6YogD8cyuVJUdcCQveiuMeTaO0h76uyeRTr6PqNvxia6Aijps3Q9MatjgG6VLqHYfE1hgja598UH2hBZnwcCGl9IZm48lreiQ==|
SFTP_PORT: "2222"
CLOUD_PROVIDER: "aws"
---
apiVersion: v1
kind: Secret
metadata:
name: sftpgateway-secrets
namespace: sftpgateway
type: Opaque
stringData:
SPRING_DATASOURCE_PASSWORD: "sftpgw"
SECURITY_CLIENT_SECRET: "1234"
SECURITY_JWT_SECRET: "b03c367c-a16c-4a43-9d47-8ff73462179e"
POSTGRES_PASSWORD: "sftpgw"
---
apiVersion: v1
kind: Secret
metadata:
name: ssl-certs
namespace: sftpgateway
type: Opaque
stringData:
tls.crt: |
-----BEGIN CERTIFICATE-----
MIID4zCCAsugAwIBAgIUd2Q6F9G4dGxIqLd8cS6ltLeDpk4wDQYJKoZIhvcNAQEL
BQAwZDELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcM
DVNhbiBGcmFuY2lzY28xFDASBgNVBAoMC0RldmVsb3BtZW50MRIwEAYDVQQDDAls
b2NhbGhvc3QwHhcNMjQxMTE3MDMwMzE4WhcNMjUxMTE3MDMwMzE4WjBkMQswCQYD
VQQGEwJVUzETMBEGA1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5j
aXNjbzEUMBIGA1UECgwLRGV2ZWxvcG1lbnQxEjAQBgNVBAMMCWxvY2FsaG9zdDCC
ASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALY7NVKDdmGj0FLUY/mBjyvn
KQiF22bNxq56HTIKawjHxV70W+CBzPv2d2wNI4e4vOqTDCKOUbPKKPXX1vNu2u1l
McVQNwxR2xG4zsDj9WzX3Z782F6qmHi+hqsVbFgVdOxj4xjMOTeodwjNL2K4ylMi
Vn13M7Yj1qqPfXVRZgfcSuVmLpIadz5TAif4NhB6SBodg+jjeynGJLkS80kV13W9
bpu1JNcTFEaEB+E0RijdZ2BrUUaOaNF8wOP0Zk50v5t0M9uBfd9O0sDemzxesyWF
+pLANFkEPYiRCdn7epF1qZZer2uqbS15RhFyvfKfkZK0vx4vC/qcDKpI9CPg6t0C
AwEAAaOBjDCBiTAdBgNVHQ4EFgQUc31/aqt6ZE22MrD4JmpNZP8UNZswHwYDVR0j
BBgwFoAUc31/aqt6ZE22MrD4JmpNZP8UNZswDwYDVR0TAQH/BAUwAwEB/zAUBgNV
HREEDTALgglsb2NhbGhvc3QwCwYDVR0PBAQDAgeAMBMGA1UdJQQMMAoGCCsGAQUF
BwMBMA0GCSqGSIb3DQEBCwUAA4IBAQAGtPbCCjw3ckDncp3UD32X9dfDLWZnvXRi
jsZ0kpLu3O1A+AJb7HGdeV7TB13DU6DvlHfPMExI8LPaybiLbAB5yO3pIYueoacc
y6QK3s8AbtubWMROOeICBe6WVh63nzoPk3LjgyDk16Nm84VQequIGGJ3PlXZzXjZ
PVlEEPryg8s6U8iY7z/HHXse4CytMrEB9last5Z3TBgNqTT5Uiqw9zAhb4L6oHwW
zE99hgVx5G5eAVeziPY5Hy1xYY7/G6EXmdpRWI5BbJO4kKN0RFS03b8iGkgiwHvp
24Yi6PfMCT1WSNQ9OEIjsAaQIKJikH1xww46y0oEn/wc2BBCgcOO
-----END CERTIFICATE-----
tls.key: |
-----BEGIN PRIVATE KEY-----
MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQC2OzVSg3Zho9BS
1GP5gY8r5ykIhdtmzcaueh0yCmsIx8Ve9Fvggcz79ndsDSOHuLzqkwwijlGzyij1
19bzbtrtZTHFUDcMUdsRuM7A4/Vs192e/Nheqph4voarFWxYFXTsY+MYzDk3qHcI
zS9iuMpTIlZ9dzO2I9aqj311UWYH3ErlZi6SGnc+UwIn+DYQekgaHYPo43spxiS5
EvNJFdd1vW6btSTXExRGhAfhNEYo3Wdga1FGjmjRfMDj9GZOdL+bdDPbgX3fTtLA
3ps8XrMlhfqSwDRZBD2IkQnZ+3qRdamWXq9rqm0teUYRcr3yn5GStL8eLwv6nAyq
SPQj4OrdAgMBAAECggEAJUl2puhO1fo4o2YhgblUlAFj2EJZaw7iXyuN40IV9hE4
Ta5WyViN2qVq+KE0mq3+e8n0UvLHfW/5UxpjuWI+qhIJbcv0w5DRMC5eIcJTIr8F
siUe2bny4kvrzsBer6ROTRtAKcAJ2h1eo96mGj9g6MNPKrN0EYoCP9qF63YpGCTO
zVpY7fIOxow2AHaiRlEblpRtJHMEL/DdcmxqvCvkREgjwQSWZKAL8Mu4dZKasYBy
+nNV7vIudGmTciRuWJLgLayLXFil7OJME44PIktGlBNL3UgMM/oKCTM0qp8aA9DQ
52dKWk9gI9I6mum+XnBMipQtBSFMyBHEoSb9dUytkQKBgQDonUUiz417NgO0fljE
0GvrqNzk2RrJ50KMcLB6wdJoVx037qLJkHJJUeKsJeOqJfYOQ68PnusucEvSgR5N
/69c1v5UfFASj+mVVtLaEsEEZ+MMSvYhSHq/Dlj4NdKaSkdcCxY8YoMN3fRNUTtY
o3oOQWDn+43uqe1Wabr2TMxUzQKBgQDIjT5jNo9H27bkiXUV2t+a9KmGTu2FNE9F
CtMrSAmpj+lCHPNJzwgP49KfGf+KerkZ/bslixhROXo0HXQ0Eyp+iduNmXKjEX/h
rpj+HekN/cdHyQA64Kc8qHYbN+4VgksXk1hWXovhY99bg2bEtzX9D4mFbmdArGXA
4eMNZfJuUQKBgACfAuM/6KHOmB3wRG5qHA+qCMT3q3Gkk3Hqjx4UzGoI6YQPuBGP
uC5n8JIDG+OFbG3HUn1ZMEmUdS9ftuQAbchyroUtO82A4t/KNo/sguVvHZUX0iZu
mh1OfYBULHbLAfvF785DeRQdZpyaPe1TqmzFUevsqQldHMwhRiWIOPd1AoGAYy6P
Cwvhgj0jzxQ3xm4vJXgYGqcQCk9bYJ7A3mfK94OHbT3aB8eOiiU2dZ6q5TZaMoNs
OV330bumNv3WCSbtXhUZcobPzduKrfbmDM6IAnZeRp8eMQAHVRVPC5j2csa0El25
U0WA0h/NR3nNqj2dQqCbd1SpVa+sxt4vpuGjKnECgYASiNxDdbApD6F153Y56dO1
PM17ujQ+sa0qZH+fdCKweBZ5xHN+I7VYf4zMJ630/7KWy9lwa4N8GWxNNGAEhWav
7xqWNw2UCfb5BzsztIxSL60NSnqCzqvZP7OSboFS9X6lQKQ73bWyAtQuhG5ydALz
0Bz/2SdeU40IbTl/wrpY2g==
-----END PRIVATE KEY-----
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: postgres-pvc
namespace: sftpgateway
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 20Gi
storageClassName: gp2
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: sftpgateway-home-pvc
namespace: sftpgateway
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 10Gi
storageClassName: gp2
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: postgres
namespace: sftpgateway
spec:
replicas: 1
selector:
matchLabels:
app: postgres
template:
metadata:
labels:
app: postgres
spec:
containers:
- name: postgres
image: postgres:16-alpine
ports:
- containerPort: 5432
env:
- name: POSTGRES_DB
value: "sftpgw"
- name: POSTGRES_USER
value: "sftpgw"
- name: POSTGRES_PASSWORD
valueFrom:
secretKeyRef:
name: sftpgateway-secrets
key: POSTGRES_PASSWORD
- name: PGDATA
value: "/var/lib/postgresql/data/pgdata"
- name: POSTGRES_INITDB_ARGS
value: "--data-checksums"
volumeMounts:
- name: postgres-storage
mountPath: /var/lib/postgresql/data
livenessProbe:
exec:
command:
- pg_isready
- -U
- sftpgw
- -d
- sftpgw
initialDelaySeconds: 30
timeoutSeconds: 5
readinessProbe:
exec:
command:
- pg_isready
- -U
- sftpgw
- -d
- sftpgw
initialDelaySeconds: 5
timeoutSeconds: 1
volumes:
- name: postgres-storage
persistentVolumeClaim:
claimName: postgres-pvc
---
apiVersion: v1
kind: Service
metadata:
name: postgres-service
namespace: sftpgateway
spec:
selector:
app: postgres
ports:
- protocol: TCP
port: 5432
targetPort: 5432
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: backend
namespace: sftpgateway
spec:
replicas: 1
selector:
matchLabels:
app: backend
template:
metadata:
labels:
app: backend
spec:
containers:
- name: backend
image: [Sign up for our Beta program to get the backend ECR image]
ports:
- containerPort: 8080
- containerPort: 2222
envFrom:
- configMapRef:
name: sftpgateway-config
env:
- name: SPRING_DATASOURCE_PASSWORD
valueFrom:
secretKeyRef:
name: sftpgateway-secrets
key: SPRING_DATASOURCE_PASSWORD
- name: SECURITY_CLIENT_SECRET
valueFrom:
secretKeyRef:
name: sftpgateway-secrets
key: SECURITY_CLIENT_SECRET
- name: SECURITY_JWT_SECRET
valueFrom:
secretKeyRef:
name: sftpgateway-secrets
key: SECURITY_JWT_SECRET
volumeMounts:
- name: sftpgateway-home
mountPath: /home/sftpgw
workingDir: /opt/sftpgw
securityContext:
runAsUser: 1000
runAsGroup: 1000
resources:
requests:
memory: "2Gi"
cpu: "1000m"
limits:
memory: "4Gi"
cpu: "1500m"
livenessProbe:
httpGet:
path: /actuator/health
port: 8080
initialDelaySeconds: 120
periodSeconds: 10
readinessProbe:
httpGet:
path: /actuator/health
port: 8080
initialDelaySeconds: 90
periodSeconds: 5
volumes:
- name: sftpgateway-home
persistentVolumeClaim:
claimName: sftpgateway-home-pvc
---
apiVersion: v1
kind: Service
metadata:
name: backend-service
namespace: sftpgateway
spec:
selector:
app: backend
ports:
- name: http
protocol: TCP
port: 8080
targetPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: sftp-service
namespace: sftpgateway
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
service.beta.kubernetes.io/aws-load-balancer-cross-zone-load-balancing-enabled: "true"
service.beta.kubernetes.io/aws-load-balancer-scheme: "internet-facing"
service.beta.kubernetes.io/aws-load-balancer-source-ranges: "0.0.0.0/0"
spec:
type: LoadBalancer
selector:
app: backend
ports:
- name: sftp
protocol: TCP
port: 22
targetPort: 2222
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: frontend
namespace: sftpgateway
spec:
replicas: 2
selector:
matchLabels:
app: frontend
template:
metadata:
labels:
app: frontend
spec:
containers:
- name: frontend
image: [Sign up for our Beta program to get the frontend ECR image]
ports:
- containerPort: 80
- containerPort: 443
envFrom:
- configMapRef:
name: sftpgateway-config
env:
- name: SECURITY_CLIENT_SECRET
valueFrom:
secretKeyRef:
name: sftpgateway-secrets
key: SECURITY_CLIENT_SECRET
- name: WEBSITE_BUNDLE_CRT
valueFrom:
secretKeyRef:
name: ssl-certs
key: tls.crt
- name: WEBSITE_KEY
valueFrom:
secretKeyRef:
name: ssl-certs
key: tls.key
resources:
requests:
memory: "128Mi"
cpu: "100m"
limits:
memory: "256Mi"
cpu: "200m"
livenessProbe:
httpGet:
path: /
port: 80
initialDelaySeconds: 30
periodSeconds: 10
readinessProbe:
httpGet:
path: /
port: 80
initialDelaySeconds: 10
periodSeconds: 5
---
apiVersion: v1
kind: Service
metadata:
name: frontend-service
namespace: sftpgateway
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
service.beta.kubernetes.io/aws-load-balancer-cross-zone-load-balancing-enabled: "true"
service.beta.kubernetes.io/aws-load-balancer-scheme: "internet-facing"
service.beta.kubernetes.io/aws-load-balancer-source-ranges: "0.0.0.0/0"
spec:
type: LoadBalancer
selector:
app: frontend
ports:
- name: http
protocol: TCP
port: 80
targetPort: 80
- name: https
protocol: TCP
port: 443
targetPort: 443